Today i wanna share you some point about CCIE RS .
As a reliable transmission protocol, TCP's core goal is to transmit the data of the application layer correctly, reliably and efficiently to the peer. The IP network that TCP relies on is a primitive jungle world, with packet loss, out of order, and delay. fixed.
TCP has a twin brother called UDP, UDP is a big old, but very obedient. UDP in the IP network jungle, strictly enforce the purpose of its own owner (application layer), the master will send 1000 / sec UDP packets, UDP will certainly send so much, perhaps the 1000 packets eventually reach the destination of only 200 The other 800 disappeared into the jungle world without a trace.
TCP is an elegant gentleman who is very disgusted with the hidden rules of the jungle world but has a strong adaptability and can cope with all challenges. TCP also received instructions from the boss: send 1000 packets to the destination within 1 second!
TCP euphemistically expresses its own ideas and can be sent to the destination accurately, but time is not guaranteed!
TCP always likes to make appointments. Whenever you need to visit the other party, you will always say hello (establish a connection). Only when the other party is in and accept the appointment (connection establishment) will you bring the boss's data packet to visit the other party.
TCP does this:
Send a packet first, and wait for a packet to be acknowledged, you can get a round trip time RTT
Send two, receive confirmation, get the second RTT, add the average SRTT with the first one
...
It has been exponentially increasing twice and has been calculating SRTT.
Until a packet loss is detected, or the retransmission timer expires, or at least three duplicated ACKs are received,
1.TCP decides to send the number of indexes in the SRTT time to be halved
2. If an ACK is received, the SRTT is continuously calculated, the number of transmissions increases linearly, and one SRTT sends one more packet.
3. If you still have not received the ACK, repeat steps 1, 2
This is TCP's adaptive flow control algorithm, which determines how fast TCP can be sent. This formula yields:
Delivery Rate = CWND/SRTT, where
CWND = number of packets that can be sent the * size of the package
SRTT is a smooth RTT, the result of dynamic measurements
If the SRTT is unchanged, the larger the CWND, the faster the transmission rate.
If the CWND is unchanged, the smaller the SRTT, the faster the transmission rate.
But once the network is congested, the router cache queue makes the SRTT larger, so the rate will become smaller.
If the buffer queue is dropped (overflow), it means that there is a packet loss, the sender can definitely detect it, and the exponent decreases CWND, so the rate will also drop by 1/2.
TCP uses this small rate to detect network congestion, exponentially increase the transmission speed, detect packet loss, halve the transmission rate, until packet loss is no longer detected, linearly increase the transmission rate, detect packet loss, and reduce the transmission rate again. ...
The key to the TCP flow control algorithm is based on packet loss. Whether or not the packet is lost is the only basis for judging whether it is a throttle or a break.
However, TCP is very one-sided because it knows about the network.
1) The network is really congested and lost
2) The line quality is poor, CRC check fails, or signal interference is lost.
3) Misjudgment caused by out of order of IP packets
Only case 1 requires braking, and situations 2 and 3 are not required.
The Google BBR algorithm proposes an algorithm based on bandwidth real-time measurement. It measures the RTT for each TCP packet with data and dynamically calculates the SRTT, which is more accurate than the traditional TCP-based SRTT because the traditional TCP is measured within an SRTT time period. Once, not every TCP packet with data is measured.
According to the trend of the real-time bandwidth value, whether it is increasing or decreasing. If it increases, it indicates that there is space in the bandwidth. It can be optimistic. On the basis of the current delivery rate, * a coefficient greater than 1, equal to adding a small throttle, and the transmission rate is rising.
If it is subtracted, you need to be cautious. Based on the current delivery rate, the coefficient is less than 1, equal to the small break, and the transmission rate is slow.
The BBR algorithm does not rely on packet loss. It can overcome the excessive sensitivity and excessive response of traditional TCP to packet loss, avoiding the sudden increase and decrease of the transmission rate, so that the overall transmission rate fluctuates within a small range, which is more gradual and smoother.
This is an improvement of the traditional TCP flow control algorithm.
As for other TCP improvements, it has been patched through TCP option, such as
Scaling window
Selective ACK responds to high packet loss scenarios
The timestamp should handle the accuracy of serial number rollback and RTT measurement
Authentication Option addresses data integrity challenges
TCP Cookie should respond to SYN Flooding DOS attacks
FAST TCP Open should deal with TCP transmission data delay
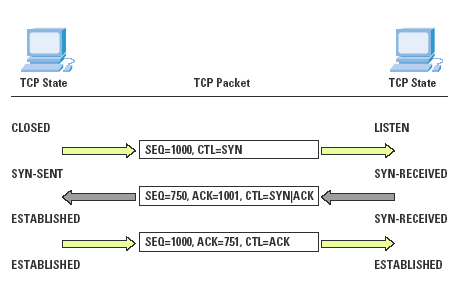
TCP uses a three-way handshake mechanism to establish a connection. The first message of the handshake is an SYN packet. The second message is an SYN/ACK packet, indicating that it responds to the first SYN packet while continuing the handshake. The third report The text is just a response expressed as an ACK packet. If A is placed as a connection, B is the responder, and the possible threats are:
1. The attacker listens for SYN/ACK packets sent by Party B.
2. The attacker sends the RST packet to the party, then sends the SYN packet, and the fake A party initiates a new connection.
3. Party B responds to the new connection and sends a connection response message SYN/ACK.
4. The attacker then impersonates the A party to send an ACK packet to the B party.
In this way, the attacker achieves the function of destroying the connection. If the attacker then takes the opportunity to insert harmful data packets, the consequences are more serious. The TCP protocol treats data transmitted over a connection as a byte stream, numbering the transmitted bytes with a 32-bit integer. The initial sequence number (ISN) is generated during the TCP handshake, and the generation mechanism is related to the protocol implementation. The attacker only needs to send a connection request to the target host to obtain the last connected ISN, and then pass the measurement path back and forth through multiple measurements to obtain the round-trip time RTT of the packet transmission between the attacking host and the target host. Knowing the last connected ISN and RTT, it is easy to predict the next connected ISN. If an attacker spoofs a trusted host to make a TCP connection to the target host and predicts the TCP serial number of the target host, the attacker can spoof the harmful data packet and accept it by the target host.
The IP protocol provides connectionless packet transmission between interconnected networks. The IP protocol sends an IP packet based on the destination address entry in the IP header. That is to say, when the IP route IP packet, the source address provided in the IP header is not checked, and the source address in the IP header is considered as the IP of the machine that sent the packet.
address. In this way, many services that rely on IP source addresses for acknowledgment will cause problems and will be hacked. The most important of these is the use of various attacks caused by IP spoofing.
Take a firewall as an example. Some network firewalls only allow IP packets that the network trusts to pass. However, since the IP address does not detect whether the IP source address in the IP packet is the real address of the source host that delivers the packet, the attacker can use IP source address spoofing to bypass the firewall. In addition, there are some network applications that use IP addresses as the basis for security rights allocation. It is easy for an attacker to obtain privilege by using IP source address spoofing, thereby causing serious damage to the attacker. In fact, every attacker can use IP to not check the characteristics of the IP header source address, and fill in the fake IP address to attack, so that they are not discovered.
We have CCNA Wikipedia Encyclopedia, you can contact us if you are interested.

 Join Telegram Study Group ▷
Join Telegram Study Group ▷