Sometimes your data center will have L2 domain (Bridge Domains-BD), that will be used with hardware devices such as F5 NLB, or similar to other firewalls, WAF, or similar devices. This is where ACI does not route or bridge, but the only L3 point that exits from this segment will be located on the actual hardware device outside the ACI Fabric-connected to the Leaf port.
We will present an example here and use it throughout the article, where BIGIPF5NLB is used as L3 terminal for L2BD 10.10.10.0/24.
The route directly connected to the ACI Leaf,10.10.10.0/24 subnet (L2 BD) is completed directly on the F5 device, which is the default gateway for the subnet endpoint.
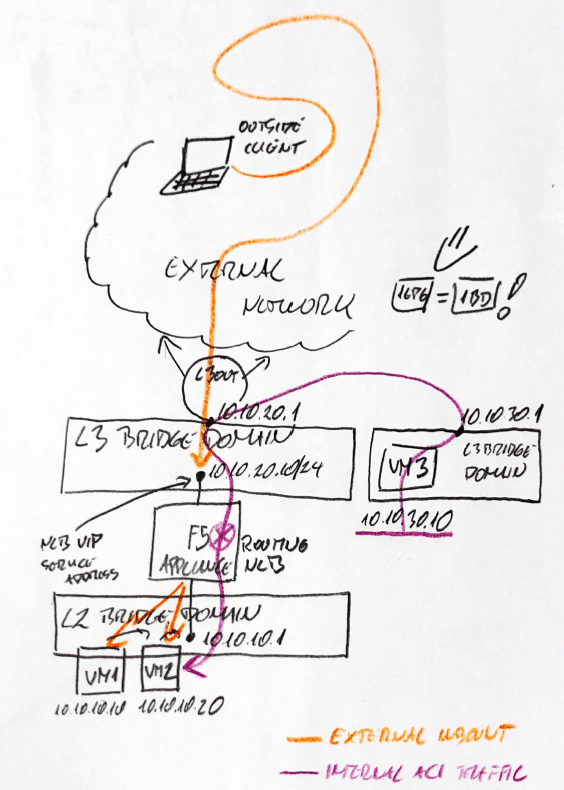
In certain implementations, when you decide not to use PBR or service diagram, devices such as F5 will appear on L3 terminals of some ACIL2BD, as shown in Figure 10.10.10.0/24.
When devices such as F5 NLB become the default gateway for some L2 BD, you need to enable flooding in the database because you need to flood on all BD with external devices mapped to them (for ARP packets from external devices to VM and ARP)-Versa).
IP unicast routing can be disabled on this BD because there is no L 3 point in ACI (the possibility of not configuring subnet), ACI for "smart" bridge and traffic routing on BD will be lost. ACI does not learn the IP address of the endpoint (VM) in the bridge domain, nor does it do more for the traffic than a normal L2 switch. He will only know the MAC address and bridge the traffic to the F5 interface, which will respond to the ARP. when an endpoint sends an ARP request for the default gateway.
THE ORANGE TRAFFIC FLOW
On the other hand, when your data center has an L3OUT connection to the outside world (in order to be able to receive traffic from the Internet or a client somewhere), you can advertise outside through L3OUT in the case of all ACI learning subnets (ACI data center network segments or BD).
On the other hand, the endpoints in the L2 BD segment (such as the VM in the L2 BD behind the F5 NLB device in our example subnet 10.10.10.0 ≤ 24) will not be learned by ACI, and even if we configure the DB, they will not advertise outside the external advertisement (because ACI does not know that there are some IPv4 or IPv6 addresses in the BD).
For our L3 BD (F5-OUT 10.10. 20.0/24) NLB external interface IP (SelfIP or VIP IP), ACI will know that they exist and can route them from any point in the ACI data center
If we configure the F5 device to load balance some services running on the VM in L2 BD (VM 10.10.10.10 and 10.10.10.20), the service will be used as a VIP address on the VIP address of the 10.10.20.0 ≤ 24 subnets. If configured for L3L, it will arrive from the ACI structure and be notified outside the ACI.
We are talking about orange traffic flow from the image above in case you are wondering.
Note: if you are interested in the method to Advertise a Route from ACI Layer2 BD Outside the Fabric, and you can contact us to get more information.
THE PURPLE TRAFFIC FLOW
When the administrator requests direct access to the same VMs behind the NLB for administrative operations, they will want to access these VMs through their own IP rather than the VIP address on the NLB (the VIP address on the NLB receives the traffic on some services and the VM behind the load-balancing server pool with more traffic). One of the reasons may be that by accessing the VIP, you do not determine which VM will eventually be used.
" Okay okay, you can control that on NLB device but we need direct access to VMs for administrative reasons to work all the time without the need to touch NLB config every time".
From an ACI point of view, the traffic of IP addresses such as 10.10.10.10 and 10.10.10.20 inside L2 BD will come from these virtual machines, because when someone requests (ARP requests) these addresses, the F5 device will respond using the IP address of the external interface. All IP from the BD 10.10.10.0 / 24 endpoint will be seen by ACI on the F5 external interface and will be displayed in L3 BD 10.10.20.0 / 24
F5 needs to be additionally configured as a forwarder in order to enable any IP traffic to get to those VMs by acting as a router and not load balancer.
ADVERTISE ROUTES TO THOSE ENDPOINTS OUTSIDE ACI
The thing is, those IPs are only learned and known inside ACI and are not advertised outside 10.10.20.0/24 BD even when that BD has “Advertise Externally“ routing setting enabled.
we have an option to resolve this problem by generating a host route representing f5 inside the EPG that will use the IP address of these endpoints (and then define the appropriate next hop to the nlb device external interface) to advertise outside the aci data center, Thereby effectively enabling inbound traffic to obtain information about the sending traffic in order to access the related virtual machines (10.10. 10.10 and.20).
When configuring host routes to those endpoints (in L2BD-F5IN) we need to configure host routes under outside EPG (L3BD-F5OUT).
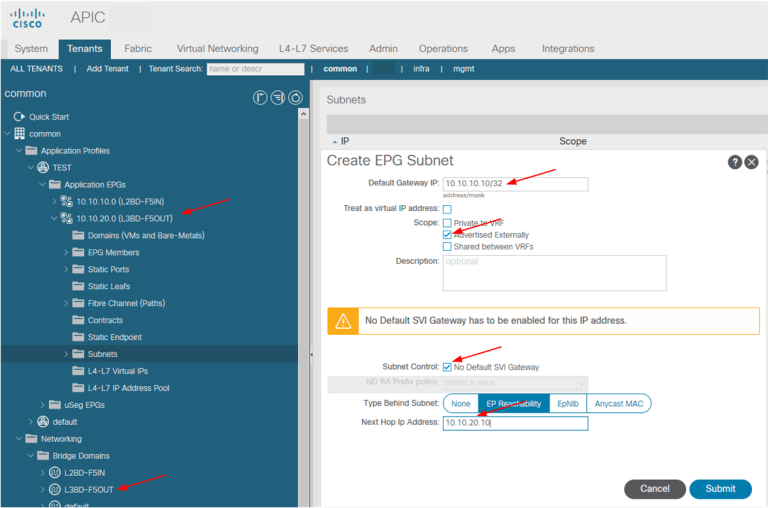
In this case, similar to the above example, host routing is generated and notified from the L 3 BD outside the ACI. This route will inform the external client that 10.10.10.10 IP exists in the ACI and can be reached by sending traffic to the L3 BD IP address 10.10.20.10 (actually F5 outside the interface IP). F5 will receive the traffic and be able to route it to the final destination 10.10.10.10
About SPOTO
SPOTO offers Cisco CCIE certification practice tests and training to help all candidates to pursue their ideal careers. You can also find more useful tips and suggestions to help you study and master networking knowledge.

 Join Telegram Study Group ▷
Join Telegram Study Group ▷














