What is a VPN?
The Virtual Private Network (VPN) is designed to provide users with dedicated network capabilities through a shared infrastructure. They connect to the remote site and provide the same privacy level as the private network. An IP security (ipsec) VPN provides data confidentiality by using encryption, by using the authenticity of the message authentication, by the data integrity of the hash algorithm, and by using an anti-replay of the verified serial number. IPSec VPNs are commonly used for Hub-Spoke designs where the number of links is equal to n-1. However, in the full mesh topology, the number of links is greatly increased, according to formula n * (n-1)/2. The customer routers are peer-to-peer with each other, so adding a new VPN site requires that configuration changes be made on all existing sites. Obviously, the problem of scalability is the major drawback of the IPSec VPN, as the configuration overhead is dramatically increased for a large number of sites.
Benefits of BGP / MPLS Layer 3 VPN
When supporting complex topologies, BGP / MPLS layer 3 VPN represents an alternative to IPSec VPN. They solve the scalability problem of traditional IPSec VPN deployed in the full mesh model and reduce the configuration overhead when connecting multiple sites. Adding a new site to the VPN requires a change on the provider edge (PE) device that connects to the customer router. The customer edge (CE) router uses IGP or eBGP to peer with the service providers PE router and exchanges layer 3 routing information with the PE router. However, CE routers are not VPN aware. A VPN, RFC 4760.MP-BGP is formed between RFC routers running BGP-4 Multiprotocol extension (MP-BGP) to assign customer prefixes to the providers' network. Customer data is switched in the service providers multi-protocol label switching (MPLS) network based on tags. Traffic passes through a predetermined label switching path (LSP), which is a one-way tunnel between a pair of PE routers.
Note: The combination of VRF, MPLS, and MP-BGP ensures that traffic from one VPN does not leak to another VPN and that the same private IP address (RFC 1918) space is available for VPN sites.
Using MPLS to forward packets in the providers' backbone network brings another benefit in the form of traffic engineering (TE). Customer traffic can be moved through underutilized paths in the providers MPLS network, or priority can be determined according to the service. Because the non-congestion path with high delay in TE is better than that with lower delay. Classic IGP, such as OSPF, uses non-TE routing. In the case of OSPF, the cost of each link is used as a measure of the SPF algorithm to find the shortest path. In this case, the best path through the service provider core may be widely used, while other redundant paths will not be fully utilized. Changing costs may help, but it may affect the entire network at the same time.
BGP / MPLS Tier 3 VPN Infrastructure
Figure 1 shows the BGP/MPLS Layer 3 VPN infrastructure. This article further explains the functionality of each device in the network.
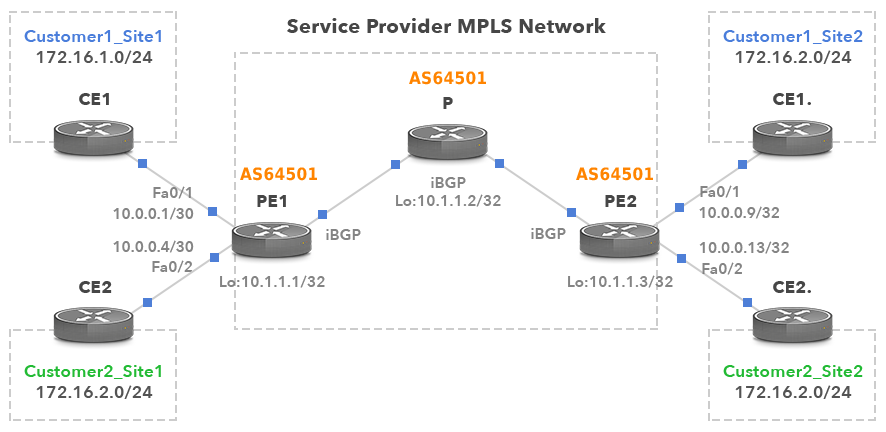
The Customer Edge (CE) router is located at the edge of the customer site, typically owned by the customer. The customer router advertises the route to the PE router through the routing protocol. The PE router installs the received route in the VRF with the appropriate VPN MPLS label.
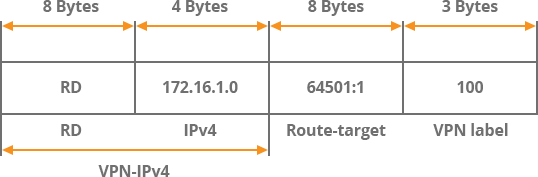
The provider edge (PE) router is located on the edge of the provider network and connects one or more CE routers. Multiple forwarding routing tables, also known as VPN routing and forwarding table (VRF)., run on PE routers at each site Customer-oriented interface assigned to VRF, each site is configured with its own VRF. PE routers assign routing identifiers (RD) to each VRF, form as or: Add an 8-byte RD, PE router to convert customer routing to a 12-byte VPN-IPv4 (also known as VPNv4) address. This ensures that the customers' prefix is unique in the providers' network, even if the customer uses overlapping private addresses.
In the following configuration example, two customers connect to the PE router. The service provider has defined two VRF instances, one for each customer. The provider uses BGP AS number 64501. Route-target specifies how to import and export routes from VRF. For example, PE1 leads the way out of VRF Customer1 by 172.16.1.0 / 24 and allocates it to route-target 64501 / 1. Router PE2 installs this route into VRF Customer1 because it is configured with RT 64501 / 1 (not shown). Keywords refer to both import and export routes from/to VRF. Therefore, router PE1 leads the way out from VRF Customer2 to 172.16.2.0 / 24 and allocates a routing target of 64501 / 2 to it. Router PE2 then installs route 172.16.2.0 / 24 into VRF Customer2 because it has been configured with RT 64501 / 2.
PE1(config)# IP vrf Customer1
PE1(config-vrf)# rd 64501:1
PE1(config-vrf)# route-target both 64501:1
PE1(config-vrf)# IP vrf Customer2
PE1(config-vrf)# rd 64501:2
PE1(config-vrf)# route-target both 64501:2
Note: VPN-IPv4 addresses are used only in the provider’s network. Translation from IP to VPN-IPv4 occurs only on the PE router. PE routers maintain the VPN routes, however, they only need to know routes for VPNs that have the attached sites.
The commands below assign customer-facing interfaces on PE1 router to particular VRFs.
PE1(config)# interface f0/1
PE1(config-if)# ip vrf forwarding Customer1
PE1(config-if)# IP address 10.0.0.1 255.255.255.252
PE1(config-if)# interface f0/2
PE1(config-if)# ip vrf forwarding Customer2
PE1(config-if)# IP address 10.0.0.5 255.255.255.252
PE router marks the VPN-IPv4 routes with extended community and advertises them via MP-BGP. Multiprotocol BGP allows BGP to support address families other than IPv4 such as VPN-IPv4. All PE routers receive routes via BGP and they filter them based on the VPN extended community.
PE1(config)# router BGP 64501
PE1(config-router)# neighbor 10.1.1.3 remote-as 64501
PE1(config-router)# neighbor 10.1.1.3 update-source loopback 0
PE1(config-router)# address-family vpnv4
PE1(config-router-af)# neighbor 10.1.1.3 activate
The Ingress PE1 router is the label edge router (LER), used to push the VPN label to the MPLS header for customer traffic. VPN tags are internal tags that are not affected by P routers. This label is used to identify the correct next hop on the remote PE router. In other words, PE routers use VPN tags to direct packets to the correct CE device. Remote PE routers receive packets containing VPN tags, perform tag pop-up, and forward customer traffic to the correct CE router
Note: VPN-IPv4 routing, together with inner VPN tags and routing targets, is distributed by MP-BGP between PE routers. Learn external LSP tags through LDP (Label Distribution Protocol).
In addition to the internal VPN label, the PE router uses an external LSP (label switched path) label to stack IP packets. The LSP label has only local significance and is exchanged with the new label over each p router on the path. The last p router is the reciprocal second router of the lsps. It performs the pop-up of the LSP label and switches the customer traffic to the PE router using only the internal (VPN) label.
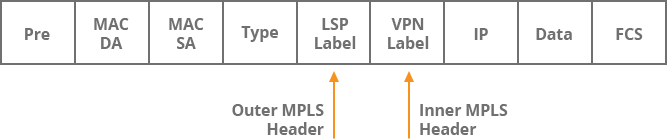
The provider (P) router is the label switching router (LSR) because it is not connected to any CE router. P routers do not contain VPNv4 routes, but only routes to other P and PE routers. The P router only checks the top (external) LSP tag and exchanges the external label with the new LSP tag before forwarding the packet. The content of the LSP header is used to forward packets, which avoids the longest prefix matching of IP on each P router.
Note: To establish BGP adjoining, PE and P routers run IGP, such as OSPF. within the provider network
Conclusion:
BGP / MPLS VPN usually appears in an enterprise environment. They are configured by the service provider and do not require VPN related configurations on the customer router. BGP / MPLS VPN can be easily used to provide a full mesh network architecture. Instead of relying on encryption algorithms, privacy is achieved by defining a single path in the providers' network. Routing separation is achieved by assigning the client router to a separate VRF on the PE router. Customer address separation is achieved by creating a unique VPNv4 route. These mechanisms are implemented through the integration of MP-BGP and MPLS technology, which allows users to maintain the separation of traffic from multiple subscriber networks when switching traffic through a single shared core.
About SPOTO:
SPOTO focus on online IT Certification training for 16 years. SPOTO offers 100% real and valid Cisco CCNA, CCNP, CCIE, ISC, Amazon AWS, Microsoft, and other IT exam practice tests. And we have many free online training courses of Cisco exam on YouTube. You can find many useful and helpful tips and suggestions. If you’re still worried about to prepare and pass the Cisco exam, try SPOTO now. SPOTO tutors will help you get the CCIE number at the first try.

 Join Telegram Study Group ▷
Join Telegram Study Group ▷