How to compare MPLS vs IPSec VPN WAN Services?
MPLS vs Internet VPN, Which represents the better option and why?
In the early 2000s, IPSec-based VPN was the default service provider product available in the telecommunications market.
In essence, IPSec-based WANs enables enterprises to leverage a single public IP backbone(or more extensive Internet)by encrypting data between office sites and remote users.
The underlying platform is suitable for the smallest business of the smallest multinational organization. However, a new acronym undermines the industry, a competitor called MPLS.
We have previously written an article on the evolution of MPLS and VPLS from SPOTO, but it is sufficient to say that the agreement provides the carrier with the ability to flow engineering internal networks, making it possible to use their infrastructure and bandwidth (as well as other benefits). View this article for more information. With this interesting information, business interests surround some of the unique selling points, opening up the possibility of doing more through the wide area network. Letundefineds talk about why your organization may choose a technology, not another technology, and why the mix of both services is normal.
Below: As part of IT Manager Mindmap (part of the buyers' undefined package), we will help you make purchase decisions without the need for a heavy white paper.

The Internet vs Public IP
There is an obvious difference-not all IPSec VPN services are the same. The difference is whether your organization configure WAN services through a single IP backbone or a mix of multiple service providers.
Fig 1 shows the potential latency impact of using multiple ISP connections.
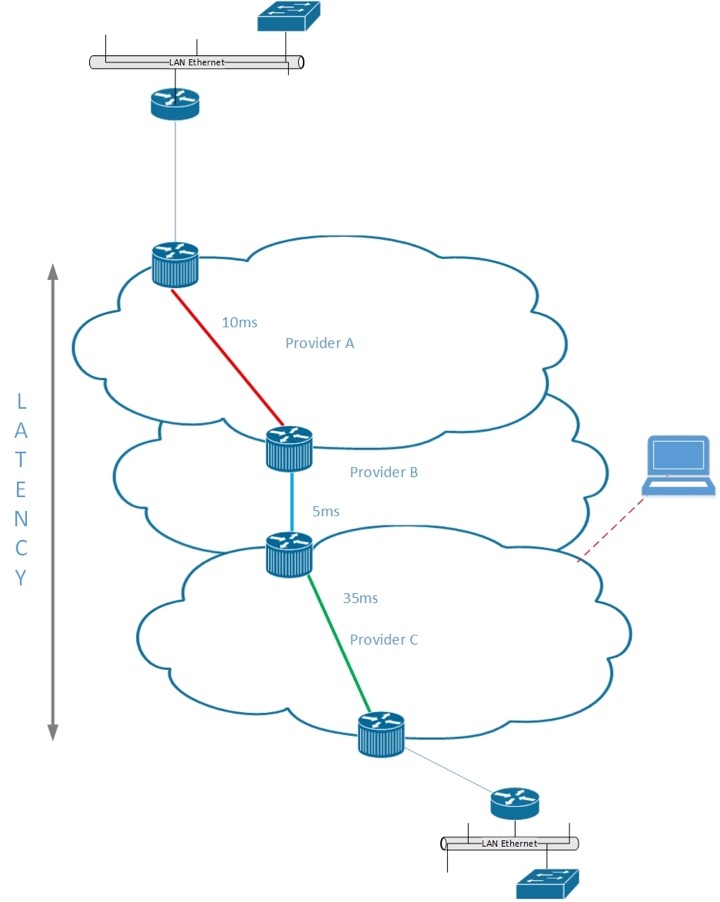
The preference is always to provide an IPSec VPN on a single backbone. Performance levels are more predictable when traffic traverses a single service provider, providing assurance from traffic throughput to latency and support for repair time. In contrast, sending traffic traversing multiple networks is unpredictable, resulting in application performance problems.
Comparing MPLS vs IPSec VPN
MPLS VPN
Private network
Connectionless any to any topology
Support for QoS (Quality of Service)
Granular per application service levels
Support for jitter, important for voice and data
End to end separation of traffic
IPSec VPN
Although it is recommended that a single backbone be used, any Internet service connection should be used with all available connections from the home broadband circuit to the full 1-Gbps Ethernet-providing connectivity, you can start the implementation quickly and easily Access to the wide array of product public cloud-based products
Split tunneling allows access to both Internet and VPN across a single circuit
With the above in mind, the reasons for the explosive growth of MPLS services is clear.
1. Security
The privacy of the MPLS VPN means that you do not need to encrypt your traffic unless you need to increase security. The addition of encryption to MPLS is mainly in financial and government institutions, where the greatest possible security is always the most important. As a default, most English and global businesses believe that MPLS VPN security is acceptable because each service provider customer maintains traffic routing through the VRF table, respectively.
IPSec is basically designed to create a secure tunnel over a public Internet connection. There are several key elements to pay attention to when configuring Internet VPN. The first surround encryption. The current encryption level supported by security services such as AES means that your data is essentially secure. Tutorials on IPSec are beyond the scope of this article, but the following IPSec Wiki articles will help. IPSec will run in VPN only mode, which means that any traffic other than the authenticated endpoint will be discarded. Another option is to separate the tunnel model, which allows companies to benefit from secure tunnels and local Internet access. shortcomings? You need a firewall. Does your IT team think IPSec is safe enough to accept advice
2. Topology
One of the key raw selling points of MPLS WAN encloses any connectionless topology. The ability of each site to communicate with each other is a fundamental transformation with traditional technologies such as Frame Relay Center and Branch Deployment. On the other hand, IPSecWAN can support any topology at the expense of processing capability. As the number of sites increases, the processor requires additional hits, where each new location requires a tunnel to each other site creation cost. In this regard, IPSec VPN is not scalable than MPLS network architecture.
3. MPLS Application Priority - QoS (Quality of Service)
When MPLS enters the market, marketing will convince us that QoS (quality of service) will be the solution to all application performance problems. In short, QoS allows enterprises to protect their key applications, such as voice, video, and Citrix (as examples). To help IT managers associate the functionality of QoS with business advantages, most SLA reflects the delay, jitter, and throughput of each QoS setting. At the time of writing, QoS is still an important aspect of a wide area network, but for high bandwidth Ethernet services, it has become a selling point to avoid congestion problems. With this, bandwidth is only part of the story, because using QoS enables us to predict and ensure performance. All organizations will have different experiences, some of which report that Ethernet ISP bandwidth provides enough performance, while others say QoS is a magical network enhancement.
IPSec VPN usually does not allow the quality of service. As with everything in life, there are always exceptions. This Cisco article explains how to implement QoS. in IPSec WAN deployment But-I didn't undefined personally see the public VPN. using QoS over IPSec. With this in mind, general service provider implementation will not give priority to your application, which means that a certain degree of trust is required when configuring services such as voice and video. In most tier1 ISP networks, we have some confidence in the performance of delay-sensitive applications in national VPN deployment. In global space, it may be difficult to deploy international IPSec VPN without using multiple provider backbone (as we mentioned at the beginning of this article) unless your application performance does not require a certain level of performance. For mission-critical voice, video, and business applications, enterprise businesses do not trust any technology other than private QoS-based VPN.
4. SLA (Service Level Agreements)
Our discussion of the SLA is led out of point 3-QoS. The key basic difference between public-based VPN and private WAN is to ensure performance and repair time. From the point of view of service provider traffic use, private-based MPLS networks are easier to predict. Therefore, it is considered that the core network is more suitable for current and future capacity. Performance SLAs can cover latency and jitter globally when combined with end-to-end application quality of service. Public VPNs typically provide a level of delay service between global locations, but these levels are the average between regions and non-urban areas. The repair time of IPSec VPN and MPLS is similar in many respects, and each service provider provides flexible functionality. When multiple ISPs are used, the SLA will vary depending on the provider undefined capabilities.
5. Cloud-based services
One of the biggest advantages of public VPN is the acquisition of large-scale growth of cloud-based production services. If you read MPLS, recently, you may be surprised by blog posts that indicate that the product is dead. To some extent, this is due to the growth of cloud services, which are not widely available through closed private VPN services. It is true that some MPLS service providers are offering cloud services, but these products are limited compared to the wider Internet. As organizations are eager to gain a competitive advantage from new applications and improve user productivity, the cloud is creating a recovery in the Internet and public WAN services. Voice, video, collaboration, customer relationship management, storage, backup and so on can get a lower monthly OPEX cost. The challenge for enterprises is to adopt the cloud while maintaining a specific level of performance for intersite applications. Because IPSec usually runs in tunnel-only mode (that is, there is no separate tunnel), the tunnel will need to be terminated within the cloud provider undefined infrastructure. This way of working is very common, and most cloud services support it.
6. The Hybrid WAN outcome
With technologies such as SDN (Software-Defined Networking), hybrid VPNs are now a hot topic in the industry. The hybrid feature allows an enterprise to purchase a single circuit (or multiple circuits) into a hybrid WAN vendor network and to access MPLS, the Internet, point-to-point/ multi-point, and so on. IPSec is still the reason for traditional VPN methods, to a large extent because it is able to terminate a connection through a low-cost circuit, including a fast-start solution. And, as we have discussed, the benefits of private-based MPLS features are also obvious.
The hybrid solution allows organizations to take advantage of a variety of connection types from one provider and one hardware device, including ADSL broadband, 3G, and 4G. Although the MPLS vs VPN (IPSec) challenge has always been a discussion point, the market is moving forward, providing the advantage of having the best of both worlds in the form of a hybrid connection.

 Join Telegram Study Group ▷
Join Telegram Study Group ▷














