SPAN and RSPAN are the most important part of the CCIE RS Lab exam, and SPOTO will introduce some basic knowledge. Recently, some candidates consider SPAN and RSPAN are difficult to pass, but SPOTO’s candidates have passed these parts of CCIE RS Lab exam easily. The following is the introduction to SPAN and RSPAN.
Note: To use RSPAN, the switch must be running the LAN Base image.
This article describes how to configure a switch port analyzer (SPAN) and a remote SPAN (RSPAN) on the Catalyst 2960 and 2960-S switches. Unless otherwise specified, the term "switch" refers to a separate switch and a switch stack.
Note: Stacking is supported only on Catalyst 2960-S switches running the LAN base image.
For complete syntax and usage information for commands used in this chapter, see the command reference for this release
This chapter consists of these sections:
Understanding SPAN and RSPAN
You can use SPAN or RSPAN to analyze network traffic over ports or VLAN to send a copy of the traffic to another port on the switch or to another switch that is connected to a network analyzer or other monitoring or security device. SPAN copies (or mirrors) traffic received or sent (or both) on the source port or source VLAN to the target port for analysis. SPAN does not affect network traffic switching on source ports or VLAN. You must dedicate the target port to SPAN. The destination port does not receive or forward traffic except for traffic required for SPAN or RSPAN sessions.
Only traffic entering or leaving the source port or entering or leaving the source VLAN can be monitored through SPAN; traffic routed to the source VLAN cannot be monitored. For example, if you are monitoring incoming traffic, you cannot monitor traffic routing from another VLAN to the source VLAN; however, you can monitor traffic that receives and routes to another VLAN on the source VLAN.
You can use SPAN or RSPAN target ports to inject traffic from network security devices. For example, if an (IDS) sensor device of the Cisco intrusion detection system is connected to the target port, the IDS device can send a TCP reset packet to close the TCP session of the suspected attack.
These sections contain this conceptual information:
Local SPAN
Remote SPAN
SPAN and RSPAN Concepts and Terminology
SPAN and RSPAN Interaction with Other Features
Local SPAN
Local SPAN fully supports the SPAN session in one switch; all source ports or source and destination ports are in the same switch or switch stack. Local SPAN copies traffic from one or more source ports in any VLAN or from one or more VLANs to the destination port for analysis. For example, in Figure 1-1, all traffic on port 5 (source port) is mirrored to port 10 (destination port). The network analyzer on port 10 receives all network traffic from port 5 instead of being physically connected to port 5.
Figure 1-1 Example of Local SPAN Configuration on a Single Switch
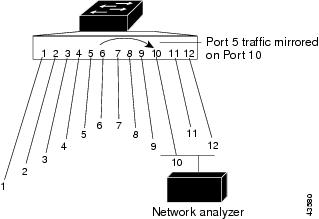
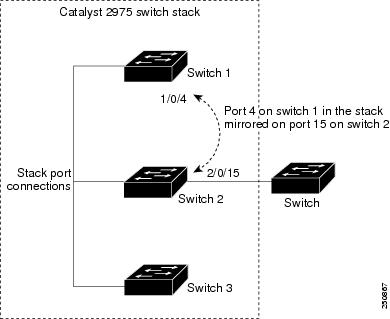
Figure 1-2 is an example of a local SPAN in a switch stack, where the source and destination ports reside on different stack members.
Figure 1-2 Example of Local SPAN Configuration on a Switch Stack
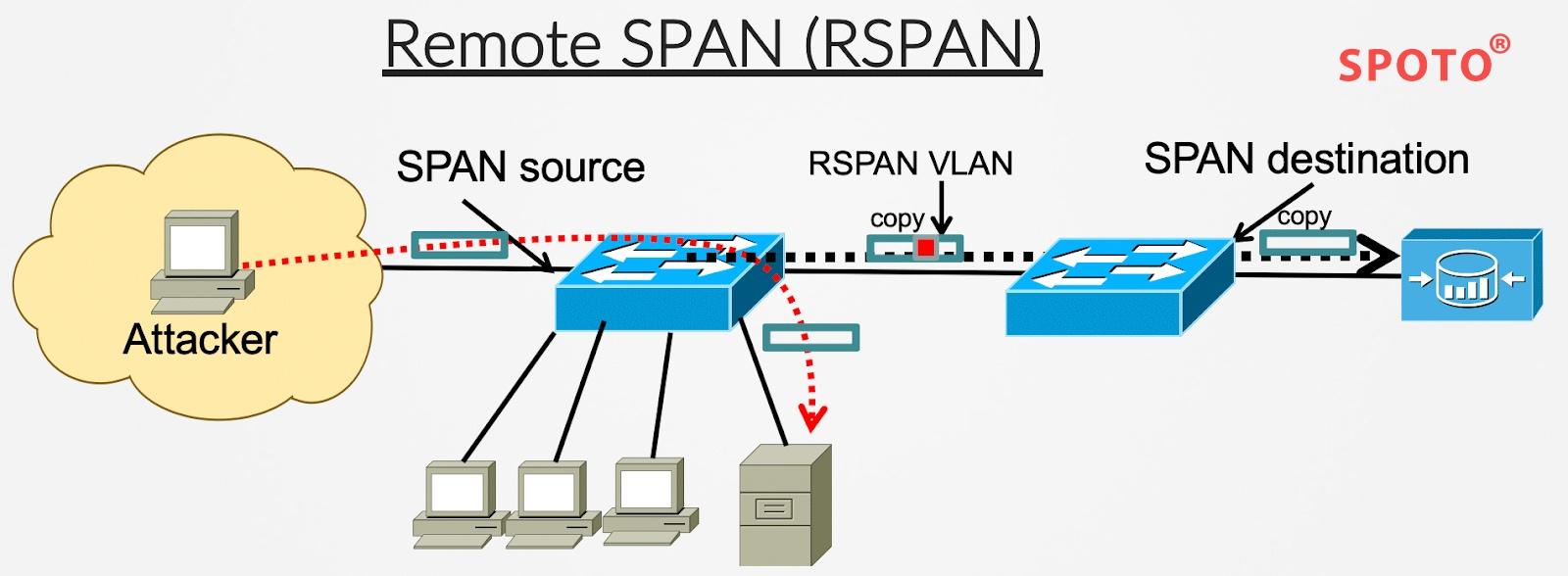
Remote SPAN
Note: To use RSPAN, the switch must be running the LAN Base image.
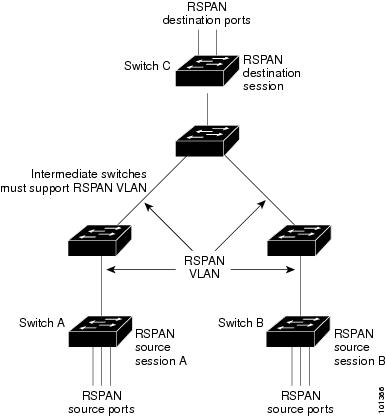
RSPAN supports source ports, source VLAN and target ports on different switches (or different switch stacks), thus realizing remote monitoring of multiple switches in the network. The source ports on Switch A and Switch B are shown in figure 1 / 3. The traffic for each RSPAN session is carried through a user-specified RSPAN VLAN, which is dedicated to all RSPAN sessions in the participating switch. The RSPAN traffic from the source port or VLAN is copied to the RSPAN VLAN and forwarded to the target session of the monitoring RSPAN VLAN through the relay port hosting the RSPAN VLAN. Each RSPAN source switch must have a port or VLAN as the RSPAN source. The target is always a physical port, as shown in Switch C.
Figure 1-3 Example of RSPAN Configuration
SPAN and RSPAN Concepts and Terminology
This section describes concepts and terminology associated with SPAN and RSPAN configuration.
SPAN Sessions
SPAN sessions(local or remote)allow you to monitor traffic on one or more ports or VLANs and send the monitored traffic to one or more target ports.
A local SPAN session is an association between a target port and a source port or source VLAN, all of which are on a single network device. There are no separate source and destination sessions for the local SPAN. The local SPAN session gathers a user-specified set of inlet and exit packets and forms SPAN data streams that are directed to the destination port.
The RSPAN includes at least one RSPAN source session, RSPAN VLAN and at least one RSPAN target session. You can configure RSPAN source sessions and RSPAN target sessions separately on different network devices. To configure an RSPAN source session on a device, associate a set of source ports or source VLAN with RSPAN VLAN. The output of this session is the SPAN packet stream sent to RSPAN VLAN. To configure an RSPAN destination session on another device, associate the destination port with RSPAN VLAN. The target session collects all RSPAN VLAN traffic and sends it to the RSPAN destination port.
RSPAN source sessions are very similar to local SPAN sessions, except for packet flow orientation. In the RSPAN source session, SPAN packets are remarked using RSPAN VLAN ID and directed to the target switch through the normal relay port.
The RSPAN target session receives all the packets received on the RSPAN VLAN, the VLAN tag, and displays them on the destination port. The purpose is to provide the user with a copy of all the RSPAN VLAN data packets (except Layer 2 control packets) for analysis.
Multiple source sessions and multiple target sessions can be active in the same RSPAN VLAN. There can also be an intermediate switch that separates the RSPAN source from the target session. These switches are not able to run RSPAN, but they must respond to the requirements of the RSPAN VLAN (see the "RSPAN VLAN" section).
if you want to get more details, and you can click here:
Traffic monitoring in a SPAN session has these restrictions:
The source can be a port or VLAN, but cannot mix the source port and the source VLAN. in the same session, The switch supports up to two source sessions (local SPAN and RSPAN source sessions).
You can run local SPAN and RSPAN source sessions in the same switch stack. The switch stack supports a total of 66 source and RSPAN target sessions. With the LAN Lite license, the switch supports only one SPAN session.
You can have multiple destination ports in a SPAN session, but no more than 64 destination ports per switch stack. You can configure two separate SPAN or RSPAN source sessions using separate or overlapping SPAN source ports and VLAN groups.
SPAN sessions do not interfere with the normal operation of the switch. However, oversubscribed SPAN targets (for example, monitoring 10 Mb / s ports on 100 Mb / sports) can cause packet loss or loss. When RSPAN is enabled, each monitored packet is transmitted twice, once as normal traffic and once as monitored packet.
Therefore, monitoring a large number of ports or VLAN may generate a large amount of network traffic. You can configure a SPAN session on a disabled port; however, a SPAN session does not become active unless the target port and at least one source port or VLAN, are enabled for the session. Switches do not support combining local SPAN and RSPAN. That is, in a single session, the RSPAN source session cannot have a local destination port, the RSPAN target session cannot have a local source port, and the RSPAN target session and the RSPAN source session using the same RSPAN VLAN cannot run on the same switch stack.

 Join Telegram Study Group ▷
Join Telegram Study Group ▷