SPOTO will introduce the site to site VPN configuration with PRE shared key. I hope that it is helpful for you.
Recommended Read:
1. What is VPN-Virtual Private Network
2.Types and classification of VPN.
3. You must know all the information about the Cisco CCNA, CCNP, and CCIE.
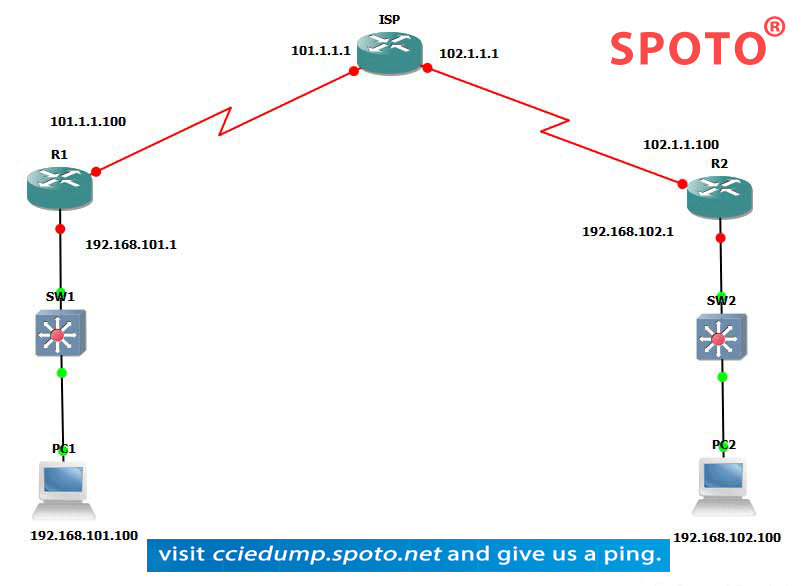
Site to Site VPN
To understand the site-to-site VPN, we cite an example of an organization with offices in multiple locations. The main requirement for any organization is to establish a simple and secure connection between branches so that shared resources and employees can work better. There is also a need for a secure VoIP deployment between branch offices so that the distance between branches can be usually very long between branches, so we need some service providers to connect them. To this end, we have two solutions:
1.Leased Line
There are a number of telecommunications companies providing leased line services. They can provide connectivity solutions, but they charge based on the speed and distance between the branches. If the distance is too long or you want the high-speed cost to rise.
Leased line characteristics:-
1.Isolated from the outside world
2. Link speed will be slow
3.More Security
2.Broadband Internet Connection
This solution is also offered by the same telecommunication companies which provide leased line services. The key difference is that we are connected through a public network i.e. Internet.
Broadband Internet characteristics:-
1.Direct connectivity with the outside world
2.High-speed connectivity
3. Less security as compares to the leased line
When we purchase anything cost plays an important role in the decision. The following is these solutions and decide our requirements:
1. We want direct connectivity with the world through the internet.
2. We want a high-speed link.
3. We also want security for data going between branches.
The only problem is that the broadband connection meets the first 2 requirements is security. To improve security, a VPN is used. Site-to-site VPNs enable two sites to communicate with each other in a secure way through an insecure network (Internet).
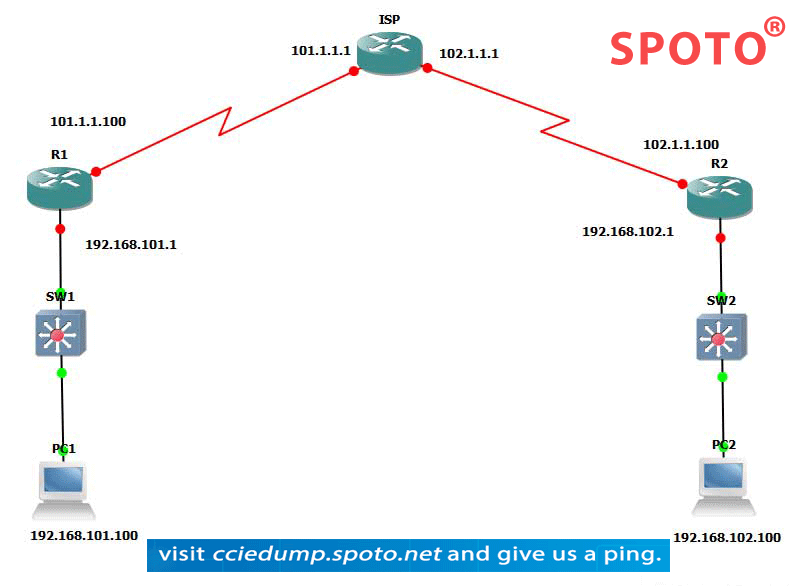
The site to Site VPN Working:-
PC1 wants to communicate with PC2.
PC1 will generate a packet containing the 192.168. 101.100 source and 192.168. 102.100 as its destination. The packet will be transmitted to the gateway.
The gateway checks its destination IP and the packet is routed to the exit interface. When the packet arrives at the egress interface, there is an encrypted mapping that the router will check. If the packet matches the crypto map access list, it is encrypted and hashed. Otherwise, the packet will be routed to the Internet without encryption.
The router will then check the SA. with its peers If SA, is not found, the initiator will use ISAKMP UDP port 500 to send the proposal to the responder peer.
IKE phase 1 and Phase2 will be executed. When phase 2 is complete, the protected data will be passed to the peer.

 Join Telegram Study Group ▷
Join Telegram Study Group ▷