SPOTO devotes itself to IT training for 16 years. Nowadays, SPOTO had expended various certification such as Cisco CCNA, CCNP, CCIE, CISSP certification, and some new products. What’s more, SPOTO guarantees that you can clear every certification exam in your first try. SPOTO will show you the ideal SSL VPN in the following content.
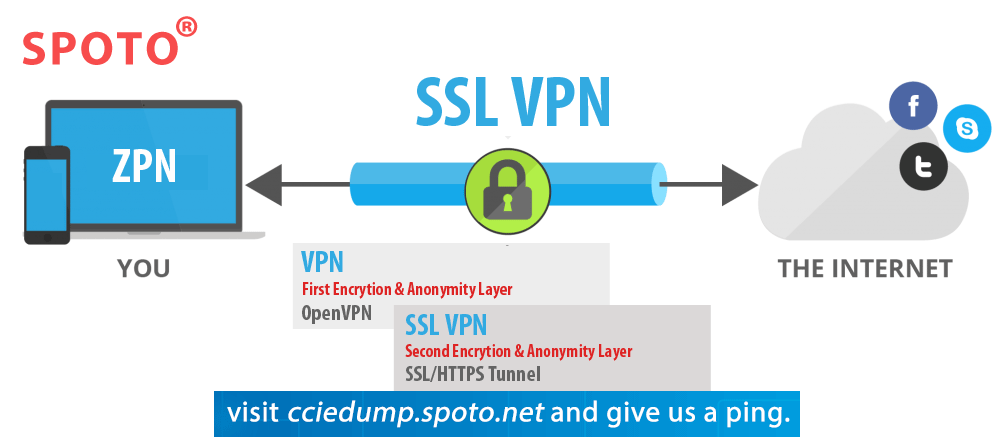
Because of its inception, SSL VPN has been a major technology that has enabled companies to significantly reduce their remote access costs while providing dedicated transaction services over the Internet. VPNs bring great business value, but only with such a precondition can this value be realized, that is, to provide the appropriate level of protection to ensure that enterprise information can only be accessed by authenticated users. To this end, it must be able to provide a powerful authentication barrier that can actively complete the identification of each user and network integrity, so that the process of data transmission over the Internet will not be tampered with.
SSL VPN can establish a proprietary communication channel between a business employee on the Internet and a corporate headquarters at the other end through a special encrypted communication protocol, just like setting up a dedicated line. Compared with the traditional VPN solution, SSL VPN is easy to maintain and maintain without changing the existing network structure; it has strong mobility and disordered security client program; it has powerful access control capability, which enables mobile users to easily access the company's internal B/ S and C/S applications and other core resources.
As a traditional solution, the completion of remote access utilizes the method of renting a private line dial-up connection. Although the effect of this method is quite good, its most typical flaw is the low transmission speed, and the huge network cost makes it difficult for you to provide users with the services they need. However, SSL VPN allows you to fully leverage the power of the Internet to remote access. This approach not only significantly reduces costs; it increases productivity, improves service quality, and provides access to information anytime, anywhere. At present, many vendors have launched their own SSL VPN products, but an ideal SSL VPN solution should have the following five features.
First, you should have strong security.
We say that SSLVPN is a dedicated channel established between enterprise mobile personnel and corporate headquarters. The data transmitted in this channel is internal to the enterprise and is not public. Therefore, it is necessary to carry out remote connection under the premise of security. Taking SafeNet iGate4.0 as an example, its security includes three meanings: one is the security of client access; the other is the security of data transmission; the third is internal Security of resource access.
For remote mobile users, SafeNetiGate recommends using the iKey+PIN code for authentication. The iKey is a USB hardware device that authenticates users. Just like the bank card used on the ATM machine, the authentication can only be performed after the iKey is inserted and the correct PIN code is entered. The iKey or the PIN code only does not work. Second, after a legitimate user connects to the company intranet through authentication, the security of the client device becomes the core of the entire LAN. Although the internal network construction is very strong, because mobile workers can use laptops, PDAs, and public computers in Internet cafes to log in to the company's internal systems, whether the client device has personal firewall anti-virus software installed is a key point for hacker viruses to invade the enterprise. SafeNetiGate has a special client detection function, which can scan out the firewall and anti-virus programs installed by the client and determine their security level to determine whether the device meets the access conditions and ensures the security of the entire system. Third, after the mobile user completes the remote access, the hacker or criminal can steal the corporate secret by copying and copying the data residing in the client buffer. To this end, SafeNetiGate automatically clears the contents of the user buffer after the user is offline. In addition, access is automatically interrupted after the iKey is removed.
Second, support the full application of the connection
The first SSL VPN product only supports the remote connection of web applications. Due to the complexity of most enterprise applications, enterprises often apply not only B/S-based applications but also traditional C/S applications and other non-TCP applications. Such as UDP, which restricts the development of SSLVPN to a certain extent. With the development of product development and upgrades, SafeNet iGate now supports full-network connectivity, including TCP/based B/S and C/S applications, UDP applications such as WebDAV, SMB file sharing access, standard email protocol, Lotus Note, Telnet service, remote terminal, Citrix, etc.
Third, easy to manage and maintain, use of operational.
One of the outstanding advantages of SSLVPN is its mobility and ease of use, but these features tend to increase management difficulty. The SafeNetiGate interface is simple, easy to use, flexible and meticulous in setting access rights, and a user/group/role-based authentication mechanism that allows each file, web address or application to be individually set up to make access control easier to manage. At the same time, SafeNet iGate can directly use the existing user database for authentication and authority allocation, so it can make better use of existing resources and greatly reduce the administrator's work intensity. For all remote access, iGate automatically records access time, session activity, and alert information through a reporting tool that administrators can graphically describe by date, usage, or group.
Fourth, do not reduce operating efficiency by processing SSL.
Because it is a centralized system, SSL acceleration determines the throughput of the entire network. If SSL acceleration does not keep up, remote access will be much lower than the actual Internet access bandwidth. SafeNetiGate uses dedicated SSL acceleration hardware to increase the responsiveness of the VPN. In addition, through data compression technology, iGate compresses all transmitted data and then transmits it, which improves the efficiency and practicability of the entire network.
Five, stable operation, no network interruption
The stability of access is another key factor in satisfying users' remote access. Users cannot tolerate frequent network interruptions. Excessive functionality sometimes affects access stability, and SafeNetiGate optimizes all features to give the system stability.

 Join Telegram Study Group ▷
Join Telegram Study Group ▷