Table of Contents
In modern network environments, the efficient management of broadcast domains is crucial. Virtual LANs (VLANs) and VLAN Trunking play significant roles in achieving this efficiency. Let's delve into the foundational concepts of VLANs and the mechanisms of VLAN Trunking to understand their importance and implementation.
Virtual LANs (VLANs)
A Virtual LAN (VLAN) is an administratively defined subset of switch ports that form a single broadcast domain. In a traditional Ethernet LAN, all devices are in the same broadcast domain by default, meaning a broadcast sent by any device is received by all other devices in the network. This configuration can lead to various issues, such as broadcast storms and security vulnerabilities.
VLANs solve these problems by segmenting the network into smaller, isolated broadcast domains. Each VLAN is identified by a unique VLAN ID, and devices within the same VLAN can communicate as if they were on the same physical network, even if they are geographically dispersed. This segmentation enhances security, reduces congestion, and improves overall network performance.
Key points about VLANs:
- Broadcast Domain Segmentation: VLANs create separate broadcast domains within the same physical network, reducing the scope of broadcast traffic.
- Security: VLANs isolate sensitive data by restricting access to specific network segments.
- Flexibility: VLANs allow logical grouping of users by function, department, or application, regardless of their physical location.
Configuring VLANs
Configuring VLANs involves several steps, typically performed in either VLAN database mode or configuration mode.
VLAN Database Mode:
- Used for creating VLANs and defining their properties.
- Commands:vlan <VLAN-ID>,name <VLAN-NAME>
Configuration Mode:
- Used for assigning interfaces to VLANs and modifying VLAN configurations.
- Commands:interface <INTERFACE-ID>,switchport mode access,switchport access vlan <VLAN-ID>
Private VLANs (PVLANs) further extend VLAN capabilities by creating secondary VLANs (isolated, community, and promiscuous) within a primary VLAN. This configuration enhances security and traffic management by controlling how devices within the same primary VLAN can communicate.
VLAN Trunking: ISL and 802.1Q
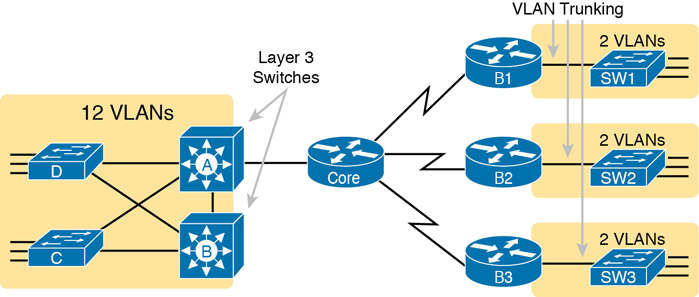
VLAN Trunking allows multiple VLANs to traverse a single physical link between switches, routers, or other network devices. Trunking is essential for maintaining VLAN information across interconnected network devices.
Inter-Switch Link (ISL):
- A Cisco proprietary protocol.
- Encapsulates the original Ethernet frame with a new ISL header and trailer.
IEEE 802.1Q:
- An open standard protocol.
- Inserts a VLAN tag into the Ethernet frame header.
- Supports a concept of a native VLAN, which is untagged.
Trunking protocols enable the sending device to add a VLAN identifier to the frame, ensuring the receiving device knows which VLAN the frame belongs to. This capability is crucial for maintaining VLAN configurations across a network.
Configuring VLAN Trunking
Trunking configuration involves defining the encapsulation type and setting the mode of interfaces to trunk.
Key Commands:
- switchport trunk encapsulation dot1q: Specifies the use of 802.1Q encapsulation.
- switchport mode trunk: Configures the interface as a trunk.
- switchport nonegotiate: Disables Dynamic Trunking Protocol (DTP) negotiation.
VLAN Trunking Protocol (VTP)
VLAN Trunking Protocol (VTP) is a Cisco proprietary protocol that manages the addition, deletion, and renaming of VLANs on a network-wide basis. VTP ensures that all switches in a VTP domain are aware of VLAN changes, facilitating consistent VLAN configuration across the network.
VTP Modes:
- Server Mode: Allows VLAN creation, modification, and deletion. Changes are propagated to all switches in the domain.
- Client Mode: Receives updates from VTP servers but cannot create, modify, or delete VLANs.
- Transparent Mode: Forwards VTP advertisements but does not process them. VLAN changes are local to the switch.
VTP reduces administrative overhead and prevents configuration inconsistencies, making VLAN management more efficient.
Configuring PPPoE
PPP over Ethernet (PPPoE) is a network protocol that encapsulates PPP frames inside Ethernet frames. It is widely used in broadband connections, such as DSL, to provide authentication, encryption, and compression.
Key Commands for PPPoE:
- pppoe enable: Activates PPPoE client functionality.
- pppoe-client dialer-pool-number <POOL-NUMBER>: Associates the client with a dialer pool.
Configuring PPPoE involves setting up the Ethernet interface to encapsulate PPP frames and defining the dialer interface to handle PPP sessions.
Conclusion
Understanding VLANs and VLAN Trunking is essential for modern network design and management. VLANs enhance network segmentation, security, and performance, while trunking and VTP facilitate seamless VLAN propagation across interconnected devices. Additionally, PPPoE plays a critical role in broadband connectivity, providing robust network services over Ethernet.
By mastering these concepts, network engineers can design and manage efficient, secure, and scalable networks, ensuring optimal performance and reliability in complex network environments.