Intermediate System-to-Intermediate System (IS-IS) is a powerful and versatile routing protocol that plays a crucial role in the networking world. Originating from the OSI (Open Systems Interconnection) model, IS-IS has become a staple in modern IP routing due to its robust features and adaptability. This blog post explores the fundamental concepts of IS-IS, its operation, and key technical terms to help you gain a comprehensive understanding of this essential protocol.
What is IS-IS?
IS-IS stands for Intermediate System-to-Intermediate System, a routing protocol designed for moving information efficiently within a computer network, typically within an autonomous system such as a corporate network or an internet service provider (ISP). Unlike many protocols that are derived from the Internet Protocol Suite (TCP/IP), IS-IS originated from the OSI protocol suite, making it a bit unique in its operation and terminology.
Key Components of IS-IS
-
Intermediate Systems (IS): These are the routers in the IS-IS network. IS-IS refers to routers as Intermediate Systems, distinguishing between End Systems (ES), which are typically user devices like computers or smartphones.
-
Network Service Access Point (NSAP) Addressing: IS-IS uses NSAP addresses for identifying systems and interfaces within the network. This addressing scheme is more flexible and hierarchical compared to traditional IP addressing.
-
Link-State Protocol: IS-IS is a link-state routing protocol, meaning each router maintains a map of the network and uses algorithms to calculate the best path to each destination. This is in contrast to distance-vector protocols like RIP (Routing Information Protocol).
IS-IS Network Structure
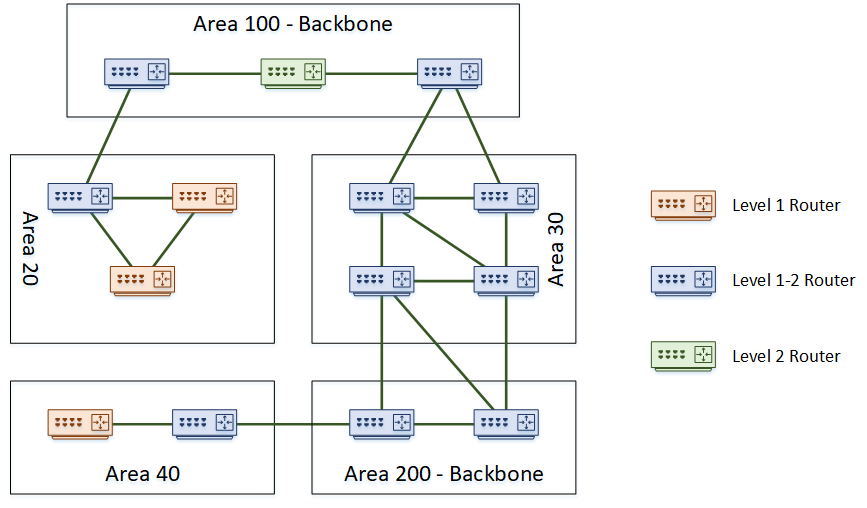
IS-IS operates by dividing the network into areas. These areas help manage large networks by limiting the scope of routing updates, which improves efficiency and scalability.
-
Areas: The IS-IS network can be divided into multiple areas. Each router belongs to an area, and areas are interconnected by backbone routers that share routing information.
-
Levels: IS-IS supports a two-level hierarchy:
- Level 1: Intra-area routing. Routers in the same area exchange information.
- Level 2: Inter-area routing. Routers in different areas exchange information through Level 2 routers.
-
Designated Intermediate System (DIS): In multi-access networks, such as Ethernet, a Designated Intermediate System is elected to manage the communication and reduce the overhead by sending out link-state information on behalf of all routers on that network segment.
IS-IS Operation
IS-IS routers exchange information using Protocol Data Units (PDUs). There are several types of PDUs, but the most important ones are:
-
Hello PDUs (IIH - IS-IS Hello): These are used to establish and maintain neighbor relationships. Routers send Hello PDUs to identify themselves and discover other routers on the network.
-
Link State PDUs (LSPs): These contain information about the router’s links and are used to build a complete picture of the network’s topology. Each router generates its own LSPs, which are then flooded throughout the network.
-
Sequence Number PDUs (SNPs): These are used to ensure the reliability and synchronization of LSPs. They help routers manage and verify the LSPs they have received.
Key Features of IS-IS
-
Scalability: IS-IS is highly scalable, making it suitable for very large networks. Its hierarchical structure and efficient handling of routing updates allow it to perform well in extensive deployments.
-
Flexibility: Originally designed for the OSI stack, IS-IS has been adapted for use with IP, making it versatile and flexible. It supports both IPv4 and IPv6, making it future-proof.
-
Fast Convergence: IS-IS typically converges quickly, which is crucial for maintaining network stability and performance. This means that the network can rapidly adapt to changes, such as link failures or topology changes.
IS-IS Metrics and Path Selection
IS-IS uses cost metrics to determine the best path to a destination. These metrics can be configured based on various parameters like bandwidth, delay, and reliability. The protocol calculates the shortest path first (SPF) using the Dijkstra algorithm, ensuring optimal routing.
-
Wide Metrics: IS-IS supports both narrow and wide metrics. Wide metrics provide a larger range of values, allowing for more granular control over path selection and better support for modern high-speed networks.
-
Traffic Engineering: IS-IS can be used in conjunction with MPLS (Multiprotocol Label Switching) for traffic engineering. This allows network operators to optimize the flow of traffic through the network based on specific requirements and constraints.
Security in IS-IS
Security is a critical aspect of modern networks. IS-IS includes several features to enhance security, including:
-
Authentication: IS-IS supports plain text and cryptographic authentication of routing updates. This helps ensure that only legitimate routers can participate in the routing process.
-
Route Filtering: Network administrators can implement route filtering to control the propagation of routing information. This can prevent unauthorized or incorrect routes from affecting the network.
IS-IS is a robust, scalable, and flexible routing protocol that plays a vital role in modern networking. Its hierarchical structure, efficient handling of routing updates, and support for both IPv4 and IPv6 make it an excellent choice for large and complex networks. Understanding the fundamental concepts and operations of IS-IS is essential for network engineers and administrators looking to optimize and secure their network infrastructure. Whether you are working in a service provider environment or managing an enterprise network, IS-IS offers the tools and features needed to maintain a reliable and efficient routing architecture.










