ospf,ospf demo,ospf costs,ospf tests
SPOTO offers 100% real & valid Cisco, PMP, ISACA, AWS, and other IT exam dumps to help you pass IT
exams. We will list out ospf tips, ospf demo, ospf tutorial, ospf cost, ospf latest industry news, all things you
concern about the Certification online proctored exam.
-
- 662
- SPOTO
- 2024-06-20 15:38
-
- 942
- SPOTO
- 2024-06-19 17:29
ospf,ospf demo,ospf costs,ospf tests
SPOTO offers 100% real & valid Cisco, PMP, ISACA, AWS, and other IT exam dumps to help you pass IT
exams. We will list out ospf tips, ospf demo, ospf tutorial, ospf cost, ospf latest industry news, all things you
concern about the Certification online proctored exam.
-
- 662
- SPOTO
- 2024-06-20 15:38
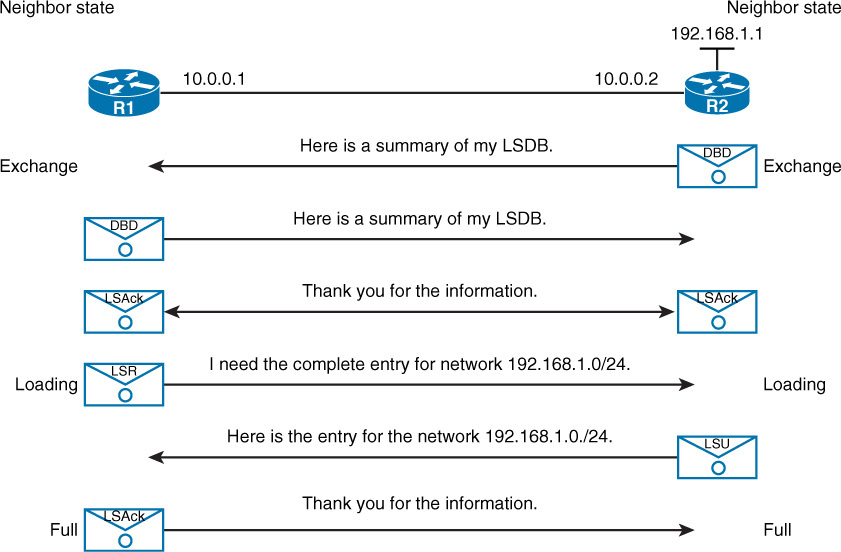
Introduction to OSPF Open Shortest Path First (OSPF) is a fundamental interior gateway protocol (IGP) used for routing within large enterprise networks. Defined by the Internet Engineering Task Force (IETF) and outlined in RFC 2328 for IPv4 (OSPFv2) and RFC 5340 for IPv6 (OSPFv3), OSPF is a link-state routing protocol that dynamically finds the best path for data through a network. This article delves into the technical aspects of OSPF to provide a comprehensive understanding of its components, operations, and configurations. OSPF Database Exchange At the heart of OSPF is the Link-State Database (LSDB), which contains information about the network's topology. The database is built through the exchange of Link-State Advertisements (LSAs). OSPF routers use several types of LSAs to describe the state of their links to neighboring routers: Router LSA (Type 1): Generated by each router, it lists the router’s active interfaces, the state and cost of each interface, and the router's neighbors. Network LSA (Type 2): Created by the Designated Router (DR) on a broadcast segment, it lists all routers on the segment. Summary LSAs (Type 3 and Type 4): Used by Area Border Routers (ABRs) to advertise routes between OSPF areas. AS External LSA (Type 5): Generated by Autonomous System Boundary Routers (ASBRs) to describe routes to external networks. NSSA External LSA (Type 7): Used in Not-So-Stubby Areas (NSSAs) to advertise external routes within the area. These LSAs are flooded throughout the network to ensure all OSPF routers have a synchronized view of the network topology, enabling them to calculate the shortest path using Dijkstra's algorithm. OSPF Design and LSA Types OSPF is designed with scalability and efficiency in mind, featuring several types of LSAs to support different network structures and requirements. The key LSA types and their purposes are outlined as follows: Router LSA (Type 1): Lists the state of the router’s interfaces and its neighbors within an area. Network LSA (Type 2): Describes the routers attached to a broadcast network. Summary LSAs (Type 3 and Type 4): Propagated by ABRs to advertise inter-area routes. AS External LSA (Type 5): Advertises routes external to the OSPF autonomous system. NSSA External LSA (Type 7): Used in NSSAs to describe external routes that are translated to Type 5 LSAs by the ABR. Additionally, OSPF supports hierarchical network design by dividing the network into areas, which reduces the size of the LSDB and limits the scope of LSA flooding, enhancing scalability. OSPF Configuration Configuring OSPF involves defining OSPF processes, specifying OSPF areas, and enabling OSPF on router interfaces. Key OSPF configuration commands include: router ospf process-id: Initiates an OSPF process and enters OSPF router configuration mode. network ip-address wildcard-mask area area-id: Associates a network with a specific OSPF area. ip ospf process-id area area-id: Enables OSPF on an interface and associates it with an area. ipv6 router ospf process-id: Configures OSPFv3 for IPv6 networks. ospfv3 process-id {ipv4 | ipv6} area area-id: Configures OSPFv3 for either IPv4 or IPv6 address families on an interface. These commands allow for granular control over OSPF behavior and enable network engineers to optimize OSPF operation within different network topologies. OSPFv3 and IPv6 OSPFv3, the IPv6 version of OSPF, introduces several enhancements over OSPFv2. It supports multiple address families, enabling both IPv4 and IPv6 routing. Key differences and features of OSPFv3 include: Address Family Support: OSPFv3 can handle multiple address families, allowing IPv4 and IPv6 routing information to be maintained separately. Link LSA (Type 8): Advertises the IPv6 link-local address and other link-local parameters. Intra-Area-Prefix LSA (Type 9): Carries IPv6 prefixes associated with a router or a network. OSPFv3 configuration commands are similar to those in OSPFv2 but include additional options to handle IPv6-specific parameters. OSPF Authentication OSPF supports several authentication methods to secure routing information and prevent unauthorized access. The main types of OSPF authentication are: Null Authentication (Type 0): No authentication is used. Simple Password Authentication (Type 1): A clear-text password is included in OSPF packets. MD5 Authentication (Type 2): A more secure method using MD5 hash values. To configure authentication, the following commands are used: area area-id authentication: Enables authentication for an OSPF area. ip ospf authentication-key key: Configures the authentication key for an interface. ip ospf message-digest-key key-id md5 key: Configures MD5 authentication for an interface. These authentication mechanisms ensure that only trusted routers can participate in the OSPF routing process, enhancing network security. Graceful OSPF Restart The Graceful Restart feature allows OSPF routers to restart without disrupting OSPF neighbors and routes. During a graceful restart, the restarting router maintains its OSPF state, preventing route flapping and minimizing traffic disruption. Key steps in a graceful restart include: Sending Hello packets with router priority set to 0: This indicates the router is undergoing a restart. Flushing LSAs: The router flushes its LSAs to inform neighbors of the restart. Flooding a new Router LSA: After the restart, the router floods a new Router LSA with maximum link costs to signal neighbors. Graceful restart is configured using the shutdown command and can be fine-tuned with additional parameters for specific network requirements. OSPF is a robust and versatile routing protocol essential for large and complex network environments. Its ability to dynamically adjust to network changes, combined with features like hierarchical design, multiple LSA types, and support for IPv6, makes it a cornerstone of modern network routing. Understanding and configuring OSPF, including OSPFv3 for IPv6 and security mechanisms, is crucial for network engineers aiming to optimize and secure their network infrastructures. ​ -
- 942
- SPOTO
- 2024-06-19 17:29
IP routing is the process of moving packets across a network from a source to a destination. It involves various protocols and techniques to ensure efficient and reliable data transmission. Chapter 5 of the "CCIE Routing and Switching v5.0 Official Cert Guide, Volume 1" offers a comprehensive exploration of IP routing. This blog post will introduce key technical terms and fundamental concepts of IP routing, enabling readers to understand how data navigates through complex network infrastructures. What is IP Routing? IP routing is the mechanism by which data packets are forwarded from one network segment to another. It involves routers and routing protocols that determine the best path for data to travel across an interconnected network. Routers maintain routing tables that store the routes to different network destinations. Key Components of IP Routing: Routing Table: A database in a router that stores route information, including destination networks and the next hop to reach them. Routing Protocols: Algorithms and processes that routers use to communicate route information and select optimal paths. Next Hop: The immediate next device to which a packet should be forwarded on its way to the final destination. Static vs. Dynamic Routing Routing can be classified into static and dynamic routing based on how routes are determined and maintained. Static Routing: Definition: Static routing involves manually configuring routes in a router's routing table. Use Cases: Typically used in smaller networks or specific network segments where routes do not change frequently. Advantages: Simple and predictable. Disadvantages: Lack of scalability and flexibility, as manual updates are required for changes. Dynamic Routing: Definition: Dynamic routing uses routing protocols to automatically discover and maintain routes. Use Cases: Suitable for larger, complex networks with frequent topology changes. Advantages: Scalability, flexibility, and adaptability. Disadvantages: Requires more resources and introduces complexity. Common Routing Protocols Routing protocols are essential for dynamic routing, enabling routers to exchange information and determine the best paths for data packets. Here are some key routing protocols: RIP (Routing Information Protocol): Type: Distance-vector routing protocol. Metric: Hop count. Characteristics: Simple to configure, suitable for small networks, limited to 15 hops, updates every 30 seconds. OSPF (Open Shortest Path First): Type: Link-state routing protocol. Metric: Cost, based on bandwidth. Characteristics: Scalable, fast convergence, hierarchical design with areas, supports VLSM and CIDR. EIGRP (Enhanced Interior Gateway Routing Protocol): Type: Advanced distance-vector protocol. Metric: Composite metric (bandwidth, delay, load, reliability). Characteristics: Rapid convergence, supports unequal-cost load balancing, uses DUAL algorithm. BGP (Border Gateway Protocol): Type: Path-vector protocol. Metric: Path attributes (AS path, next hop, etc.). Characteristics: Used for routing between autonomous systems (inter-domain routing), highly scalable, supports policy-based routing. Route Redistribution Route redistribution involves sharing route information between different routing protocols within the same network. This process is crucial in networks that use multiple routing protocols, enabling seamless communication across different network segments. Key Concepts: Administrative Distance: A value that routers use to rate the trustworthiness of routes received from different routing protocols. Lower values are preferred. Redistribution Process: Configured on a router to import and export routes between different routing protocols. Routing Metrics and Path Selection Routing metrics are values used by routing protocols to determine the best path for data packets. Different protocols use different metrics, such as hop count, bandwidth, delay, load, and reliability. Path selection is based on these metrics to optimize network performance. Common Metrics: Hop Count: The number of routers a packet must pass through. Bandwidth: The data capacity of a link. Delay: The time taken for a packet to traverse a path. Load: The amount of traffic on a link. Reliability: The likelihood of a link failure. Route Summarization Route summarization, or route aggregation, is the process of combining multiple network routes into a single, summarized route. This technique reduces the size of routing tables, conserves bandwidth, and improves network efficiency. Benefits: Reduces Routing Table Size: Aggregates multiple routes, decreasing the amount of routing information that needs to be processed and stored. Enhances Performance: Simplifies routing decisions, reducing the processing load on routers. Improves Stability: Minimizes the impact of network changes on routing tables. Example: If a router has routes to 192.168.1.0/24, 192.168.2.0/24, and 192.168.3.0/24, it can summarize them as 192.168.0.0/22. IPv6 Routing IPv6 routing introduces new considerations due to the differences between IPv4 and IPv6 addressing. Routing protocols have been updated or developed to support IPv6. Key Points: IPv6 Addressing: Uses 128-bit addresses, vastly increasing the address space compared to IPv4. Updated Protocols: OSPFv3, EIGRP for IPv6, and MP-BGP support IPv6 routing. Dual Stack: Networks can run IPv4 and IPv6 simultaneously, requiring routers to handle both types of addresses and protocols. Routing Security Securing the routing infrastructure is critical to protect against threats such as route hijacking, spoofing, and denial of service attacks. Several techniques and protocols are used to enhance routing security. Key Security Measures: Route Authentication: Ensures that routing updates come from trusted sources. Examples include MD5 authentication for OSPF and BGP. Route Filtering: Controls which routes are accepted or advertised, preventing the propagation of invalid or malicious routes. Access Control Lists (ACLs): Restrict access to routing protocol communications based on IP addresses and other criteria. IP routing is a fundamental aspect of network design and operation, ensuring that data packets are efficiently and reliably delivered across interconnected networks. Understanding the principles of static and dynamic routing, routing protocols, route redistribution, metrics, summarization, IPv6 routing, and routing security is essential for network engineers and administrators. Mastery of these concepts enables the design and maintenance of robust, scalable, and secure networks, capable of supporting diverse and evolving communication needs.