ipv6,ipv6 demo,ipv6 costs,ipv6 tests
SPOTO offers 100% real & valid Cisco, PMP, ISACA, AWS, and other IT exam dumps to help you pass IT
exams. We will list out ipv6 tips, ipv6 demo, ipv6 tutorial, ipv6 cost, ipv6 latest industry news, all things you
concern about the Certification online proctored exam.
-
- 4460
- SPOTO
- 2024-06-20 15:20
-
- 943
- SPOTO
- 2024-06-19 17:29
ipv6,ipv6 demo,ipv6 costs,ipv6 tests
SPOTO offers 100% real & valid Cisco, PMP, ISACA, AWS, and other IT exam dumps to help you pass IT
exams. We will list out ipv6 tips, ipv6 demo, ipv6 tutorial, ipv6 cost, ipv6 latest industry news, all things you
concern about the Certification online proctored exam.
-
- 4460
- SPOTO
- 2024-06-20 15:20
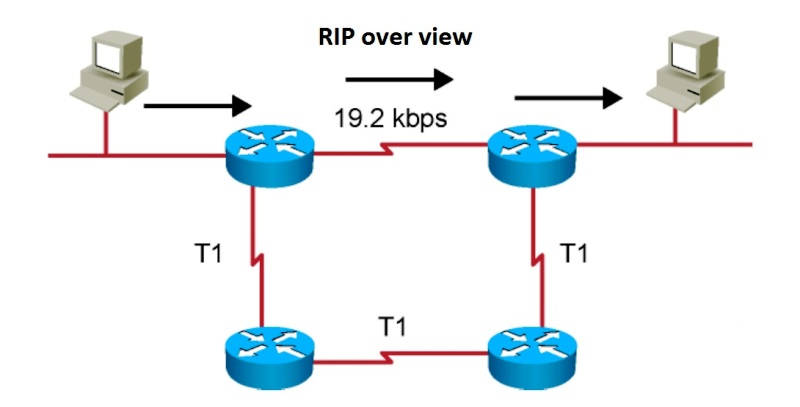
In the ever-evolving landscape of networking, the Routing Information Protocol (RIP) has stood the test of time due to its simplicity and effectiveness. This blog post delves into the technical intricacies of RIPv2 and RIPng, both of which are essential for modern network engineers. Drawing from the comprehensive content in Chapter 7 of the CCIE Routing and Switching v5.0 Official Cert Guide, we will explore key concepts and technical terms to provide a thorough understanding of these protocols. Introduction to RIP RIP is a distance-vector routing protocol that has been a staple in network engineering since its inception. Designed for simplicity, RIP employs hop count as the primary metric for path selection, making it straightforward yet powerful for small to medium-sized networks. RIPv2: Enhancements and Features 1. Protocol Basics RIPv2, defined by RFC 2453, is an enhancement over the original RIPv1. It supports Classless Inter-Domain Routing (CIDR) and Variable Length Subnet Masking (VLSM), allowing for more efficient use of IP addresses. This version also includes the ability to carry subnet information in its updates, which RIPv1 lacked. 2. Multicast Updates RIPv2 improves network efficiency by using the multicast address 224.0.0.9 for routing updates, as opposed to broadcasting them to all nodes on a network. This reduces unnecessary load on devices that are not participating in RIP. 3. Authentication A significant addition in RIPv2 is support for route authentication. This helps secure routing updates, ensuring that only trusted routers can participate in the routing process. RIPv2 supports simple password authentication and MD5 authentication, providing a layer of security against routing attacks. 4. Route Tagging Route tagging in RIPv2 allows for better route management and policy implementation. Tags can be used to indicate routes from different sources, which is useful in complex environments with multiple routing protocols. 5. Split Horizon and Route Poisoning To prevent routing loops, RIPv2 implements split horizon and route poisoning. Split horizon prohibits a router from advertising a route back onto the interface from which it was learned. Route poisoning marks a route as unreachable (with a metric of 16) when it is no longer valid, prompting other routers to remove the route from their tables. Configuring RIPv2 Basic Configuration Configuring RIPv2 on Cisco routers involves enabling the RIP process and specifying the networks that participate in RIP. For example: router rip version 2 network 192.168.1.0 Distribute Lists RIPv2 allows for filtering of routing updates using distribute lists. These can be based on access control lists (ACLs) or prefix lists, enabling fine-grained control over which routes are advertised or accepted. distribute-list 10 in distribute-list 20 out RIPng: RIP for IPv6 With the advent of IPv6, RIP was adapted to support the new addressing scheme, resulting in RIPng (RIP next generation). Defined by RFC 2080, RIPng retains the simplicity of RIPv2 while incorporating necessary changes for IPv6. 1. Protocol Adjustments RIPng operates on UDP port 521 and uses the multicast address FF02::9 for routing updates. Unlike RIPv2, which uses IPv4 addresses, RIPng routes IPv6 prefixes. The maximum hop count remains 15, maintaining consistency with RIPv2. 2. Simplified Header The RIPng message format includes a simplified header, omitting the address family identifier used in RIPv2. This is because RIPng exclusively handles IPv6 routes. 3. Authentication Unlike RIPv2, RIPng does not include built-in authentication. Instead, it relies on IPsec for securing routing updates, aligning with modern security practices for IPv6. 4. Multiple RIPng Processes Cisco IOS supports running multiple RIPng processes on a single router. Each process can be identified by a unique name, allowing for greater flexibility in complex network environments. 5. Route Poisoning and Metric Offset RIPng supports route poisoning to prevent routing loops, similar to RIPv2. Additionally, metric offsets can be configured to adjust the hop count for routes learned over specific interfaces, providing more control over route selection. Configuration Example Configuring RIPng involves enabling IPv6 unicast routing and the RIPng process on the necessary interfaces: ipv6 unicast-routing ipv6 router rip RIPngProcess interface GigabitEthernet0/0 ipv6 address 2001:DB8:1::1/64 ipv6 rip RIPngProcess enable Advanced Features and Troubleshooting Both RIPv2 and RIPng include advanced features and tools for network optimization and troubleshooting: 1. Timers and Intervals RIP protocols use various timers to manage routing information. These include the update timer (default 30 seconds), invalid timer (180 seconds), hold-down timer (180 seconds), and flush timer (240 seconds). Adjusting these timers can optimize routing performance for specific network conditions. 2. Debugging and Monitoring Cisco IOS provides a suite of commands for monitoring and debugging RIP. Theshow ip rip databaseanddebug ip ripcommands offer insights into the operation of the RIP process, helping administrators diagnose and resolve issues. 3. Route Summarization Route summarization reduces the size of routing tables by combining multiple routes into a single summary route. This is particularly useful in hierarchical network designs. In RIPv2, summarization can be configured manually using theip summary-address ripcommand. RIPv2 and RIPng are fundamental routing protocols that, despite their simplicity, provide robust and flexible solutions for routing in IPv4 and IPv6 networks. Understanding their features, configuration, and best practices is essential for any network engineer. By leveraging the strengths of these protocols, engineers can design and maintain efficient, scalable, and secure networks. For those preparing for certifications like the CCIE Routing and Switching, mastering these protocols is a crucial step towards achieving networking excellence. -
- 943
- SPOTO
- 2024-06-19 17:29
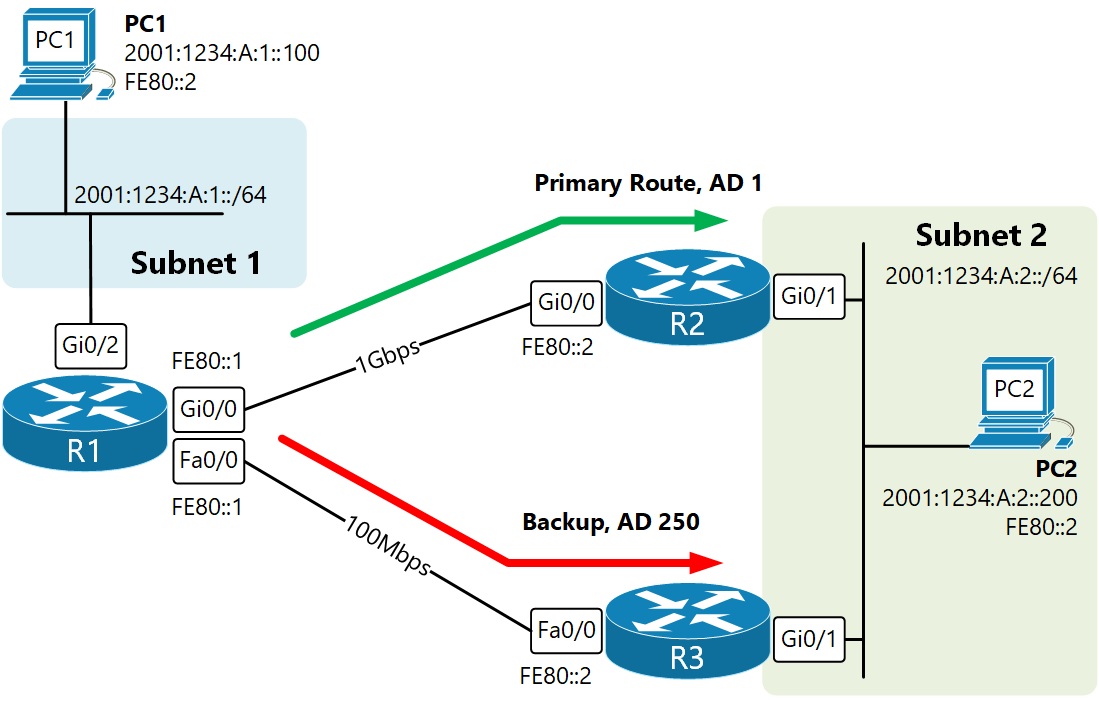
IP routing is the process of moving packets across a network from a source to a destination. It involves various protocols and techniques to ensure efficient and reliable data transmission. Chapter 5 of the "CCIE Routing and Switching v5.0 Official Cert Guide, Volume 1" offers a comprehensive exploration of IP routing. This blog post will introduce key technical terms and fundamental concepts of IP routing, enabling readers to understand how data navigates through complex network infrastructures. What is IP Routing? IP routing is the mechanism by which data packets are forwarded from one network segment to another. It involves routers and routing protocols that determine the best path for data to travel across an interconnected network. Routers maintain routing tables that store the routes to different network destinations. Key Components of IP Routing: Routing Table: A database in a router that stores route information, including destination networks and the next hop to reach them. Routing Protocols: Algorithms and processes that routers use to communicate route information and select optimal paths. Next Hop: The immediate next device to which a packet should be forwarded on its way to the final destination. Static vs. Dynamic Routing Routing can be classified into static and dynamic routing based on how routes are determined and maintained. Static Routing: Definition: Static routing involves manually configuring routes in a router's routing table. Use Cases: Typically used in smaller networks or specific network segments where routes do not change frequently. Advantages: Simple and predictable. Disadvantages: Lack of scalability and flexibility, as manual updates are required for changes. Dynamic Routing: Definition: Dynamic routing uses routing protocols to automatically discover and maintain routes. Use Cases: Suitable for larger, complex networks with frequent topology changes. Advantages: Scalability, flexibility, and adaptability. Disadvantages: Requires more resources and introduces complexity. Common Routing Protocols Routing protocols are essential for dynamic routing, enabling routers to exchange information and determine the best paths for data packets. Here are some key routing protocols: RIP (Routing Information Protocol): Type: Distance-vector routing protocol. Metric: Hop count. Characteristics: Simple to configure, suitable for small networks, limited to 15 hops, updates every 30 seconds. OSPF (Open Shortest Path First): Type: Link-state routing protocol. Metric: Cost, based on bandwidth. Characteristics: Scalable, fast convergence, hierarchical design with areas, supports VLSM and CIDR. EIGRP (Enhanced Interior Gateway Routing Protocol): Type: Advanced distance-vector protocol. Metric: Composite metric (bandwidth, delay, load, reliability). Characteristics: Rapid convergence, supports unequal-cost load balancing, uses DUAL algorithm. BGP (Border Gateway Protocol): Type: Path-vector protocol. Metric: Path attributes (AS path, next hop, etc.). Characteristics: Used for routing between autonomous systems (inter-domain routing), highly scalable, supports policy-based routing. Route Redistribution Route redistribution involves sharing route information between different routing protocols within the same network. This process is crucial in networks that use multiple routing protocols, enabling seamless communication across different network segments. Key Concepts: Administrative Distance: A value that routers use to rate the trustworthiness of routes received from different routing protocols. Lower values are preferred. Redistribution Process: Configured on a router to import and export routes between different routing protocols. Routing Metrics and Path Selection Routing metrics are values used by routing protocols to determine the best path for data packets. Different protocols use different metrics, such as hop count, bandwidth, delay, load, and reliability. Path selection is based on these metrics to optimize network performance. Common Metrics: Hop Count: The number of routers a packet must pass through. Bandwidth: The data capacity of a link. Delay: The time taken for a packet to traverse a path. Load: The amount of traffic on a link. Reliability: The likelihood of a link failure. Route Summarization Route summarization, or route aggregation, is the process of combining multiple network routes into a single, summarized route. This technique reduces the size of routing tables, conserves bandwidth, and improves network efficiency. Benefits: Reduces Routing Table Size: Aggregates multiple routes, decreasing the amount of routing information that needs to be processed and stored. Enhances Performance: Simplifies routing decisions, reducing the processing load on routers. Improves Stability: Minimizes the impact of network changes on routing tables. Example: If a router has routes to 192.168.1.0/24, 192.168.2.0/24, and 192.168.3.0/24, it can summarize them as 192.168.0.0/22. IPv6 Routing IPv6 routing introduces new considerations due to the differences between IPv4 and IPv6 addressing. Routing protocols have been updated or developed to support IPv6. Key Points: IPv6 Addressing: Uses 128-bit addresses, vastly increasing the address space compared to IPv4. Updated Protocols: OSPFv3, EIGRP for IPv6, and MP-BGP support IPv6 routing. Dual Stack: Networks can run IPv4 and IPv6 simultaneously, requiring routers to handle both types of addresses and protocols. Routing Security Securing the routing infrastructure is critical to protect against threats such as route hijacking, spoofing, and denial of service attacks. Several techniques and protocols are used to enhance routing security. Key Security Measures: Route Authentication: Ensures that routing updates come from trusted sources. Examples include MD5 authentication for OSPF and BGP. Route Filtering: Controls which routes are accepted or advertised, preventing the propagation of invalid or malicious routes. Access Control Lists (ACLs): Restrict access to routing protocol communications based on IP addresses and other criteria. IP routing is a fundamental aspect of network design and operation, ensuring that data packets are efficiently and reliably delivered across interconnected networks. Understanding the principles of static and dynamic routing, routing protocols, route redistribution, metrics, summarization, IPv6 routing, and routing security is essential for network engineers and administrators. Mastery of these concepts enables the design and maintenance of robust, scalable, and secure networks, capable of supporting diverse and evolving communication needs.