As technology rapidly advances, the challenges in the field of cybersecurity are becoming increasingly severe. Threats such as hacker attacks, data breaches, and phishing attacks continue to emerge, making cybersecurity a highly scrutinized domain. Consequently, for those aspiring to enter the cybersecurity industry, learning cybersecurity becomes an urgent and imperative task. The debate over whether one should start with programming or computer fundamentals in the journey to enter the realm of cybersecurity is a contentious one. Some advocate for starting with programming, while others suggest prioritizing computer fundamentals. In reality, both are essential, and proficiency in both areas is crucial for mastering cybersecurity. However, for individuals with zero background or those seeking a career change, learning programming or computer fundamentals can pose certain challenges, and the time investment required may seem daunting. Next, we will utilize a roadmap to elucidate the process of entering the field of cybersecurity.
I. Foundation Preparation
Before delving into the cybersecurity domain, certain foundational preparations are necessary, constituting a crucial part of the learning journey for all security practitioners. This stage of learning encompasses essential knowledge in computer fundamentals, network basics, and operating systems. It will take almost 4 to 6 weeks.
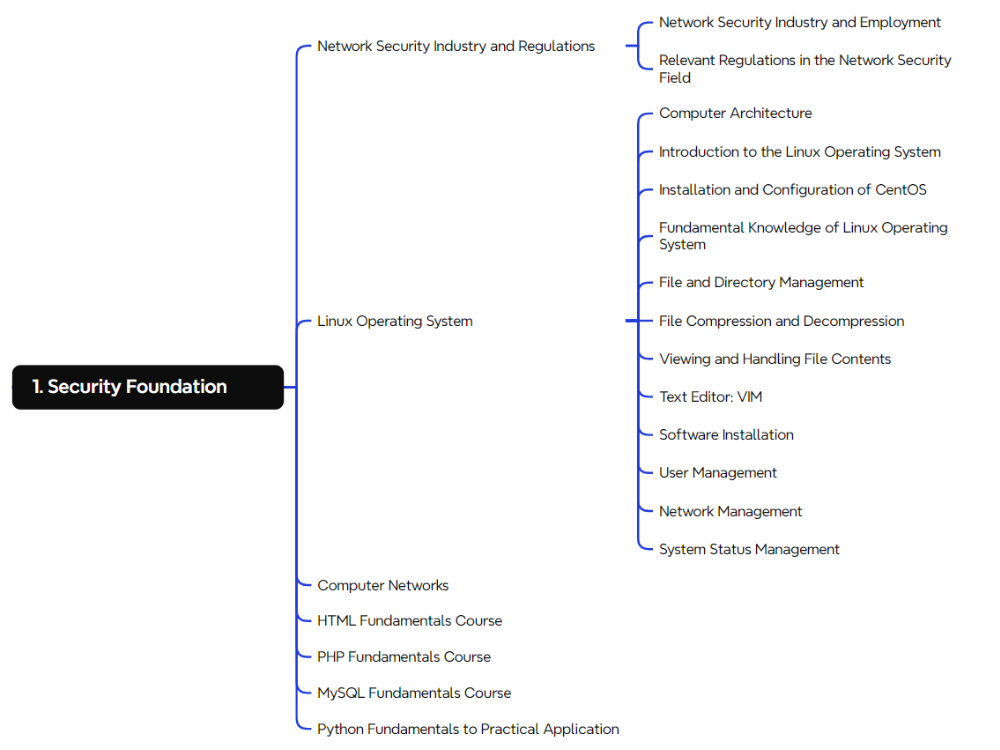
II. Web Penetration Testing
1. Basic Learning (Duration: 1 to 2 weeks)
At this stage, it is imperative to grasp fundamental concepts such as SQL injection, XSS, file uploads, CSRF, and backdoors to lay the groundwork for subsequent web penetration testing. Additionally, studying web penetration cases on forums and understanding the diverse approaches to different sites helps cultivate problems-solving skills.

2. Configuration of Penetration Testing Environment (Duration: 3 to 4 weeks)
Understanding commonly used penetration testing tools like AWVS, SQLMAP, NMAP, BURP, etc., and downloading clean versions for installation is essential. Familiarity with the usage scenarios of these tools, along with seeking additional information on platforms like Google, is recommended.
3. Practical Penetration Operations (Duration: Approximately 6 weeks)
In this phase, delving into real-world penetration scenarios through case studies is crucial. Building a vulnerability environment for testing using platforms like DWVA, SQLi-labs, Upload-labs, bWAPP is recommended. Understanding the stages of penetration testing and mastering the required actions at each stage, as defined by standards like PTES, is essential. Thorough exploration of manual SQL injection, finding ways to bypass WAF, creating custom scripts, studying file upload principles, including truncation, double suffix deception, and leveraging parsing vulnerabilities are key. Understanding XSS principles and types, practical application on a CMS with XSS vulnerabilities, comprehension of backdoors, and attempting to script one are integral components. Lastly, researching privilege escalation methods on both Windows and Linux platforms is crucial.
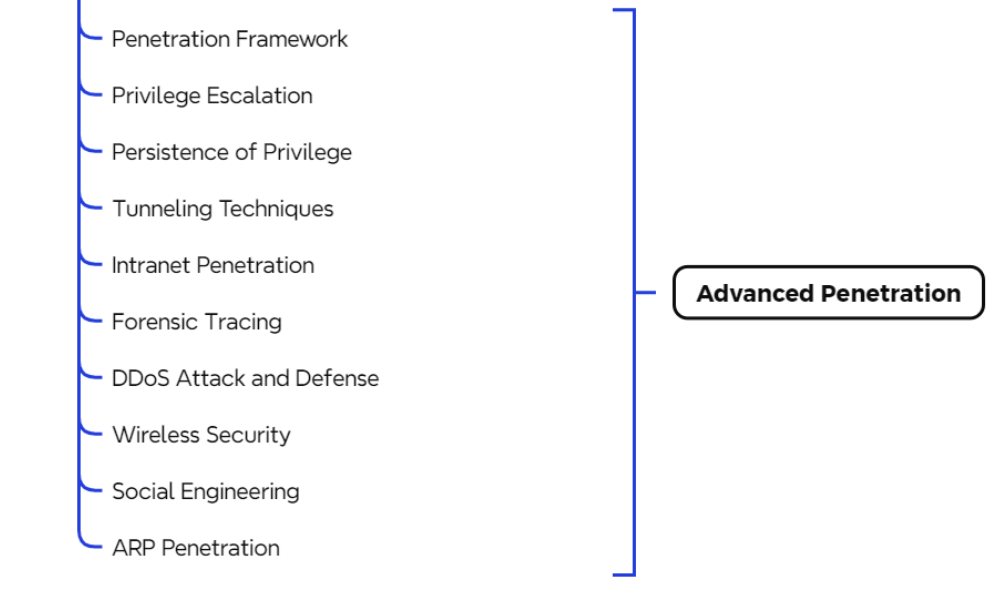
III. Advanced
After gaining entry and securing a job, how does one advance further? Details are provided in the image below.

Starting a career in cybersecurity is like embarking on a thrilling adventure. In today's fast-paced digital world, the need for skilled network security professionals is growing rapidly. However, with this rising demand comes tougher competition, pushing aspiring individuals to find ways to stand out. One effective strategy is earning recognized network security certifications, such as the respected ISACA certification and the well-known CompTIA Security certification.
ISACA offers certifications like the Certified Information Systems Auditor (CISA) and Certified Information Security Manager (CISM), focusing on auditing, control, and information security management. These certifications not only show off your expertise but also highlight your commitment to high standards in the field.
CompTIA Security certification is another valuable credential, providing a solid understanding of core security concepts. Covering topics like network security, cryptography, and risk management, it equips professionals with the knowledge to tackle real-world security challenges.
When pursuing these certifications, resources like SPOTO can be a game-changer. SPOTO is a reliable platform offering accurate CompTIA Security exam dumps, free practice tests, and expert guidance. Using these resources not only streamlines your preparation but also significantly boosts your chances of passing the exams. The experienced experts at SPOTO provide valuable insights, ensuring you're well-prepared for the certification journey.
Combine your dedication with reputable certifications and reliable resources from SPOTO, and you'll not only enhance your skills but also position yourself for success in the competitive field of network security.
Feel free to reach out to us for access to the comprehensive Cybersecurity Roadmap in high definition.