As a network engineer, you will often meet many network problems in your projects. Today, SPOTO tutors will introduce some basic network commands that you can use to detect and locate the fault points. By using the network commands, the work of solving the problems can achieve a multiplier effect.
1.ping (Packet Internet Groper / Internet Explorer)
Ping is a command under Windows, Unix and Linux systems. Ping also belongs to a communication protocol and is part of the TCP / IP protocol. Use the "ping" command can check whether the network connectivity, can be very good to help us analyze and determine the network failure.
Application Format: Ping space IP address. The command can also add many parameters to use, specifically type Ping Press Enter to see detailed instructions.
Ping is to send a test packet to a web site to see whether the other site response and statistics response time, in order to test the network.
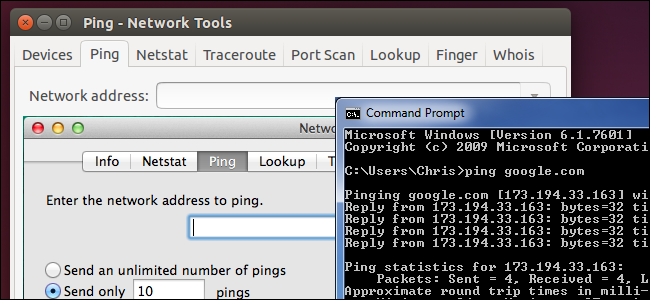
The specific way is, start - run-cmd, in the dos window, called out to enter a ping space + you want to ping the URL, a carriage return.
Note: If you want to know more knowledge of Networking or Cisco practice tests to pass your exam, please click here to contact us.
For example, "pingXXX URL" screen will display similar information
\
windows 7 system ping Baidu website case
Note: The following time = 25ms is the response time, the smaller this time, the faster you connect to this address.
ping command parameters
Usage: ping [-t] [-a] [-n count] [-l length] [-f] [-i ttl] [-v tos] [-r count] [-s count] [-j computer- list] | [-k computer-list] [-w timeout] destination-list
-t: non-stop ping each other's host until you press Control-C;
-a: resolve computer NetBios name;
-n count: Sets the number of data to echo requests sent (X is the number to be sent, if not written, the default is to send 4 times);
-l size: define the size of the echo packet (in the case of the default windows ping send packet size 32byte, we can define its own size, but there is a size limit, that is, the maximum can only send 65500byte);
-f: Set "no segmentation" flag in the packet ;
-I TTL Survival time;
-v TOS: service type ;
-r count: Route to record count hops ;
-s count: timestamp for counting hops ;
-j host-list: Loose route along with host list ;
-k host-list: strict routing with host departure ;
-w timeout: wait for each reply timeout ;
-R: Also use the routeing header to test the reverse route ;
-S srcaddr: The source address to use;
-4: Forced use of IPv4;
-6: Forced use of IPv6;
\
ping command parameters
2. ipconfig (IPConfig / display IP configuration value)
IPConfig Utility and Its Equivalent Graphical User Interface - WinIPCfg in Windows 95/98 can be used to display the current TCP / IP configuration settings. This information is generally used to verify that the manually configured TCP / IP settings are correct. However, if your computer and your local area network use the Dynamic Host Configuration Protocol (DHCP) - a protocol under Windows NT that assigns fewer IP addresses to more hosts, similar to dial-up Dynamic IP allocation), the information displayed by this program may be more practical.
Note: If you want to know more knowledge of Networking or Cisco practice tests to pass your exam, please click here to contact us.
In simple terms, ipconfig this command allows us to quickly get the computer's current IP address, subnet mask and default gateway and other information, this information are necessary for testing and failure analysis project. At the same time, this command can also clear the DNS cache (DNS cache).
ipconfig command parameters
ipconfig / all: Displays the native TCP / IP configuration details;
ipconfig / release: DHCP client manual release IP address;
ipconfig / renew: DHCP client manual refresh request to the server;
ipconfig / flushdns: Clear local DNS cache content;
ipconfig / displaydns: display local DNS content;
ipconfig / registerdns: DNS client manual registration to the server;
ipconfig / showclassid: Display network adapter DHCP category information;
ipconfig / setclassid: Set the network adapter DHCP category.
ipconfig / renew "Local Area Connection": Update the configuration of DHCP-assigned IP address for the "Local Area Connection" adapter
ipconfig / showclassid Local *: Displays the DHCP category ID of all adapters whose names start with Local
ipconfig / setclassid "Local Area Connection" TEST: Set the DHCP Category ID of the "Local Area Connection" Adapter to TEST
\
ipconfig command parameters
3. traceroute (route tracking)
traceroute is the tool used to detect the number of gateways that pass between the host sending the packet and the target host. Traceroute's principle is to try to send a probe packet with the smallest TTL to track the gateway through which the packet arrived at the target host, and then listen for a reply from the gateway ICMP. The size of the send packet defaults to 38 bytes.
The program uses its TTL value to achieve its function. Whenever a packet goes through a router, its lifetime will be reduced by one. When its survival time is 0, the host will cancel the data packet and send an ICMPTTL data packet to the originator of the original data packet.
Note: If you want to know more knowledge of Networking or Cisco practice tests to pass your exam, please click here to contact us.
The program sends the first three packets TTL value is 1, then 3 is 2, and so on, it will be a series of packet path. Note that IP does not guarantee that each packet will go the same path.
traceroute command parameter
Usage: Traceroute [options] [data size]
-d: Use Socket-level troubleshooting.
-f: Set the first test packet survival value TTL size.
-F: set not to leave the break bit.
-g: Set the source routing gateway, you can set up to eight.
-i: use the specified network interface to send packets.
-I: Use ICMP echo instead of UDP data information.
-m: Sets the maximum TTL value of the detection packet.
-n: Use the IP address directly instead of the host name.
-p: set the UDP transport protocol communication port.
-r: Ignore the ordinary Routing Table, the data packets directly to the remote host.
-s: Set the IP address of the local host to send packets.
-t: Set the TOS value of the detection packet.
-v: shows the instruction execution in detail.
-w: Set the waiting time for a remote host report.
-x: turn on or off the correctness of the packet inspection.
\
The command in the windows system tracert
Note: The command in windows system is traced.
4.nslookup (name server lookup / domain name query)
nslookup is the name of a program that lets an Internet server administrator or any computer user enter a host name (for example, "www.toutiao.com") and find the appropriate IP address. It also looks for the opposite name to find the host name for an IP address you specify.
usage:
nslookup [-opt ...] # Use the default server interaction mode
nslookup [-opt ...] - server # Use the "server" interactive mode
nslookup [-opt ...] host # Find only the "host" that uses the default server
nslookup [-opt ...] host server # Find only "host" using "server"
\
Use nslookup reverse order to find the first address
5.route command
The Route command is to display and modify the entry network command in the local IP routing table.
Usage: route [-f] [-p] [Command] [Destination] [mask Netmask] [Gateway] [metric metric] [if Interface]
-f
Clear all routes that are not primary routes (those with a netmask of 255.255.255.255), loopback network routes (routes with a destination of 127.0.0.0, a netmask of 255.255.255.0), or multicast routes with a target of 224.0.0.0, With a mask of 240.0.0.0). If it is used in conjunction with one of the commands, such as add, change, or delete, the table is cleared before the command is run.
-p
When used with the add command, the specified route is added to the registry and the IP routing table is initialized when the TCP / IP protocol is started. By default, the added route is not saved when the TCP / IP protocol is started. When used with the print command, a list of persistent routes is displayed. All other commands ignore this parameter. The location where permanent routes are stored in the registry is HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesTcpipParametersPersistentRoutes.
Note: If you want to know more knowledge of Networking or Cisco practice tests to pass your exam, please click here to contact us.
About SPOTO:
SPOTO focus on online IT Certification training for 16 years. SPOTO offers 100% real and valid Cisco CCNA, CCNP, CCIE, ISC, Amazon AWS, Microsoft, and other IT exam practice tests. And we have many free online training courses of Cisco exam on YouTube. You can find many useful and helpful tips and suggestions. If you’re still worried about to prepare and pass the Cisco exam, try SPOTO now. SPOTO tutors will help you get the CCIE number at the first try.
Youtube: https://www.youtube.com/channel/UCEjAjr00o5VmNn5r9dIOY5g

 Join Telegram Study Group ▷
Join Telegram Study Group ▷