Benefits
When SD-WANfirstcametomarketover5yearsago, the value proposition
was based on four key requirements:
•Increasingbandwidththroughtheactivationofidlebackuplinksanddynamic
load-balancing.
•Deliveringfastercloudaccessbyenablingdirectinternetaccessatthe
branch.
•Reducingoperationalandmanagementcoststhroughcentralized
management that was commonly cloud-based.
•LoweringWANcoststhroughtheuseofcheaperinternetorLTEconnectivity
asanalternativetoMPLS.
Thedigitalbusinesshasevolvedandthemodernworkforceisincreasingly
distributed and the applications they consume are becoming more
decentralized, moving from the data center to a multi-cloud environment.
Whencombinedwiththeincreasingnumberofusers, devices, and locations
that need access to cloud applications, this creat an overwhelming
complexity for IT. To address the challenges, IT has to consider more
advancedWANusecasesthatgobeyondthebasiccapabilitiesofferedby
earlier SD-WANsolutions.CiscoSD-WANisacloud-scalar architecture
designed to meet the complex needs of modern wide area network through
three key areas:
•Advancedapplicationoptimizationthatdeliversapredictableapplication
experience as the business applications trade evolves
•Multi-layered security which provides the flexibility to deploy the right
security in the right place, either on-premise or cloud-delivered
•Simplicityatenterprisescalewhichenablesend-to-end policy from the user
to the application over thousands of sites
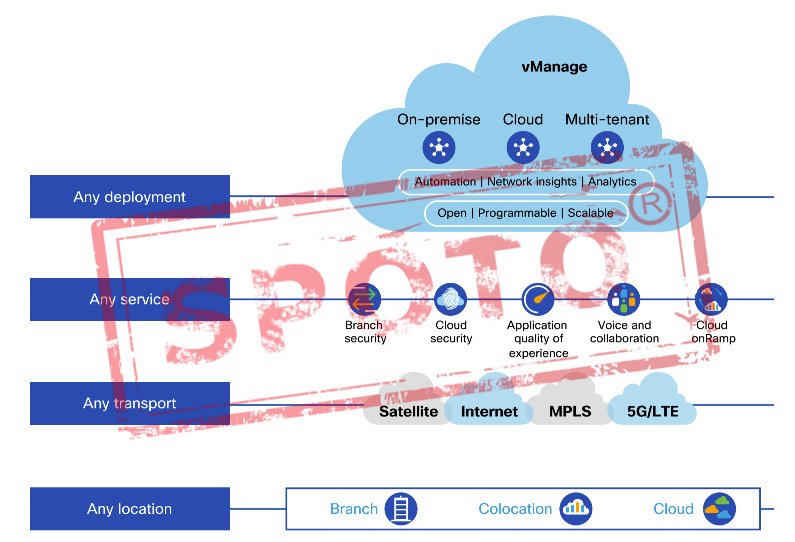
Cisco SD-WAN Cloud-Scale Architecture
Components and architecture
The Cisco SD-WAN solution is a cloud-delivered Wide Area Network (WAN) overlay architecture that extends the principles of software-defined networking (SDN) into the WAN. The solution is broken up into four planes: data, control, management, and orchestration.
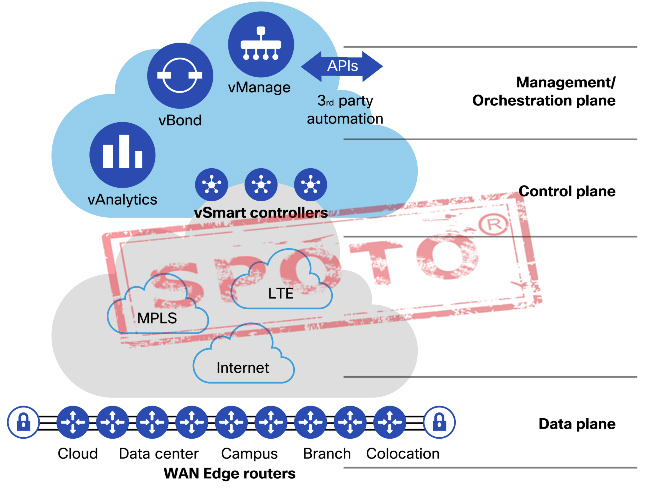
Applying SDN principles to the WAN
The Cisco SD-WAN solution contains four key components responsible for each plane of organization:
Cisco vManage
In the management plane, Cisco vManage represents the user interface of the solution. Network administrators and operators perform configuration,
provisioning, troubleshooting, and monitoring activity here. vManage offers both a single-tenant dashboard and a multitenant dashboard for a variety of customer and service provider deployments.
Cisco vBond
Cisco vBond resides in the orchestration plane. The vBond controller is largely responsible for the Zero-Touch Provisioning process as well as first-line authentication, control/management information distribution, and facilitating Network Address Translation (NAT) traversal. When a router boots up for the first time in an unconfigured state, vBond is responsible for onboarding the device into the SD-WAN fabric. It is the job of vBond to understand how the network is constructed and then share that information amongst other components.
Cisco Vsmart
Cisco vSmart is the “brain” of the solution and exists within the control plane. As policies are created on vManage, vSmart is the component responsible for enforcing these policies centrally. When branches come online, their routing information is exchanged with the vSmart controller and not directly with other branches. By using policies, routing information is influenced and shared with other locations which determine how individual branches will communicate with each other. As routes are received via the Overlay Management Protocol (OMP) from branch locations, the vSmart controller can invoke policy created on vManage against these routes and control how traffic traverses the SD-WAN fabric.
Cisco WAN Edge routers
Cisco WAN Edge routers are responsible for establishing the network fabric and forwarding traffic. Cisco WAN Edge routers come in multiple forms, virtual and physical, and are selected based on the connectivity, throughput, and functional needs of the site. All of these components combine to form the Cisco SD-WAN fabric. In the following diagram, notice the relationship between each of the components:
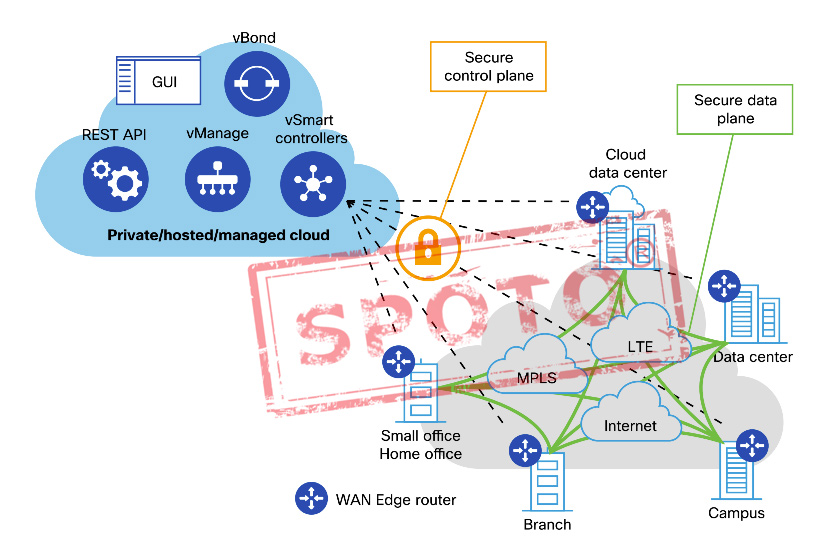
Cisco SD-WAN fabric components
The WAN Edge routers form Internet Protocol Security (IPSec) tunnels with each other to form the SD-WAN overlay. In addition, a control channel is established between the WAN Edge routers and each of the control elements. Through this control channel, each component receives configuration, provisioning and routing information. Note that no data plane traffic is forwarded to the control infrastructure.
Overlay Management Protocol (OMP)
Cisco SD-WAN uses OMP which manages the overlay network. OMP runs between the vSmart controllers and WAN Edge routers where control plane information, such as route prefixes, next-hop routes, crypto keys, and policy information, is exchanged over a secure connection. If no policy is defined, the default behavior of OMP is to allow a full mesh topology, where each WAN Edge router can connect directly to other WAN Edge routers. OMP advertises three types of routes:
1. OMP routes are prefixes that are learned at the local site. The prefixes are redistributed into OMP so that they can be carried across the overlay. OMP
routes advertise attributes including transport location (TLOC) information,
which is similar to a BGP next-hop IP address for the route, and other attributes such as origin, originator, preference, site ID, tag, and VPN. An OMP route is only installed in the forwarding table if the TLOC to which it points is active.
2. TLOC routes are the logical tunnel termination points on the WAN Edge routers that connect into a transport network. A TLOC route is uniquely identified and represented by a three-tuple, consisting of system IP address, link color, and encapsulation.
3 Service routes represent services (such as firewall, IPS, application optimization, etc.) that are connected to the WAN Edge local-site network and are available for other sites for use with service chaining. In addition, these routes also include VPNs. VPN labels are sent in this update type to tell the vSmart controllers which VPNs are serviced at a remote site. For more information on service chaining, see the Leveraging colocations chapter later in this book.24
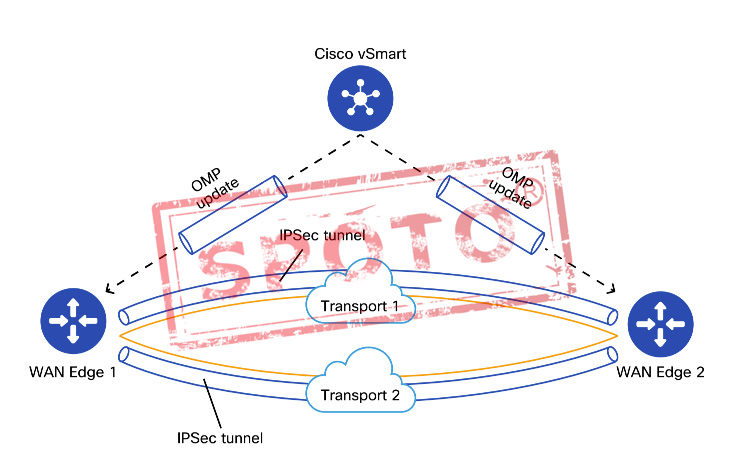
Bi-directional Forwarding Detection (BFD)
The BFD mechanism is used by the WAN Edge routers to probe and measure the performance of the transport links. It also determines the best performing path based on the result of the BFD probes, giving information about latency, jitter, and loss on all the transport links.
High availability and redundancy
The Cisco SD-WAN solution is designed with application availability and performance as a cornerstone. The goal of any high-availability solution is to ensure that network services are resilient to failure. The core of the Cisco SD-WAN high-availability solution is achieved through a combination of three factors:
• Device redundancy: The strategy consists of installing and provisioning redundant devices and redundant components within the hardware. These devices are connected by a secure control plane that operates in an active/active fashion.
• Robust network design: Support for multiple protocols (such as VRRP, BGP, and OSPF) and redundant physical connections to both LAN and WAN segments.
• Software mechanisms: Software mechanisms ensure rapid recovery from both direct and indirect failure. To provide a resilient control plane, the solution regularly monitors the status of all WAN Edge routers in the network and automatically adjusts to changes in the topology as routers join and leave the network. For data plane resilience, the Cisco SD-WAN software implements standard protocol mechanisms, specifically BFD, which runs on the secure IPsec tunnels between WAN Edge routers.
Control plane redundancy
Orchestration level redundancy is achieved by having one DNS name (FQDN) with multiple IP addresses representing different vBond controllers. Control plane redundancy is implemented with multiple vSmart controllers, one WAN Edge router will create a hash and contact two of the redundant vSmart controllers by default. Network management system redundancy can be achieved by building clusters with multiple vManage instances.











Comments