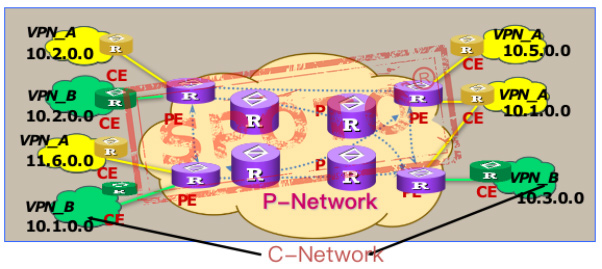
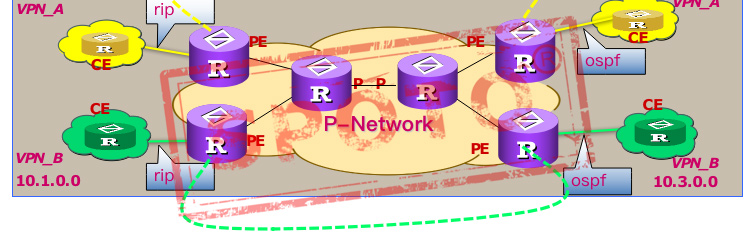
CE (Custom Edge):
User equipment directly connected to the service provider.
PE (Provider Edge Router):
refers to the edge router on the backbone network, which is connected to the CE and is mainly responsible for the access of VPN services.
P (Provider Router):
refers to the core router on the backbone network, which mainly completes routing and fast-forwarding functions. Due to different network sizes, there may not be a P router in the network. The PE router may also be a P router at the same time.
Overlay VPN method:
Service providers only provide logical dedicated channels, and user edge routers directly exchange user routing information.
L2 VPN:
Implemented through Layer 2 WAN technologies such as FR (Frame Relay) and ATM
L3 VPN:
through the three-layer tunnel technology GRE, IPsec
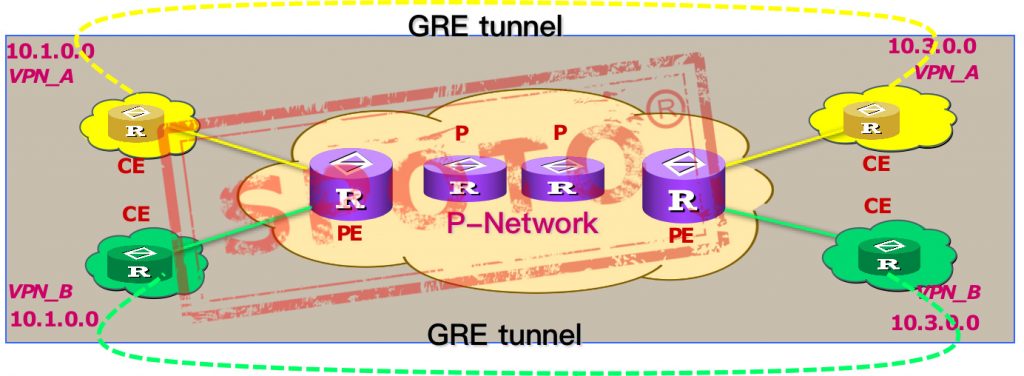
Features:
Establish a tunnel between CE and CE, and directly transfer routing information, routing protocol data is always exchanged between customer equipment, service providers know nothing about customer network structure. Typical representatives are GRE, IPSec
Advantage:
Different customer address spaces can overlap, and confidentiality and security are very good.
Disadvantages:
Customers need to create and maintain VPNs themselves. Usually, customers are unwilling and do not have this ability.
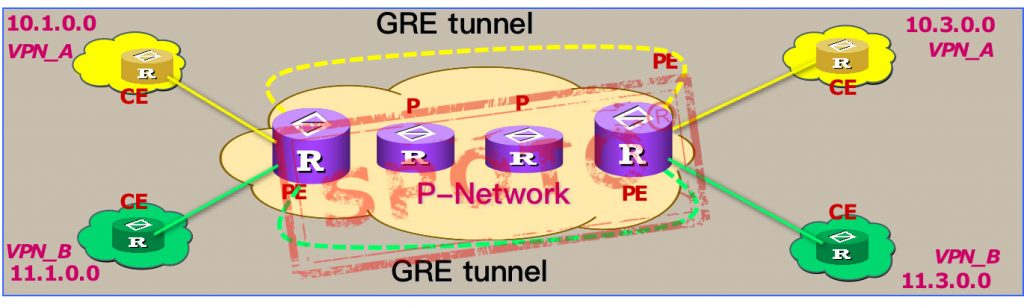
Features:
A corresponding GRE tunnel is established on the PE for each VPN user, routing information is passed between the PE and the PE, and the P device in the public network does not know the routing information of the private network.
Advantage:
The customer completely hands over the creation and maintenance of the VPN to the service provider, with better confidentiality and security.
Disadvantages:
Different VPN users cannot share the same address space. Even if they can share, the addresses between PE and CE, and the addresses between tunnels must not be the same, and a large number of ACLs and policy routes must be used. It is not feasible in practice.
Peer-to-Peer VPN:
Exchange user routing information between user routers and service provider routers;
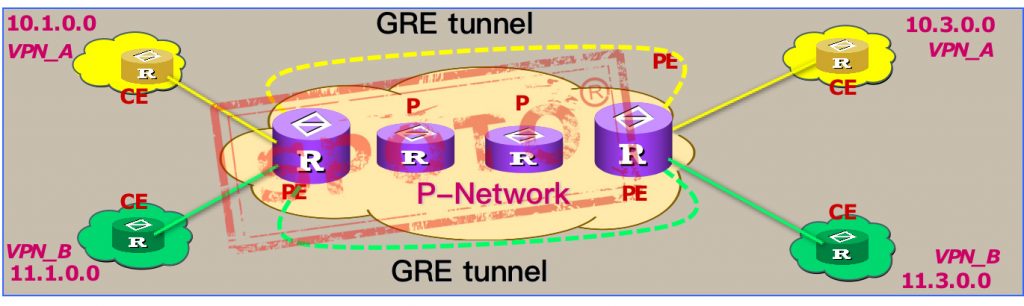
A separate PE router is prepared for each VPN. Any routing protocol can be run between PE and CE, regardless of other VPNs. Run BGP or other routing protocols between PE and P, and use routing attributes to filter. There is no need to configure any ACL, which greatly reduces the administrator’s configuration workload. Every VPN user must add a dedicated PE, which is too expensive.
Disadvantages: To prevent interworking between different CEs connected to the same PE, a large number of ACLs must be configured on the PE. Local routing conflict: How to distinguish the same route of different VPNs on the same PE?
All VPN user CEs are connected to the same PE. PEs and different CEs run different routing protocols or different processes of the same routing protocol. For example, the originating PE publishes VPN routes to the public network in OSPF. These routes are filtered on the PE at the end and then sent to the corresponding CE device. In order to avoid the leakage of routes between different VPN users, the shared route access method needs to configure a large number of ACLs to filter, which will have a very high performance and management cost Big burden.
A PE router is prepared for each VPN. Any routing protocol can be run between PE and CE, regardless of other VPNs. Run BGP between PE and P, and use routing attributes to filter.
Advantages: No need to configure any ACL.
Disadvantages: Every VPN user has a dedicated PE, which is too expensive.
Three problems with VPN.
Local routing conflict: How to distinguish the same route of different VPNs on the same PE?
The propagation problem of routes in the network: two identical routes are both propagated in the network, how to distinguish the receiver?
Packet forwarding problem: Even if the routing table conflict is successfully resolved, but when the PE receives an IP packet, how can it know which VPN to send to?
(1) Address conflict?
(2) “Provide a dynamically established tunnel technology”?
LSP in MPLS is a natural tunnel, and the establishment of this tunnel is
Based on the LDP protocol, it is exactly a dynamic label generation protocol.
(3) A protocol for dynamically establishing the tunnel bearer?
RIP, IS-IS, OSPF, EIGRP, BGP
Prerequisites
The main problems exist in the characteristics related to routing, so to solve these problems must be considered from the routing protocol. However, none of the existing routing protocols have the conditions to solve these problems, so they must be implemented by transforming the existing routing protocols. Choosing a suitable routing protocol to achieve transformation has become the first problem to be solved.
As a candidate routing protocol, it must be able to adapt to a huge number of VPN routes, and the protocol must have good scalability. And it requires the protocol to have good scalability. Qualified agreements must be based on TLV elements (ease of expansion).
OSPF is the most widely used routing protocol, but the scalability of this protocol is relatively poor,
Moreover, it requires a lot of calculations on the received LSA, and it is difficult to adapt to the huge number of VPN routing RIPs on the public network.
From the perspective of expansion, it is the scalability of TLV architecture, but the operation mechanism of RIP is not suitable for large networks. Other routing protocols also have corresponding unsuitable places,
In the end, there is only the BGP protocol. Many characteristics of BGP make it suitable for transformation to meet the problem of address overlap on the VPN network.
BGP
The number of VPN routes in the network may be very large, and BGP is the only routing protocol that supports a large number of routes;
BGP is based on TCP to establish a connection, which can exchange information between routers that are not directly connected, which eliminates the need for P routers to include VPN routing information;
BGP can carry any information appended to the route. As optional BGP attributes, any BGP router that does not understand these attributes will transparently forward them, which makes it very simple to propagate routes between PE routers.
Therefore, we can solve the three problems of VPN by combining MPLS and BGP, namely
Local routing conflict:
it can be solved by creating different routing tables on the same router, and different interfaces can belong to different routing tables. This is equivalent to simulating a shared PE as multiple dedicated PEs.
The problem of routing propagation in the network: You can add an identifier to this route during the routing process to distinguish different VPNs;
Packet forwarding problem:
Since the format of the IP packet cannot be changed, some information can be added to the IP header and the originating VPN will mark it so that the PE can forward the packet according to this mark when receiving the packet.












Comments