IP forwarding background:
In the early 1990s, with the rapid popularity of the Internet, due to the limitations of hardware technology at that time, routers using the longest matching algorithm and hop-by-hop forwarding increasingly became a major bottleneck limiting network forwarding performance, and fast router technology became a research hot spot. At the same time, ATM technology uses fixed-length labels and only needs to maintain a much smaller label table than the routing table, which can provide much higher forwarding performance than IP routing. This also led to widespread debate at the time, who will become the basis of next-generation network technology in the end: ATM and IP
IP technology is simple, but its performance is limited; ATM technology has high performance, but it’s complex Control signaling and high deployment costs are prohibitive.
Naturally, some people began to try to combine the advantages of ATM and IP technology, while maintaining the simplicity of IP technology, providing high performance similar to ATM technology. Many manufacturers have conducted similar research, and as a result, each manufacturer has proposed its own label switching solution.
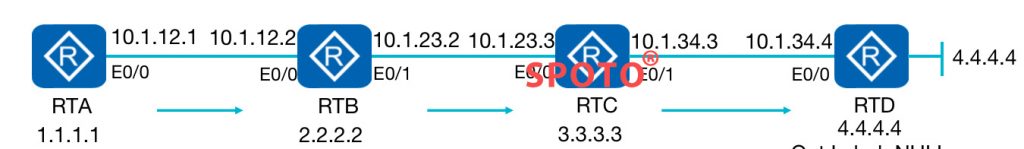
principle:
The router must decapsulate the received data frame and obtain the three-layer data. According to the destination IP of the three-layer data, the routing table is searched and the MAC address of the next-hop is encapsulated. The router searches for the route through the software-based CPU, then The CPU processes each IP packet using the longest mask matching principle, which is slower than the ASIC hardware chip used by the Layer 2 switch to look up the MAC address table.
switch:
Forwarding process–When receiving a Layer 2 data frame sent by its own physical layer, it learns and writes the MAC address table according to the source MAC, and looks up the MAC address table according to the destination MAC to decide whether to forward or flood.
Here, the switch looks up the MAC address table and forwards are done by the hardware ASIC chip. And the layer 2 switch has not done any encapsulation and decapsulation of the data frame and has not made any rewriting of the data frame.
Two tables
RIB routing information database, RIB stores routing entry information, RIB maintains the network topology and routing table for each protocol. This will include many routes to the same destination prefix.
For example, 1.0.0.0/32 is subnetted, 1 subnets
The summary information will appear only if they belong to the same main network and the main network numbers are the same.
If the subnet masks of the subnets are the same, the summarized network number is the main class network number, and the mask is the subnet mask. It also lists the number of entries containing subnets. If the subnet mask of the subnet is different, the summarized network number is still the main type of network number, but the mask defaults to the main type mask. Not only the number of subnets included but also the number of categories of subnet masks.
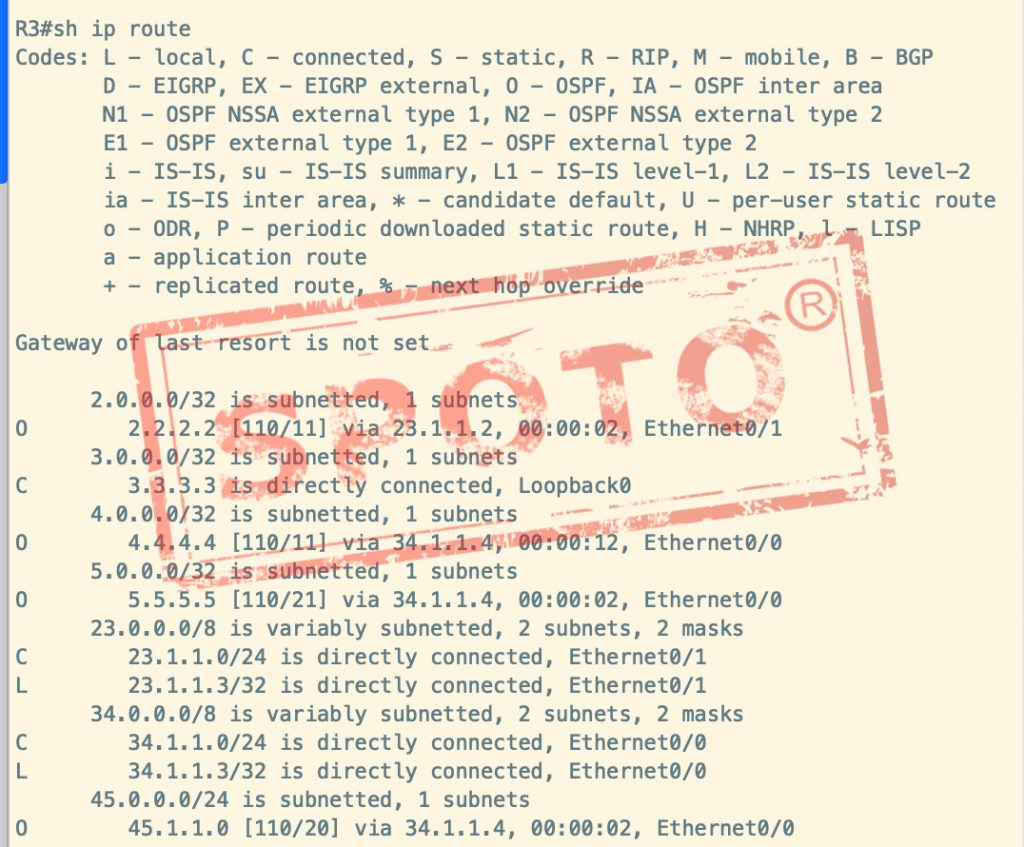
Routing-table
FIB Forwarding Information Base
FIB stores and forwards information, such as forwarding packets from interface f0 / 0 according to route entry A (sh ip cef detail), which table should be checked first for data forwarding?
In the process of data forwarding, first, check the fib table, and then check the routing table. The routing table is like a leader. Without specific implementation work, the fib table is a working brother.
The routing table may contain multiple routes to the destination address, but only the optimal route is taken in the forwarding table. The next hop of the routing table is the original next-hop, which is not necessarily directly reachable. FIB is used to direct forwarding, its next hop must be directly reachable. The process of finding the “direct next hop” based on the “original next hop” is called “routing iteration”.
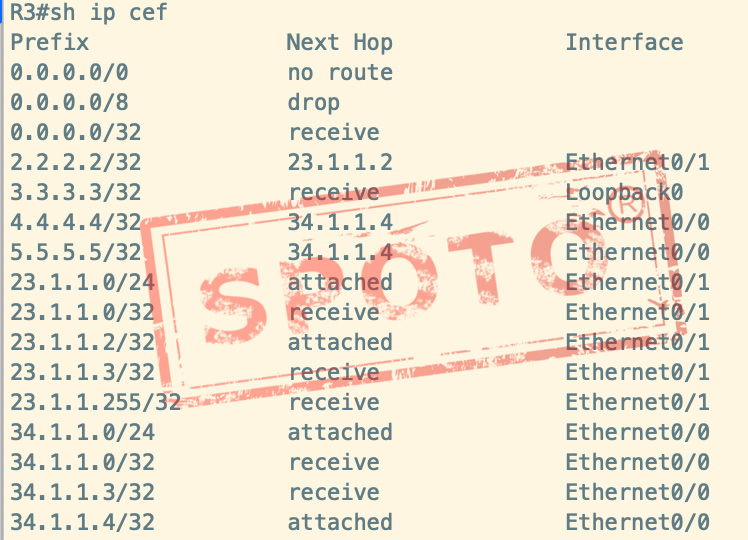
FIB-table
Defects of traditional IP switching
Each hop needs to perform route lookup, the router needs to have all routing entries
For example, if the router receives a packet with a destination IP of 192.168.1.1, there are three routes in the routing table: 192.168.0.0/16, 192.168.1.0/24, 192.168.1.1/32
Then the router must go through three searches and find the most accurate match 192.168.1.1/32 before it can forward the packet. And IP packets are not fixed-length. For computer hardware, processing variable-length data is very slow.
MPLS
Concept
The MPLS concept was originally proposed to improve forwarding efficiency. At that time, IP forwarding was mostly performed by software, and at least one longest match search was performed at each hop of the forwarding. The complicated operation resulted in a slow forwarding speed. Some manufacturers use the ATM forwarding method to simplify the IP forwarding process, which results in a new technology that combines the advantages of IP and ATM—MPLS. Under the conditions at the time, this can be said to be a great initiative, and its advantages are also obvious, but then there are many new technologies in the field of IP forwardings, such as the emergence of hardware forwarding and network processors, resulting in the MPLS speed advantage not being reflected In fact, pure MPLS forwarding has little use in practical applications. But MPLS is a “potential” technology that can be flexibly expanded. Many new applications are difficult to achieve by relying on pure IP forwarding, but MPLS can be implemented in combination with other technologies. For example, BGP / MPLS VPN, traffic engineering and other technologies are the results of the flexible expansion of MPLS. At present, MPLS is getting more and more attention, and it has become a hotspot of today’s network technology, and some new application requirements are also being realized by MPLS.
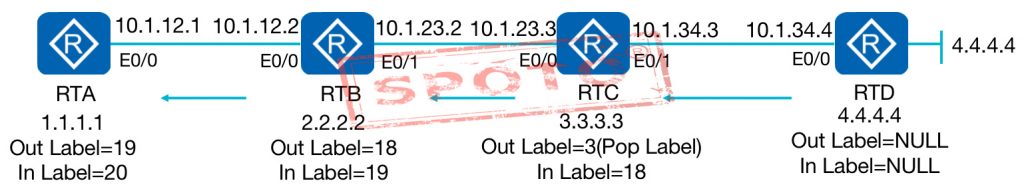
For example:
for the three routes 192.168.0.0/16, 192.168.1.0/24, 192.168.1.1/32, only one label needs to be assigned, such as label 20, which is called Forwarding Equivalence Class (FEC)
At this time, the router originally received the data packet whose destination IP is 192.168.1.1, and it needs to check the routing table three times before forwarding;
And now the labeled packet with label 20 is received, so the router will not look up the routing table, but look up the label forwarding table (LFIB) at once
Find the label assigned by other routers for 192.168.0.0 and exchange it directly. Speed up the forwarding efficiency of the router.
Two tables
LIB tag information library
The router generates a label locally for each IGP prefix and distributes it to LDP neighbors. It also receives labels distributed for network segments from other LDP neighbors. The router stores local labels and remote labels (sent to me by LDP neighbors) in the LIB. MPLS separates the router’s control plane from the forwarding plane
At the control level, routing protocols generate routing tables, and label protocols generate label information bases (LIB)
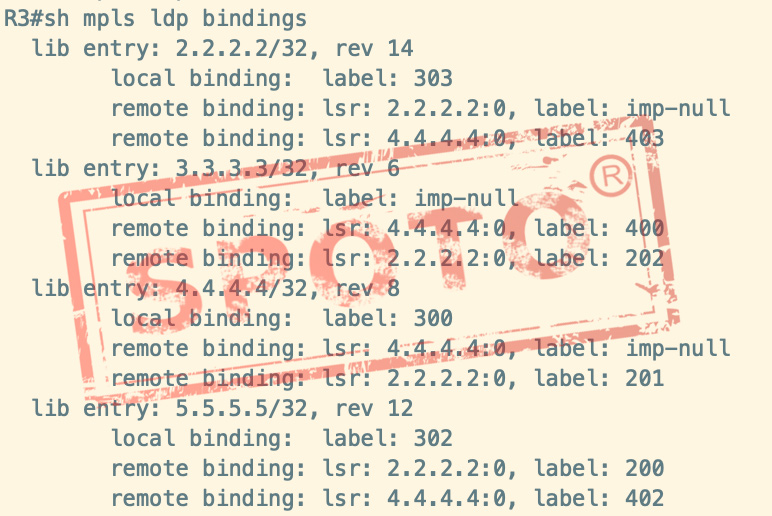
LIB
A label is assigned to each type of routing entry in the label information database, and all FECs from the forwarding plane of the router, which we call the label forwarding table (LFIB)
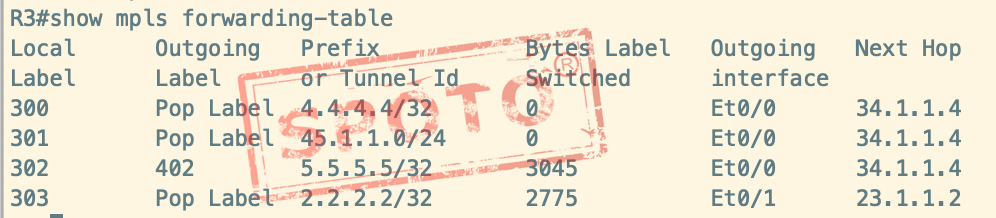
LFIB












Comments