At its core, F5 BIG-IP is primarily an Application Delivery Controller (ADC)—in other words, a sophisticated load balancer that optimizes, secures, and accelerates application traffic. Through its modular architecture, however, BIG-IP can be extended to include full-fledged firewall capabilities via the Advanced Firewall Manager (AFM) and Application Security Manager (ASM) modules. In other words, F5 is both—it is a best-in-class load balancer by default, and with the right modules becomes a high-performance network and application firewall.
Table of Contents
1. F5 BIG-IP: The Industry-Leading Load Balancer
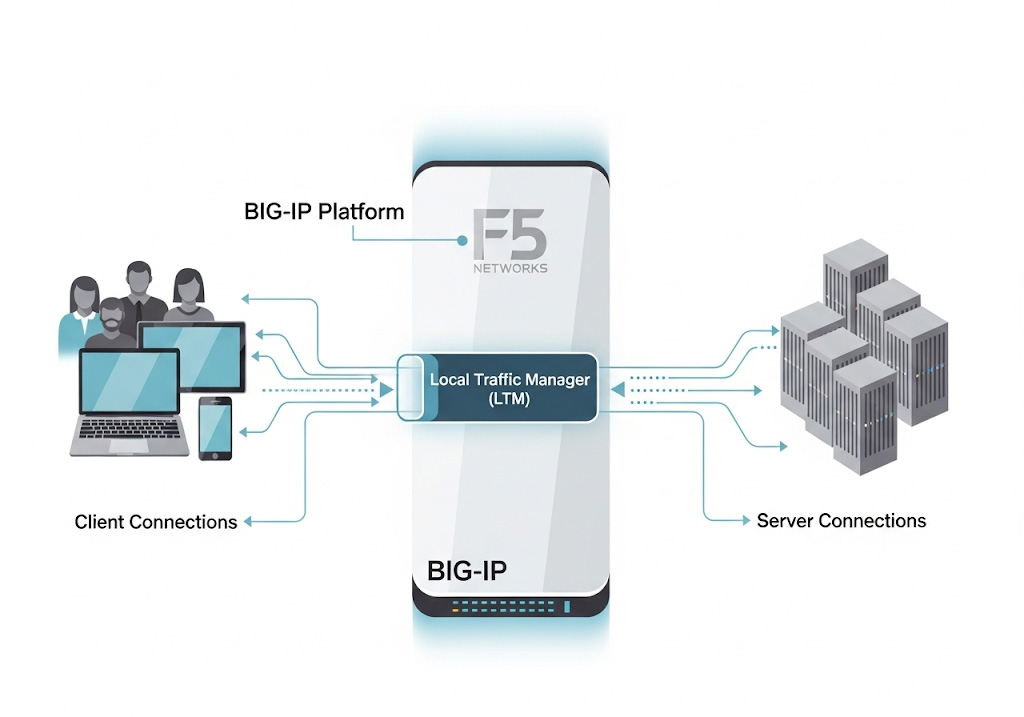
F5 Networks pioneered the ADC market with its BIG-IP platform, whose Local Traffic Manager (LTM) module remains the industry standard for load balancing and application delivery. LTM operates as a full proxy, terminating client connections and establishing new server connections to provide:
- Advanced load-balancing algorithms (round-robin, least connections, ratios, etc.)
- SSL/TLS offloading to reduce CPU load on application servers
- Health checks and dynamic server pool management
- Application acceleration (caching, compression, TCP optimizations)
- Global Server Load Balancing (GSLB) across data centers or clouds
This proxy-based architecture not only optimizes application performance and availability but also positions BIG-IP inline, making it the natural enforcement point for additional security services.
2. The Built-In “Mini-Firewall” in LTM
Even without purchasing dedicated security modules, LTM includes a Global Packet Filter—a basic Access Control List (ACL) engine that allows you to permit or deny traffic based on 5-tuple criteria (source/destination IP, ports, protocol). This capability earned BIG-IP early ICSA certification, enabling customers to enforce simple firewall rules at the ADC layer. However, these packet filters:
- Are global (single rule-set applies to all traffic)
- Offer limited logging and no context awareness
- Lack granular controls at the virtual-server or self-IP level
For organizations needing more granular or audit-ready firewalling, F5 offers dedicated modules.
3. Advanced Firewall Manager (AFM): A Full-Blown Network Firewall
BIG-IP AFM transforms the ADC into a high-performance, stateful, full-proxy network firewall that rivals dedicated firewalls in throughput and features:
- Contextual Rule Application
- Rules can be scoped globally, per route domain, per virtual server, per self-IP, or even on the management interface.
- Comprehensive Logging & Reporting
- Detailed denial logs, real-time DDoS dashboards, and customizable reports for forensic analysis.
- DDoS & Protocol Anomaly Protection
- Hardware-based signatures (over 100), volumetric and protocol-level attack mitigation before traffic reaches servers.
- Full State Tracking
- Maintains session state and deep subscriber/application awareness for precise connection control.
By integrating AFM directly into the BIG-IP dataplane (Traffic Management Microkernel), F5 achieves firewall performance that scales linearly on iSeries hardware or virtual editions—eliminating the bottleneck of chaining standalone devices.
4. Application Security Manager (ASM): The Layer-7 WAF
Where AFM stops at layer 4, BIG-IP ASM provides deep-packet inspection and protects against OWASP Top 10 threats:
- HTTP/S protocol validation
- Signature-based and behavioral attack detection
- Bot and API abuse mitigation
- Brute-force, credential stuffing, and form-based attack defenses
ASM complements AFM’s network-level filtering by policing application-layer traffic, making BIG-IP a comprehensive security platform when both modules are deployed.
5. Comparing Roles: Load Balancer vs. Firewall
| Feature | LTM Only | LTM + AFM/ASM |
|---|---|---|
| Primary Function | Distribute and accelerate application traffic | Distribute, accelerate, and fully secure traffic |
| Layer 4 Packet Filtering | Basic global ACL | Context-aware, granular firewall policies |
| Logging & Auditing | Minimal (syslog) | Detailed logs, compliance reporting |
| DDoS Mitigation | N/A | Advanced volumetric and protocol defenses |
| Layer 7 Inspection | Limited (rate shaping) | Full WAF capabilities via ASM |
| Management Complexity | Single device, fewer modules | Additional configuration but unified GUI |
6. Why Choose F5’s Integrated Approach?
- Consolidation of Infrastructure
- One BIG-IP box (physical or virtual) can replace multiple load balancers, DDoS scrubbing appliances, and firewalls—reducing management overhead and capex.
- Unified Policy & Visibility
- Single pane of glass for traffic steering, security events, and analytics—eliminating siloed logging and simplifying troubleshooting.
- Performance at Scale
- F5’s full-proxy architecture offloads CPU-intensive tasks (TLS, deep packet inspection) from servers, while ASICs on hardware models accelerate security and load-balancing functions.
- Extensible Licensing
- Pay-as-you-grow: start with LTM, then add AFM, ASM, DNS, APM modules as needs evolve—protecting initial investment.

















Comments