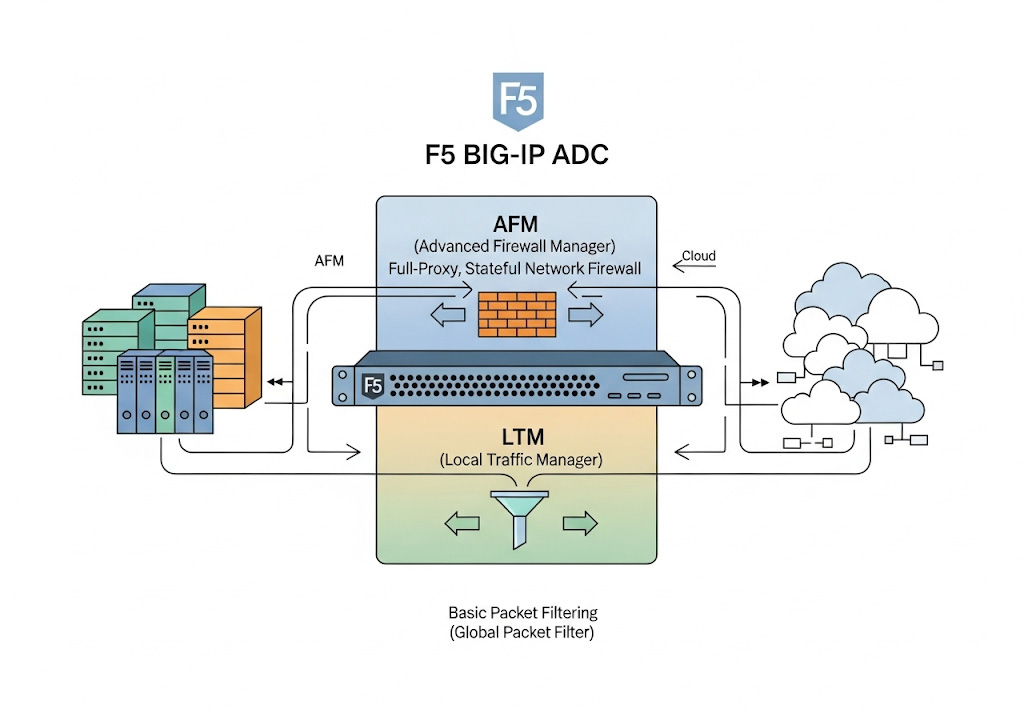
F5 BIG-IP integrates firewall functionality directly into its Application Delivery Controller (ADC) architecture, delivering a full-proxy, stateful network firewall through the Advanced Firewall Manager (AFM) module, while also offering basic packet filtering out of the box via the Local Traffic Manager (LTM) module’s Global Packet Filter. In practice, this means F5 can simultaneously distribute and accelerate application traffic and enforce granular, context-aware security policies—eliminating the need for separate, chained firewall devices.
Table of Contents
1. F5’s Firewall Portfolio: From Mini-Firewall to Full-Stack Security
F5’s firewall capabilities span several layers of the BIG-IP platform:
- Global Packet Filter (LTM) – A basic ACL engine permitting or denying traffic by IP/port across the entire device; ICSA-certified since 2011.
- Advanced Firewall Manager (AFM) – A high-performance, stateful, full-proxy network firewall with granular policy contexts, detailed logging, and DDoS mitigation.
- DDoS Hybrid Defender – Blends AFM’s firewalling with specialized DDoS scrubbing and SSL decryption for volumetric and application-layer attack protection.
- Next Edge Firewall CNF – A cloud-native network function delivering AFM-powered firewalling in Kubernetes and 5G environments.
This modular approach allows organizations to start with basic protection and easily scale up to comprehensive, full-stack security.
2. The “Mini-Firewall”: LTM’s Global Packet Filter
Out of the box, every BIG-IP LTM device includes the Global Packet Filter, which:
- Permits or denies traffic based on source/destination IP, ports, and protocol (5-tuple).
- Applies globally across all virtual servers and self-IP interfaces.
- Provides minimal logging via syslog.
Because it lives in the Traffic Management Microkernel (TMM), this packet filter imposes negligible performance overhead, but its global scope and lack of context limit its suitability for enterprises requiring audit-grade, per-application firewalling.
3. Advanced Firewall Manager (AFM): The Full-Proxy Network Firewall
3.1. Core Architecture
AFM transforms BIG-IP into a true stateful firewall by leveraging the same full-proxy dataplane that handles load balancing, SSL offload, and application acceleration. All traffic terminates on the device, allowing AFM to:
- Inspect and track TCP/UDP session state.
- Validate protocols using over 100 hardware-accelerated signatures.
- Mitigate DDoS at both volumetric and protocol levels before traffic reaches back-end servers.
By integrating firewalling into the ADC, F5 avoids performance bottlenecks common in chaining separate firewalls and load balancers.
3.2. Policy Contexts & Modes
AFM introduces multiple contexts for firewall policies, processed in the following order:
- Global – Rules applying to all traffic not caught by lower contexts.
- Route Domain – Scoped to specific network partitions.
- Virtual Server – Applied per VIP, controlling traffic on configured IP/port combos.
- Self-IP – Governs traffic entering or exiting the device via a specific interface.
- Management Port – Dedicated rules for administrative access.
Two modes define default behavior:
- ADC Mode (default allow) – All traffic is permitted unless explicitly denied; ensures no disruption upon AFM activation.
- Firewall Mode (default deny) – All traffic is blocked unless explicitly allowed; enforces strict, zero-trust policies.
Administrators can switch between modes and configure Global Drop/Reject actions for unmatched traffic, while still isolating management port rules.
3.3. Logging, Reporting & Analytics
AFM’s logging engine records detailed denial events, including context, rule name, packet details, and threat signature. Integrated dashboards and reports support compliance requirements and real-time incident response.
4. Integrating Firewalling with ADC Functions
4.1. Unified Policy Enforcement
Because AFM and LTM share the same Management UI and iControl REST API, security and delivery teams collaborate seamlessly:
- iRules can dynamically invoke AFM policy decisions based on application-level data.
- Profiles (SSL, HTTP, TCP) load in concert with firewall policies on the same virtual server.
- Centralized logging consolidates load-balancing metrics and security events.
This unification eliminates configuration drift and reduces operational overhead.
4.2. Performance & Scalability
F5’s Traffic Management Microkernel and hardware offload (iSeries) or optimized virtual performance ensure firewalling scales linearly with additional CPU cores or vCPUs. By terminating TLS sessions in hardware and offloading signature checks to ASICs, AFM maintains line-rate throughput even under heavy DDoS conditions.
5. Deployment Scenarios
| Environment | Recommended Modules | Key Benefits |
|---|---|---|
| Enterprise Data Center | LTM + AFM + ASM + GTM | Consolidated ADC + firewall + WAF + DNS |
| Service Provider | AFM + DDoS Hybrid Defender + S/Gi Firewall | Carrier-grade scale, subscriber security |
| Cloud & Hybrid | BIG-IP VE + AFM + Next Edge Firewall CNF | Consistent policies across on-prem & cloud |
| Kubernetes/5G | Next Edge Firewall CNF | Container-native firewalling, microservices protection |
In each scenario, leveraging F5’s modular licensing allows organizations to pay only for the security services they need, while maintaining a unified operational model.
6. Best Practices for F5 Firewall Integration
- Segregate Policy Contexts
- Apply strict default-deny rules at the Global context, then progressively allow traffic in lower contexts for specific services.
- Leverage iRules for Dynamic Security
- Use event-driven scripting to adjust firewall rules based on real-time application telemetry (e.g., rate-limit suspicious IPs).
- Automate with iControl REST & Ansible
- Integrate firewall policy deployment into CI/CD pipelines to ensure consistency across environments.
- Regularly Update Signatures & Threat Feeds
- Keep AFM protocol signatures and IP Intelligence feeds current to defend against emerging threats.
- Monitor and Tune
- Use BIG-IQ or third-party SIEM integrations to correlate firewall logs with network and application events for proactive threat hunting.

















Comments