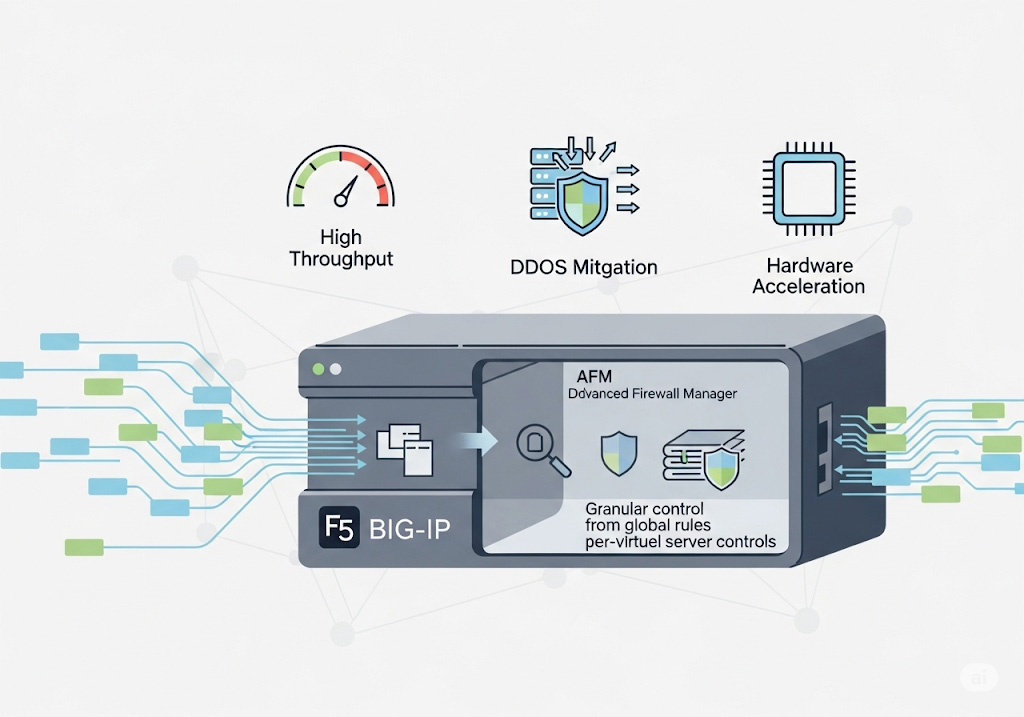
F5 BIG-IP’s firewall functionality is delivered through its Advanced Firewall Manager (AFM) module, which transforms the ADC’s full-proxy data plane into a stateful, context-aware network firewall. By terminating and inspecting all traffic, AFM enforces granular security policies—ranging from global rules to per-virtual server controls—while leveraging hardware acceleration for high throughput and DDoS mitigation. In addition, F5’s Web Application Firewall (WAF) capabilities (via the Application Security Manager module) provide deep application-layer protection against OWASP Top 10 threats. In essence, F5 firewalls work by proxying, inspecting, and controlling traffic at Layers 3–7, all within the same platform used for load balancing and SSL offload.
Table of Contents
1. Fundamentals of Firewall Operation
Before diving into F5’s implementation, it’s helpful to recap how traditional firewalls work:
- Packet Inspection & Rules
- Firewalls inspect each network packet entering or leaving a network interface, evaluating headers (source/destination IP, ports, protocol) against a set of security rules to allow, deny, or drop the packet.
- Stateful Connection Tracking
- Modern firewalls maintain a state table of active connections (TCP streams, UDP “flows”), enabling them to make context-aware decisions. If a new packet belongs to an existing session in the state table, it is handled according to the session’s established permissions rather than fresh rule evaluation.
- Proxying & Deep Inspection
- At higher OSI layers, proxy firewalls (e.g., application-level gateways) terminate client connections, fully parse protocol semantics, and re-originate connections to back-end servers, enabling granular inspection of payloads for application-specific threats.
- Layered Defenses
- Organizations often deploy a combination of packet filters, stateful firewalls, and application-layer gateways (including WAFs) to create a defense-in-depth security posture, ensuring threats at every layer are inspected and mitigated.
2. F5’s Full-Proxy Architecture: The Foundation
F5 BIG-IP is built on a full-proxy data plane called the Traffic Management Microkernel (TMM). Unlike traditional “bump-in-the-wire” devices, TMM terminates every client session, enabling:
- SSL/TLS Offload
- Advanced Load Balancing
- Protocol Optimization & Acceleration
- Traffic Manipulation via iRules
By centralizing all traffic, TMM becomes an ideal enforcement point for firewall functions—every packet and HTTP request must pass through it, allowing complete visibility and control.
3. Advanced Firewall Manager (AFM): Turning ADC into a Network Firewall
3.1 Stateful, Context-Aware Policy Engine
AFM leverages TMM’s full-proxy model to deliver a true stateful firewall:
- Connection Termination & State Tracking
- Each TCP/UDP session terminates on the BIG-IP, and AFM records its state in a high-performance state table. Returning packets are matched against these entries, ensuring accurate, context-aware filtering.
- Protocol Validation & Signatures
- AFM includes over 100 hardware-accelerated protocol signatures to detect anomalies and protocol-based attacks (e.g., malformed DNS, TCP scans).
- DDoS Mitigation
- Inline volumetric scrubbing, SYN-cookie protection, and rate-limit policies defend against state-exhaustion and network floods at Layers 3–4.
3.2 Granular Policy Contexts
AFM policies can be scoped at multiple levels, processed in this order:
- Global – Default rules for all traffic not matched elsewhere.
- Route Domain – Isolation of traffic in segmented network namespaces.
- Virtual Server – Policies per VIP (IP:port), enabling per-application controls.
- Self-IP – Rules on specific device interfaces for north-south and east-west traffic.
- Management Port – Dedicated policies for device administration access.
Each context layer allows distinct default actions (allow or deny), letting administrators adopt a “default deny” posture at the global level while selectively permitting known services.
3.3 Policy Modes: ADC vs. Firewall
AFM offers two operational modes:
- ADC Mode (Default Allow)
- Emulates a benign ADC: traffic flows unless explicitly blocked. Ideal for gradual adoption without service interruption.
- Firewall Mode (Default Deny)
- Enforces strict security: all traffic is blocked unless expressly allowed, supporting zero-trust networks.
3.4 Logging & Analytics
AFM’s logging framework captures detailed denial logs (source/destination, protocol, dropped packet bytes, rule invoked) and feeds them into:
- BIG-IP dashboards for real-time monitoring
- BIG-IQ Security for centralized log aggregation and forensic analysis
- SIEM integrations via syslog or REST APIs
This deep visibility supports compliance audits and rapid incident response.
4. Application Security Manager (ASM): Web Application Firewall
While AFM defends the network layers, F5’s ASM module provides Layer 7 WAF capabilities:
- Reverse-Proxy Inspection
- ASM sits inline as a reverse proxy, parsing HTTP/S requests to detect SQL injection, XSS, file inclusion, and other OWASP Top 10 attacks.
- Signature & Behavioral Analysis
- Combines known-attack signatures with dynamic profiling to uncover zero-day exploits and anomalous traffic patterns.
- Bot & API Protection
- Differentiates between human users and automated clients, throttling or blocking malicious bots and API abuse.
- Adaptive Learning
- Machine learning assists in auto-tuning policies, reducing false positives and easing operational burden.
By co-hosting ASM with AFM and LTM on the same BIG-IP platform, organizations gain a single control plane for network, transport, and application security.
5. Integrating Firewall with ADC Services
5.1 Unified Management
- Shared GUI & iControl REST API
- Single host for SSL certificates, traffic profiles, and security policies
- iRules can invoke AFM or ASM decisions dynamically, based on HTTP headers, cookies, or application context.
5.2 Performance at Scale
- TMM’s multicore architecture and ASIC offloads ensure that adding firewall rules does not degrade throughput.
- On hardware platforms (iSeries), dedicated silicon accelerates TLS decryption and signature checks, enabling line-rate firewalling even under DDoS attack.
6. Deployment Scenarios & Best Practices
| Scenario | Modules | Key Considerations |
|---|---|---|
| Data Center | LTM + AFM + ASM | Consolidate load balancing & full-stack security; enforce per-app policies. |
| Service Provider | AFM + DDoS Hybrid | Scale to millions of sessions; protect subscriber edge from volumetric attacks. |
| Cloud & Hybrid | BIG-IP VE + AFM | Enforce consistent policies across on-prem and public cloud; leverage autoscaling. |
| Kubernetes / 5G | Next Edge Firewall CNF | Container-native firewalling; integrate with service mesh and microservices. |

















Comments