Table of Contents
What Is F5 BIG-IP?
Overview of BIG-IP
F5 BIG-IP is a sophisticated Application Delivery Controller (ADC) that provides a suite of services for traffic management, security, and performance optimization. Deployed at the edge of networks, BIG-IP ensures that applications are fast, secure, and available to users—whether on-premises, in the cloud, or in hybrid environments.
At its core, BIG-IP combines:
- Load balancing
- SSL offloading
- Application firewall
- Access control
- Traffic shaping
- DNS services
History and Evolution
F5 Networks introduced BIG-IP in the late 1990s as a load balancing appliance. Over time, the platform evolved into a modular system, expanding into security (WAF, DDoS protection), identity access, and advanced global traffic management. Today, it supports virtual editions (VE) and cloud deployments alongside traditional hardware (iSeries, VIPRION).
Core Architecture of F5 BIG-IP
Traffic Flow and High-Level Workflow
The core of BIG-IP is its ability to intercept and intelligently route traffic based on user-defined rules and health monitoring.
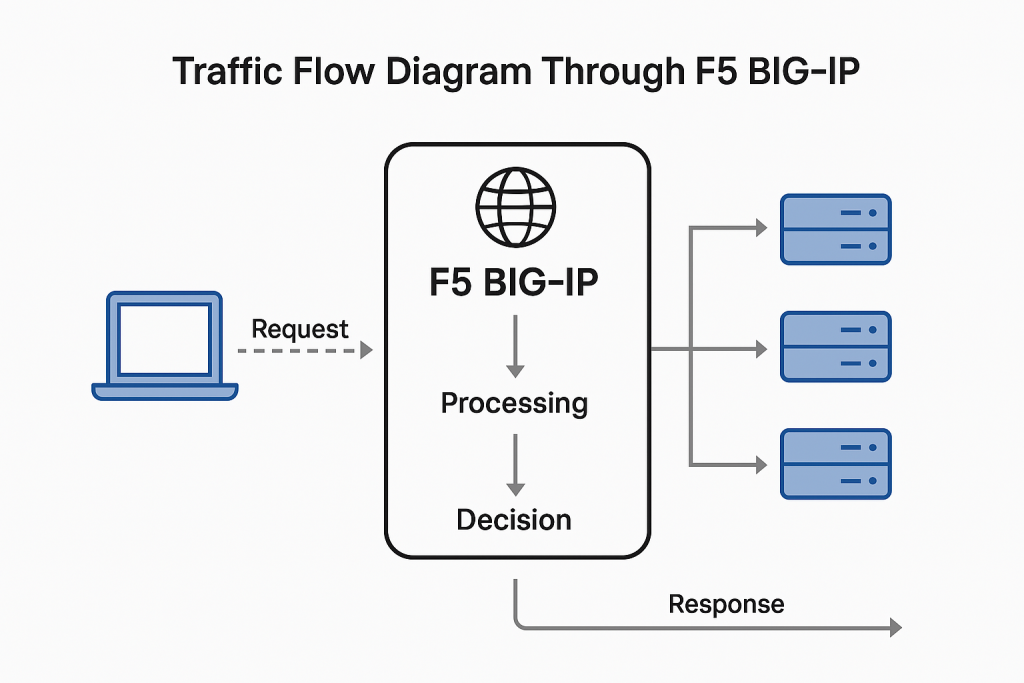
Here’s how traffic typically flows:
- A client sends a request to an application’s IP (which is actually a Virtual Server on the BIG-IP).
- The Virtual Server processes the request using BIG-IP’s core OS, TMOS.
- BIG-IP determines the best pool member (backend server) based on load and health checks.
- The request is forwarded to the selected pool member.
- The response follows the reverse path, optionally optimized or modified.
BIG-IP Operating System (TMOS)
The Traffic Management Operating System (TMOS) is F5’s proprietary OS. It underpins all BIG-IP modules and provides:
- Full TCP stack
- Deep packet inspection
- API-based programmability
- High-performance traffic handling
Virtual Servers, Nodes, Pools, and Pool Members
- Virtual Server: The frontend IP that clients connect to.
- Node: A backend server’s IP.
- Pool: A collection of nodes.
- Pool Member: A node + service port (e.g., 192.168.1.10:80).
iRules and iApps
iRules: TCL-based scripts to program traffic behavior.
iApps: Templates for application deployment and configuration.
Key Modules and Their Functions (Beginner-Friendly)
F5 BIG-IP is modular, which means you can choose the specific features you need. Each module adds new capabilities to help manage, protect, or optimize your application traffic. Here are the most important ones, explained simply:
LTM – Local Traffic Manager (The Brains of BIG-IP)
The LTM is the most commonly used BIG-IP module. It acts like a traffic cop, deciding which backend server should handle a user’s request.
🔧 What It Does:
- Balances traffic across servers (load balancing)
- Checks if servers are healthy before sending traffic
- Can reroute traffic if a server goes down
✅ Example Use:
If you have 3 servers running your website, LTM can split incoming traffic evenly or based on how busy each server is.
ASM – Application Security Manager (The Shield)
The ASM is like a Web Application Firewall (WAF). It protects your apps from common attacks such as SQL injections, cross-site scripting (XSS), or bots.
🔐 What It Does:
- Blocks malicious requests
- Prevents attackers from exploiting your app
- Helps meet security compliance like PCI-DSS
✅ Example Use:
Protecting a login page from brute force or script-based attacks.
APM – Access Policy Manager (The Gatekeeper)
APM handles secure user access to apps. It’s often used for VPNs or remote access to internal applications.
🔐 What It Does:
- Manages user authentication (e.g., login with AD, SSO)
- Controls who can access which app or part of the network
- Offers multi-factor authentication (MFA)
✅ Example Use:
Allowing employees to securely access apps from outside the office.
GTM – Global Traffic Manager (The Traffic Director)
GTM, now often called BIG-IP DNS, controls traffic across multiple data centers or geographic locations.
🌍 What It Does:
- Routes users to the nearest or healthiest data center
- Balances DNS requests globally
- Helps with disaster recovery
✅ Example Use:
If you have one app in the US and one in Europe, GTM can send European users to the EU server for faster access.
AFM – Advanced Firewall Manager (The Bodyguard)
AFM is a network firewall built for high-speed environments. It protects against DDoS attacks and unwanted traffic at the network level.
🔥 What It Does:
- Filters bad IPs or countries
- Stops floods of fake traffic
- Protects backend systems from being overwhelmed
SSL Offloading and Acceleration
BIG-IP can handle the encryption/decryption of HTTPS (SSL/TLS) traffic, which is usually resource-heavy.
🚀 Why It’s Useful:
- Frees up backend servers to focus on app logic
- Speeds up encrypted connections
✅ Example Use:
BIG-IP decrypts traffic, checks it for threats (via ASM), then re-encrypts it before forwarding it to the app.
Want a quick visual to connect it all?
Here’s a simplified analogy:
| BIG-IP Module | Acts Like… | Helps With… |
|---|---|---|
| LTM | Traffic Cop | Directing traffic to healthy, fast servers |
| ASM | Security Guard | Stopping hackers and malicious requests |
| APM | Door Bouncer | Allowing only authorized users inside |
| GTM | GPS Navigator | Sending users to the best data center |
| AFM | Bodyguard | Protecting the network from attacks |
How F5 BIG-IP Works in a Real-World Scenario
Let’s imagine you’re hosting a public website, like www.mycoolapp.com, and you want it to:
- Stay online even if one of your servers goes down
- Load quickly for users
- Be protected from common web attacks
This is where F5 BIG-IP comes in!
🧠 Step-by-Step: What Happens When Someone Visits Your Website
Here’s a simplified version of how BIG-IP handles a visitor request.
👨💻 1. A User Types in Your Website (Client → Internet)
The user opens a browser and types www.mycoolapp.com.
🌐 2. The DNS Resolves to BIG-IP’s Public IP
Instead of pointing directly to a web server, your DNS entry points to a Virtual Server on the BIG-IP.
www.mycoolapp.com → 203.0.113.25 (BIG-IP)
🚦 3. BIG-IP Virtual Server Accepts the Request
BIG-IP listens on that public IP (203.0.113.25). When the request arrives:
- It checks the status of the backend servers
- Applies security rules (e.g., via ASM)
- Checks traffic policies (via iRules or LTM)
📤 4. BIG-IP Chooses the Best Server (Load Balancing)
Let’s say you have 3 backend web servers:
- 10.0.0.1
- 10.0.0.2
- 10.0.0.3
BIG-IP checks which one is:
- Healthy (via health checks)
- Least busy (based on load balancing algorithm)
And forwards the request accordingly.
🔒 5. Security and Optimization Happen
Depending on your configuration:
- SSL is terminated (BIG-IP decrypts the HTTPS)
- ASM checks the request for suspicious patterns
- APM may require the user to log in or pass MFA
📨 6. Server Sends Response → BIG-IP Sends It Back to the User
The web server sends the page content back to BIG-IP. Then BIG-IP:
- Re-encrypts the data (if SSL was offloaded)
- Applies any caching or optimization
- Sends it back to the user’s browser
🖼️ Visualizing the Flow
Here’s a basic text-based diagram of how traffic moves:
[User Browser]
|
v
[ BIG-IP Virtual Server (Public IP) ]
|
v
[ Security Checks (ASM, APM) ]
|
v
[ Load Balancer (LTM chooses best server) ]
|
v
[ Web Server 1 / 2 / 3 ]
|
^
[ Response goes back through BIG-IP ]
|
v
[ User sees the website ]
🧪 Real-World Example: Hosting a Web App
Let’s say you run an e-commerce site during a big holiday sale.
Without BIG-IP:
- All users hit the same server.
- If the server is overloaded or crashes, the site goes down.
- You’re vulnerable to attacks or slowdowns.
With BIG-IP:
- Traffic is distributed across multiple servers.
- If one server fails, BIG-IP reroutes users automatically.
- ASM protects your site from malicious bots or injection attacks.
- SSL offloading keeps your servers focused on delivering the app, not decrypting HTTPS.
🔧 Sample Load Balancing Policy (LTM)
Here’s a simple example of how BIG-IP might be configured to balance traffic using the round-robin method:
ltm pool web_pool {
members {
10.0.0.1:80 {}
10.0.0.2:80 {}
10.0.0.3:80 {}
}
load-balancing-mode round-robin
monitor http
}

















Comments