Introduction
CompTIA Security+ is one of the most popular entry-level cybersecurity certifications – but what does it actually do for your career? If you’re an IT professional in the U.S. wondering “What jobs can I get with a Security+ certification?”, you’re not alone. Many people obtain Security+ to break into security or advance from their current IT role, and they want to know the real opportunities it unlocks. The short answer is: Security+ can open the door to a variety of roles ranging from help desk and junior analyst positions up to more advanced engineering or consultant jobs as you gain experience. In this article, we’ll explore why employers value the Security+ cert, which entry-level jobs it prepares you for, how you can grow into mid-career roles (and which additional certs can help), typical salary ranges for these positions, and tips to land a job even if you don’t have much hands-on experience. By the end, you’ll see how Security+ can be a stepping stone to a long and rewarding IT security career.
Table of Contents
Why CompTIA Security+ Is So Valuable to Employers
Earning your Security+ certification proves you have a solid foundation in cybersecurity knowledge – and employers take notice. In fact, CompTIA Security+ is considered “the industry standard” for validating core security skills needed for any cybersecurity role. It covers essential topics like network security, threats and vulnerabilities, access controls, incident response, and governance. This broad coverage means a Security+ holder is conversant in the fundamental concepts required to protect an organization’s systems.
One big reason Security+ is valued is its wide recognition and compliance with government standards. It’s approved by the U.S. Department of Defense to meet DoD 8140/8570.01-M requirements, which means many federal jobs and contractors require Security+ for IT security roles. Companies in the defense industry (like Northrop Grumman and MTSI) specifically look for Security+ when hiring. Even outside of government, hiring managers often use certifications to screen candidates – an IDC report found 96% of HR managers rely on IT certs as criteria during recruitment. Having Security+ on your résumé can thus help get you past HR filters.
Another reason employers prioritize Security+ is the current cybersecurity talent shortage. There were over 63,000 job listings in the past year asking for CompTIA Security+ certification – second only to the CISSP among security certs. This high demand signals that organizations see Security+ as a baseline qualification for many roles. It reassures them that you understand security best practices and can hit the ground running in an entry-level cybersecurity job. As CompTIA’s director James Stanger puts it, Security+ “sets you up for an early-career cybersecurity job role,” giving you a well-rounded understanding of how to protect data and systems.
Finally, Security+ isn’t just theory – it includes performance-based questions that test practical skills. Employers know a certified Security+ professional has proven they can identify and mitigate threats in real scenarios, not just memorize facts. All these factors make Security+ holders attractive to organizations looking to build out their security teams.
Entry-Level Job Roles You Can Get with Security+
What actual jobs can you land once you have CompTIA Security+? At the entry level, Security+ prepares you for roles where you’ll be monitoring, configuring, or securing IT systems under the guidance of more senior staff. Below we break down some common entry-level job titles, what you do in those roles, and why Security+ is relevant.
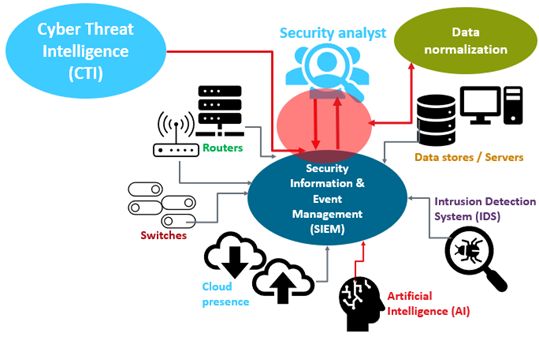
A simplified SOC (Security Operations Center) architecture shows how logs from endpoints, network devices, and security tools feed into a central SIEM platform that security analysts monitor. The SIEM correlates data (often aided by threat intelligence feeds and AI) and generates alerts. Data normalization and filtering ensure the SOC team gets actionable information from a flood of raw logs, enabling them to detect incidents and respond effectively.
Systems Administrator (with Security Duties)
A Systems Administrator is responsible for the day-to-day maintenance of an organization’s computers and servers. In a smaller company, this might be your primary role, and in a larger company it might overlap with dedicated security staff. Typical sysadmin duties include:
- Managing hardware/software: Ensuring that servers, PCs, and applications are configured correctly and working as intended. This includes installing updates and patches to keep systems secure and stable.
- User administration: Creating and managing user accounts, permissions, and access rights to various systems. For example, a sysadmin makes sure employees have appropriate access while maintaining principle of least privilege for security.
- System monitoring and backups: Monitoring system performance, verifying backups, and troubleshooting issues to minimize downtime. Often, this involves checking logs and system alerts – tasks where Security+ knowledge of what’s “normal” vs. suspicious comes in handy.
- Enforcing security policies: In many organizations, the sysadmin also implements security measures such as configuring firewall rules on servers, setting password policies, and ensuring antivirus/endpoint protection is running.
Why Security+ helps: Security+ equips a sysadmin with knowledge of fundamental security practices – like secure configurations, identity management, and incident handling – that are now a routine part of a sysadmin’s job. For example, when updating server software, a Security+ certified admin will be mindful of patching security vulnerabilities promptly. Employers often require or prefer Security+ for systems administrator positions to ensure the admin can proactively secure the IT infrastructure (the U.S. DoD even mandates it for many admin roles). In short, Security+ makes you a more security-conscious sysadmin, which is invaluable as cyber threats target even basic IT systems.
Network Administrator
A Network Administrator focuses on the organization’s network hardware and connectivity – think routers, switches, firewalls, and network segments. In this role, you ensure that the company’s LAN/WAN and internet connection are reliable and secure. Key responsibilities include:
- Network operation and uptime: Monitoring the network to ensure data can flow between devices and sites. This involves configuring network devices (routers, switches, Wi-Fi) and troubleshooting outages or bottlenecks.
- Implementing network security: Setting up and maintaining firewalls, VPNs, and intrusion detection systems. A network admin with Security+ understands how to tighten router/switch configurations (e.g. disabling unused ports, enabling encryption) and recognize signs of attacks like unusual traffic patterns.
- Upgrades and patches: Applying firmware updates to network devices and upgrading equipment when needed. Just like with systems, keeping network gear updated is critical to patch security holes.
- User connectivity and permissions: Managing network access for employees – for instance, creating VLANs or network segments to separate sensitive systems, and adjusting ACLs (access control lists) or firewall rules to allow legitimate traffic while blocking threats.
Why Security+ helps: Network administrators benefit from Security+ knowledge of network-based threats and defenses. The certification covers topics like secure network design, wireless security, and protocols (e.g. understanding why using SSH instead of Telnet is important, or how ARP spoofing and DDoS attacks work). This means as a Security+-certified network admin, you can not only keep the network running, but also lock it down against attackers. Employers value this because many breaches originate from network weaknesses. With Security+, you can better implement firewalls, VPN encryption, and monitor logs from network devices for suspicious events. In practical terms, you might be the one reviewing the firewall logs or SIEM alerts for unusual inbound connections – tasks right out of the Security+ curriculum. It’s no surprise many job listings for network administrators list Security+ as either required or “nice to have,” especially if the role is in a security-sensitive environment.
Security Administrator / IT Security Specialist
Some organizations have entry-level roles specifically titled Security Administrator or IT Security Specialist. These positions are focused on implementing and maintaining security tools and policies. Think of it as a junior cybersecurity generalist. In this job, you might:
- Maintain security systems: Manage tools like firewalls, IDS/IPS, antivirus consoles, and vulnerability scanners. For example, a security admin will update firewall rules, deploy endpoint protection to new PCs, and ensure the IDS sensors are functioning. They are the custodian of these defense technologies.
- User access management: Overlap with sysadmin duties by administering identity and access management systems (directory services, multi-factor authentication, etc.). You ensure users have the correct security clearances and remove or update access as roles change.
- Monitor for intrusions: Regularly review security dashboards (SIEM, antivirus alerts, etc.) and investigate minor security incidents. A security specialist might be the one who notices a malware alert from an endpoint and takes initial steps to quarantine the machine.
- Security policy enforcement: Make sure that employees follow security policies. You might run password audits, check for rogue devices on the network, or verify encryption is used where required. There’s also a lot of documentation in this role – logging incidents, updating security procedures, and assisting in compliance audits.
Why Security+ helps: Security+ directly maps to this role – it provides the baseline know-how for using security tools and understanding threats. The cert covers topics like IDS vs. IPS, firewall types, access control models, and basic cryptography, all of which a security admin uses daily. Employers hiring a Security Administrator often expect candidates to have Security+ because it validates you can “speak the language” of cybersecurity and won’t need training on fundamentals. For instance, when configuring an intrusion detection system, a Security+ holder will already understand what signature-based detection is or what constitutes suspicious network behavior. In short, Security+ gives you credibility and confidence to operate as an organization’s go-to junior security person.
Junior Security Analyst (SOC Analyst Tier 1)
One of the most common entry-level Security+ jobs is a Security Analyst in a Security Operations Center. Often called a SOC Analyst Level 1, Cybersecurity Analyst, or similar, this role is on the front lines of cyber defense. As a junior security analyst, your primary duty is to monitor and triage security alerts. Here’s what the job entails:
- Security monitoring: Keep an eye on the SIEM (Security Information and Event Management) system for incoming alerts from various sources – firewalls, IDS, servers, etc. When an alert triggers (say, a possible malware infection or unauthorized access attempt), you investigate it. This could mean pulling up log data, checking the affected system, and determining if it’s a real threat or a false positive.
- Incident investigation: For actual incidents, you follow playbooks to analyze the scope and impact. For example, if the SIEM shows a brute-force attack on a server, you might examine the server’s authentication logs to identify the source IP and how many attempts occurred. You’ll document findings and escalate to a senior analyst or incident responder if it’s serious.
- Threat detection and response: Level 1 analysts often handle straightforward response actions. This could include isolating a workstation that’s infected (remotely removing it from the network), resetting compromised user passwords, or blocking an IP address at the firewall. Think of it as cybersecurity first aid – address the immediate issue and hand off to higher tiers if needed.
- Reporting and improvement: After incidents, you may compile reports and also suggest tweaks to security controls. For instance, if you saw a wave of phishing emails get past a filter, you might recommend updating the email rules or training users.
Why Security+ helps: Security+ certification aligns extremely well with a junior analyst’s knowledge needs. It teaches you about various attack types (so you recognize them in alerts), incident response processes, and how logging and monitoring works. Having Security+ proves you know the basics of threat analysis and incident handling, which is exactly what a SOC analyst does. Many employers make Security+ a prerequisite for SOC jobs because it’s a benchmark for entry-level cybersecurity roles. With Security+, you’re equipped to understand SIEM alerts, read log files, and follow incident response steps. For example, Security+ covers analyzing log output from tools like Windows Event Viewer or Linux syslogs – skills directly useful when combing through events during an investigation. Below is a simple example of a Linux command a junior analyst might use to hunt for suspicious activity:
# Example: Find recent failed login attempts on a Linux server
sudo grep -i "failed password" /var/log/auth.log | tail -5
The above command searches the authentication log for any “failed password” entries (common when someone mistypes a password or an attacker is brute-forcing logins) and shows the last 5 occurrences. A Tier 1 SOC analyst might use such commands to quickly check if an account had multiple failed logins – a possible sign of a brute force attack.
Armed with Security+, you’ll not only know how to run basic commands or SIEM queries to investigate issues, but you’ll understand what you’re looking for and why it matters. This ability to connect the dots – e.g., “multiple failed logins from a single foreign IP = brute force attempt” – is exactly what employers want in a junior analyst.
IT Auditor (Junior)
A Junior IT Auditor (or Information Security Auditor) is a role that combines IT know-how with compliance and oversight. While not as technical as a SOC analyst, it’s an entry point into security especially in organizations that emphasize compliance (like finance, healthcare, or government). As an IT auditor, you’ll:
- Review systems and processes for compliance: Verify that the organization’s IT systems follow security policies, standards, or regulations. For instance, you might audit user account management to ensure old accounts are disabled, or check that servers have required security patches installed.
- Conduct risk assessments: Identify and document potential risks in the IT infrastructure. Maybe you’ll note that a database server has weak password settings or that a department isn’t encrypting sensitive data, and flag these as findings.
- Recommend improvements: After audits, you suggest remediation steps like “enable multi-factor authentication for remote logins” or “implement a stricter password policy” if you found gaps. Essentially, you act as an internal security consultant, advising how to bolster defenses.
- Prepare audit reports: A large part of the job is writing up what you found in a clear, organized manner. You may present these reports to management or external auditors. Attention to detail is key – you need evidence for each control you test.
Why Security+ helps: Security+ gives you a broad understanding of security controls and best practices, which is exactly what you’ll be evaluating as an auditor. For example, Security+ covers topics like identity management, encryption, and security policy – all of which map to common audit checkpoints. If you learned about the principles of least privilege or data encryption standards in Security+, you can apply that knowledge when checking if a business unit is appropriately restricting access or encrypting laptops. Employers appreciate Security+ for IT audit roles because it ensures you have up-to-date security knowledge to inform your audit work. In fact, many IT auditors eventually pursue the CISA (Certified Information Systems Auditor) certification, but Security+ is a great foundation to get started. It demonstrates you understand both the technical and administrative sides of security. As a junior auditor, you might not configure firewalls or hunt threats daily, but you need to speak the language of those who do – Security+ helps you confidently discuss topics with system admins and security engineers during your audits. (Plus, if you ever transition from auditing to a more hands-on security job, you’ll have that core Security+ knowledge ready to go.)
Junior Penetration Tester (Ethical Hacker)
Many people get excited about the prospect of becoming a Penetration Tester (an ethical hacker who tests an organization’s defenses). It’s indeed a possible path with Security+, though typically you’ll need to build additional skills. As a Junior Pentester, you would:
- Conduct vulnerability scans: Use tools to scan networks and applications for known vulnerabilities. This might involve running Nessus or OpenVAS and interpreting the results to find weaknesses that need manual testing.
- Perform controlled attacks: Under supervision, execute simulated attacks on systems (with permission, of course). For example, you might try SQL injection on a test web application, attempt to crack weak passwords, or see if you can gain unauthorized access to a system. This is done to identify security holes before real hackers do.
- Document and report findings: Just like an auditor, a big part of pen testing is writing up what you discovered, how you exploited it, and how to fix it. Junior pentesters often assist senior testers in creating detailed penetration test reports that outline each vulnerability, its impact, and remediation steps.
- Learn specialized tools: You’ll be hands-on with tools like Metasploit (for exploiting vulnerabilities), Nmap (network scanning), Burp Suite (web app testing), and others. Over time, you develop a hacker mindset to creatively think of attack vectors.
Why Security+ helps: Security+ by itself is not a hacking certification – however, it covers foundational knowledge that every ethical hacker needs. You learn about common vulnerabilities (e.g., unpatched software, weak configurations) and attacks (like buffer overflows, denial-of-service, man-in-the-middle). This gives you the theoretical backdrop to understand what you’re actually exploiting as a pentester. For instance, Security+ teaches you the basics of cryptography and network protocols, so when you later encounter something like an outdated SSL encryption or an open port, you know why it might be vulnerable. Many junior pen testers start with Security+, then supplement it with more focused certifications such as CompTIA PenTest+, CEH (Certified Ethical Hacker), or eventually OSCP (Offensive Security Certified Professional) as they move to mid-level. Employers hiring entry-level pentesters recognize that Security+ shows you have the broad security knowledge and professionalism (ethical guidelines are part of the cert) necessary for the role. Keep in mind that pure junior pentester roles are less common than analyst roles – often, penetration testing is a mid-career move after you’ve gained general IT/security experience. But Security+ is absolutely a stepping stone: it might first get you into a SOC or sysadmin job, where you then practice skills (maybe in a lab or CTFs on the side) to pivot into penetration testing. In summary, Security+ establishes your credibility and understanding of security basics, which you can then build on to land that first ethical hacking gig.
Honorable Mention: Help Desk / Technical Support (as a Foot-in-the-Door)
It’s worth noting that not everyone lands a dedicated security job right after earning Security+. Sometimes, your Security+ can help you get hired in a more general IT support role (Help Desk, Technical Support) that has the potential to lead into security. Entry-level IT support roles involve handling user issues, managing accounts, and troubleshooting IT problems. How does Security+ help here? Firstly, it sets you apart from other help desk candidates by showing you have extra knowledge – you might get tasked with security-related tickets or trusted with admin permissions sooner. Secondly, a lot of security incidents start as IT support issues – for example, a user reports “weird pop-ups on my PC” (which could be malware) or “I think I clicked a bad link.” With Security+ training, you can recognize these red flags and take proper action (disconnecting the machine, not just reinstalling software blindly). Some help desk jobs even explicitly prefer Security+ so that their support staff can handle basic security troubleshooting. More importantly, help desk can be a springboard: after 6–12 months proving yourself and with Security+ under your belt, you could transition internally to the security team or a junior admin role. Many professionals have used this route – leveraging Security+ to move up from help desk to security analyst or sysadmin. So, while “Help Desk Technician” isn’t a cybersecurity job per se, your Security+ knowledge makes you more effective in that role and positioned to seize a cybersecurity opportunity when it arises.
Mid-Career Roles and Growth Paths After Security+
Once you have some experience in entry-level roles (and perhaps additional training), a whole new set of mid-career cybersecurity opportunities becomes attainable. Security+ is not the end of your certification journey – it’s the foundation. As you progress, you’ll likely specialize further or take on more responsibility. Let’s look at some mid-level roles that Security+ can lead to, and how you can grow into them:
Security Engineer
As you gain a few years of experience as an analyst or admin, you might advance to a Security Engineer role. Security Engineers are the professionals who design, build, and improve an organization’s security infrastructure. In this position, you move from simply using security tools to architecting solutions. For example, a security engineer might evaluate and deploy a new SIEM system or cloud security platform. They might design the network segmentation for a new corporate network, deciding where firewalls should go and how to configure them for maximum protection. Security engineers also develop secure configurations (for servers, applications, etc.) and sometimes build custom scripts or automation to support security monitoring. Essentially, you’re combining deep technical IT skills with security expertise to fortify the organization’s defenses.
Growth path & complementary certs: To become a security engineer, you’ll build on your Security+ knowledge with hands-on experience and often additional certifications. Many Security+ holders pursue CompTIA CySA+ (Cybersecurity Analyst) or CompTIA PenTest+ next, to deepen their technical skill set in defense or offense respectively. Vendor-specific certs can also help – e.g., learning a SIEM like Splunk (Splunk Certified Power User) or a firewall vendor cert (like Fortinet NSE or Cisco CCNP Security) can be valuable. If your goal is to design security solutions at an enterprise scale, eventually an (ISC)² CISSP certification (which is more advanced and management-oriented) can boost credibility. But in the mid-career phase, something like CompTIA CASP+ (Advanced Security Practitioner) or GIAC certifications might be more targeted to technical engineering skills. Security+ gives you the baseline; progressing to Security Engineer means continuously learning new technologies and staying updated on threats. The good news is that the broad base from Security+ (networking, system hardening, etc.) will continue to be useful as you architect complex systems. Many senior engineers say that having those fundamentals down from early in their career (certs like Security+) was key to their later success.
Incident Responder / Cybersecurity Analyst (Tier 2+)
If you started as a SOC analyst, one growth path is becoming a Senior Security Analyst or Incident Responder. These mid-level roles involve handling and leading the response to more complex security incidents (think major malware outbreaks, detected intrusions, or coordinated cyber-attacks). As an incident responder, you will perform deep-dive investigations into how an attack happened, contain the damage, eradicate the threat (e.g., remove malware, purge attacker accounts), and recover systems to normal operation. You’ll also likely perform digital forensics, analyzing compromised machines or logs to trace the attacker’s steps and gather evidence. This is a challenging but exciting field – you’re essentially the firefighter of the cyber world, rushing in when everyone else is panicking.
Growth path & complementary certs: Growing into an incident response role often requires demonstrating strong analytical skills and possibly specializing. You might take training in digital forensics (for example, earning a GIAC GCFA or GCFE certification) or in incident handling (GIAC GCIH). Many incident responders also pursue the Certified Incident Handler (ECIH) or even something like Certified Ethical Hacker, because understanding how attackers operate helps in responding to them. Security+ lays the groundwork by teaching you the incident response phases and basic forensics concepts; to reach mid-level, you’ll need to build on that with real-world practice responding to incidents (sometimes starting by assisting on incidents as a junior). Another useful certification at this stage is (ISC)² SSCP (Systems Security Certified Practitioner), which is like a junior CISSP focusing on operational security – it can complement Security+ by validating more hands-on operational security skills, relevant to incident response and advanced SOC work.
Security Consultant / Cybersecurity Consultant
As you accumulate expertise, you might choose to work as a Security Consultant, either internally (advising within one company) or externally (at a consulting firm serving clients). This role is about providing expert guidance to design and implement security solutions or policies. It’s somewhat akin to a freelance security engineer/analyst hybrid. As a consultant, you need a broad and deep understanding of security – which often starts with the breadth of knowledge from Security+. You could be doing risk assessments one week, then helping deploy an IDS the next, then conducting user security training after that. Flexibility and communication skills are key, as you’ll be writing recommendations and briefing management on risks.
Growth path & complementary certs: Security+ holders moving into consulting often bolster their credentials with management or audit-oriented certifications like CISM (Certified Information Security Manager) or CISA (Certified Information Systems Auditor) if they are advising on compliance and policy. If the consulting work is technical (say, advising on network security architecture), certs like CISSP (which covers a broad range of topics at a managerial level) or vendor certs for specific technologies can help. Soft skills training is also valuable – many consultants take courses in project management or ITIL for process knowledge. The Security+ certification remains a strong conversation starter with clients because it’s well-known; combined with a few years of experience and perhaps a higher-level cert, it demonstrates you have both theory and practice. In mid-career, security consultants can command high salaries (or bill rates) as they bring in-demand expertise to organizations that need guidance.
Information Security Manager / SOC Team Lead
For those who enjoy leadership, a mid-to-late career move is into management. Information Security Managers or Security Operations Center (SOC) Leads are examples where you might not be on the tools every day, but you’re overseeing security programs and teams. With a Security+ and technical background, you understand what your team is doing, which makes you an effective leader who can bridge the gap between upper management and technical staff. In these roles, you’ll be developing security strategies, prioritizing projects (like “we need to implement multi-factor authentication this year”), ensuring compliance with regulations, and mentoring junior analysts/engineers. You’ll likely interface with other departments to coordinate security efforts and report on security posture to executives.
Growth path & complementary certs: Climbing into management usually necessitates broader experience and credentials that demonstrate strategic understanding. After Security+, many pursue CISSP once they have the required experience (CISSP covers management, risk, law, etc., and is often seen as a must-have for security managers). Others might earn CompTIA CASP+ as a technical but high-level cert, or CRISC (for risk management). An MBA or degrees in cybersecurity management can also come into play. The key is, Security+ gave you the technical cred early on; to be a manager, you combine that with big-picture skills. It’s motivating to note that some CISOs (Chief Information Security Officers) started out with humble certifications like Security+ and built on them – everyone starts somewhere, and Security+ is a common first step towards the top of the ladder.
Other Niche/Specialist Roles
Cybersecurity is a vast field, and Security+ can be the jumping-off point for many specialized mid-career roles depending on your interests. For example, you could become a Vulnerability Analyst (finding and managing vulnerabilities in systems), a Cyber Threat Intelligence Analyst (researching threat actors and techniques to inform defenses), a Digital Forensics Analyst (specializing in investigating breaches and computer crimes), or a Cloud Security Engineer (securing cloud environments for organizations). You might also move into fields like Cybersecurity Auditor or GRC (Governance, Risk, and Compliance) Specialist, ensuring companies follow security standards and regulations. Security+ provides the baseline knowledge of threats, controls, and risk that underpins all these niches. To move into them, you would pair your on-the-job experience with targeted learning (for instance, taking cloud computing courses for a cloud security role, or legal/privacy courses if you’re interested in compliance). The nice thing is, Security+ doesn’t lock you into one track – it’s respected in all these areas as a sign of your security fundamentals, so you can pivot as opportunities arise.
Certifications to complement Security+: In summary, as you grow, consider certs like CySA+ (focus on defense/operations), PenTest+ (offense), CASP+ (advanced practitioner), CISSP (management/leadership), CISM/CISA (management and audit), CEH/OSCP (penetration testing), Cloud security certs (like AWS Certified Security Specialty, CCSP, or CompTIA Cloud+) for cloud roles, and vendor certifications for any specific technologies you work with (Cisco, Microsoft, etc.). Each of these builds on the base that Security+ gave you. The combination of experience + Security+ + one or two higher-level certs can make you a strong candidate for mid-level roles in the cybersecurity job market.
Salary Ranges for CompTIA Security+ Jobs in the U.S.
What kind of salary can you expect in these Security+ related roles? Salaries vary based on location, experience, and company size, but below is an overview of typical U.S. salary ranges (from entry-level up to experienced) for common job titles where Security+ is either required or beneficial. These figures can give you a ballpark idea of earnings potential:
| Job Role | Typical U.S. Salary Range |
|---|---|
| Systems Administrator | ~$55,000 – $145,000 per year |
| Network Administrator | ~$57,000 – $124,000 per year |
| Security Analyst (SOC) | ~$58,000 – $143,000 per year |
| Security Engineer | ~$49,000 – $143,000 per year |
| Security Consultant | ~$51,000 – $171,000 per year |
| Penetration Tester | ~$86,000 – $186,000 per year |
Table: Approximate salary ranges for Security+ related roles (low end represents entry-level positions, high end represents experienced professionals in that role).
A few observations from the data:
- Entry-Level Positions: Roles like systems or network administrator and junior security analyst often start in the $50k–$70k range for entry-level in many regions. If you’re just starting out with Security+, expect your initial salary to be toward the lower end of these ranges. For example, an entry-level SOC analyst in a small city might earn around $60k, whereas one in a major metro or with some experience could be closer to $80k.
- Growth with Experience: The high-end figures (e.g. $100k+ for admins, $140k+ for analysts) reflect what you can earn with years of experience or in senior positions. Security+ alone won’t instantly get you a six-figure salary, but it sets you on a path where that becomes possible after you move into mid-level roles. For instance, Security Engineers, Consultants, and experienced Penetration Testers often break into six figures as seen in the table. The cybersecurity field overall has a strong earning trajectory, especially as you climb into roles requiring high expertise.
- Role Variability: Notice Penetration Testers have a higher starting point in the table (~$86k). This is because pure pen testing roles typically require more specialized skills; thus, even a “junior” pen tester might command a higher salary than a junior analyst. However, there are fewer of those jobs available at entry level. On the other hand, roles like Security Consultant have a wide range – some may start relatively modest if you’re consulting in a smaller domain, but highly experienced consultants (especially contractors) can earn very high, reflected in the upper range.
- Regional Differences: These ranges are national averages. In lower cost-of-living areas or for smaller companies, salaries might skew toward the lower end. In tech hubs (San Francisco, New York, DC, etc.) or for roles in high-demand sectors (finance, defense), salaries often hit the upper end or even exceed these ranges. For example, the U.S. Bureau of Labor Statistics noted that information security analysts median salary was around $100k and rising, with top earners (90th percentile) making $150k+ in 2023 – which aligns with the higher end for security analysts in our table.
Remember, salary is not everything – especially in the beginning. Gaining experience and skills will quickly increase your market value in cybersecurity. Security+ gives you a foot in the door; once inside, your growth potential (including salary growth) is substantial. Always research your local job market and use resources like salary websites or networking with professionals to gauge what you should be aiming for given your situation.
How to Land a Job with Security+ (Even With Little Experience)
Having the Security+ certification is a powerful asset on your resume, but how do you actually land that first job – particularly if you don’t have much hands-on experience yet? Here are some actionable tips to jumpstart your cybersecurity career with Security+:
1. Leverage Your Security+ on Your Resume and LinkedIn: Make sure to highlight your Security+ cert prominently. Mention it in your resume summary (“CompTIA Security+ certified aspiring cybersecurity analyst”) and list it in the certifications section. On LinkedIn, add the certification badge. This increases the chance of recruiters finding you since many will search for Security+ as a keyword when filling entry roles. Also, emphasize Security+-related skills you learned – e.g., network security, risk assessment, incident response – in your skills section. This shows that you not only passed an exam but also understand key concepts employers care about.
2. Build a Home Lab or Practical Portfolio: One way to overcome “lack of experience” is to create your own experience. Set up a home lab environment where you can practice the skills Security+ covers. For instance, you can install VirtualBox or VMware and create a small network: a Windows server, a Linux machine, maybe Security Onion (a free SIEM/IDS) and try monitoring traffic, or an vulnerable web app to practice securing it. Document what you do – this can become a talking point in interviews or even a small portfolio project you share on a blog or GitHub. For example, you could write a short report on “Hardening an Ubuntu server step-by-step” or “What I found after running Wireshark on my home network for a day.” These activities show initiative and practical skill, bridging the gap from book knowledge to real-world application. Even a simple project like configuring a pfSense firewall for your home and explaining the rules you set up can impress hiring managers.
3. Target Entry-Level Roles and Emphasize Willingness to Learn: When job hunting, look for titles like “Security Analyst I, Information Security Associate, Junior Cybersecurity Engineer, IT Security Specialist – Entry Level” and so on. Don’t overlook IT support roles that mention security either. In your application and interviews, be honest that you’re starting out but showcase your passion and continuous learning. Talk about labs you’ve done, news or security blogs you follow, or any volunteer tech support you’ve done – anything that demonstrates you’re not just collecting certs, you’re truly interested in security. Employers often value attitude and aptitude over specific experience for junior roles. Make it clear that you’re eager to learn on the job and have the foundational knowledge (backed by Security+) to ramp up quickly.
4. Network with Professionals and Join Communities: Getting involved in the cybersecurity community can open doors that applying online never will. Join local cybersecurity meetups or groups – many cities have an ISSA chapter (Information Systems Security Association) or meetup.com groups for cyber professionals. There are also online communities (on platforms like Discord, Reddit r/CompTIA or r/cybersecurity, etc.) where you can learn about job opportunities. When you attend events or participate in discussions, don’t be shy to mention you’re Security+ certified and looking for an entry role – you might get referrals or at least advice. Consider attending (or volunteering at) security conferences like BSides, which often have career tracks or job fairs. Also, engage with people on LinkedIn: a polite message expressing interest in their company and asking for advice can sometimes lead to informational interviews or referrals. Remember, referrals are gold in job searching.
5. Gain Related Experience (Internships, Volunteer, or Part-time): If you’re really struggling to land a paid role initially, seek out internships or volunteer opportunities. Many nonprofits or small businesses would be happy to have someone help part-time with IT/security in exchange for experience. For example, you could volunteer to help a local charity with their IT setup – secure their Wi-Fi, set up backups, etc. – apply your Security+ skills in a low-stakes environment. Similarly, an internship (even if you’ve already graduated, some places offer “early career” internships) at a company’s IT or security department can be a foot in the door. Even a few months of real-world experience will make your resume far stronger. Pair that with your Security+ and you’ll be much more likely to get hired full-time. If an internship isn’t feasible, consider freelancing small gigs on platforms like Upwork – there are often gigs for things like “conduct basic security assessment” or “help configure a firewall” that, if you feel capable, can both earn you a bit and give experience.
6. Prepare for Technical Interviews: With Security+, you can expect interviews for security roles to test your fundamental knowledge. Be ready for questions like “What is the difference between TCP and UDP?”, “How would you secure a server?”, “Explain what a SQL injection is,” or scenario questions (“If a user reports a phishing email, what would you do?”). Review the Security+ objectives and ensure you can talk about them confidently and applied to real situations. It’s one thing to recall a term, it’s another to explain how it matters to a business. Practice answering in a structured way: define the concept, then give a quick example. Additionally, some interviews might have a practical portion or case study – they might ask how you’d respond to a mock incident. Use your Security+ study experience: remember the steps of incident response (Preparation, Identification, Containment, Eradication, Recovery, Lessons Learned) and apply them to the scenario. Showing a calm, methodical approach can set you apart as a candidate who knows the proper process even if you haven’t lived through it yet.
7. Continue Learning and Show Initiative: The tech field loves self-starters. While job searching (and even after you land a job), keep learning and maybe even start another certification. For instance, some people go for CompTIA Network+ or Linux+ either before or after Security+ to strengthen general IT skills; others might start CompTIA CySA+ to show they’re aiming for analyst roles. Even if you don’t complete another cert immediately, mention in interviews that you’re studying topic X or working on Y project. This signals that you won’t stagnate and that you’ll grow in value over time. Employers hiring entry-level folks often worry if the person will require a lot of hand-holding – by demonstrating that you can teach yourself and stay motivated (as evidenced by you getting Security+ on your own and pursuing further knowledge), you alleviate that concern.
In summary, Security+ gets you noticed, but you must take initiative to get hired. Combine the certification with hands-on practice, networking, and a proactive attitude, and you will significantly increase your chances of landing that first cybersecurity job. Many before you have started exactly where you are and successfully launched careers – you can absolutely do it too.

















Comments