How to Sign Up for the PMP Exam? Guide to the Application Process
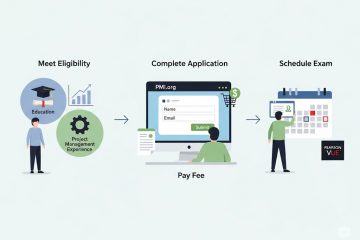
The Project Management Professional (PMP)® certification, offered by the Project Management Institute (PMI)®, is a globally recognized and highly respected credential for project managers. While the exam itself is rigorous, the journey to certification begins long before test day—it starts with a meticulous and accurate application process. This guide provides an expert-level, step-by-step walkthrough to... » read more