- Routing protocols, including OSPFv2 for IPv4, OSPFv3 for IPv6, EIGRP for IPv4, and EIGRP for IPv6
- VLANs, STP, and EtherChannel (static, PAGP, and LACP)
- WAN technologies, such as PPP, MLPPP, PPPoE, and GRE
- Quality of server (QoS), including marking, shaping, and prioritization of voice, video, and data
- 1 months of unlimited access to video courses
- Flexible online learning
- 6 months of unlimited access to video courses
- Flexible online learning
- 100% Money back guarantee
- 6 months of unlimited access to video courses
- 100% Real CCNA Practice Exam-Same with Latest CCNA Test
- Flexible online learning
- 100% Money back guarantee
Free Demos
For any network administrator using this training for exam preparation, our CCNA course maps to the Cisco 200-301 CCNA exams objectives, and covers topics such as:
After taking this CCNA course, you'll be ready to take the 200-301 CCNA, and validate the entry-level skills expected of a network administrator. For anyone who manages network administrators, this training can be used for 200-301 CCNA exam prep, on-boarding new network administrators, or as part of a team training plan. Salary and Job Opportunities: The average annual pay for a CCNA in the United States is $84,376 a year.
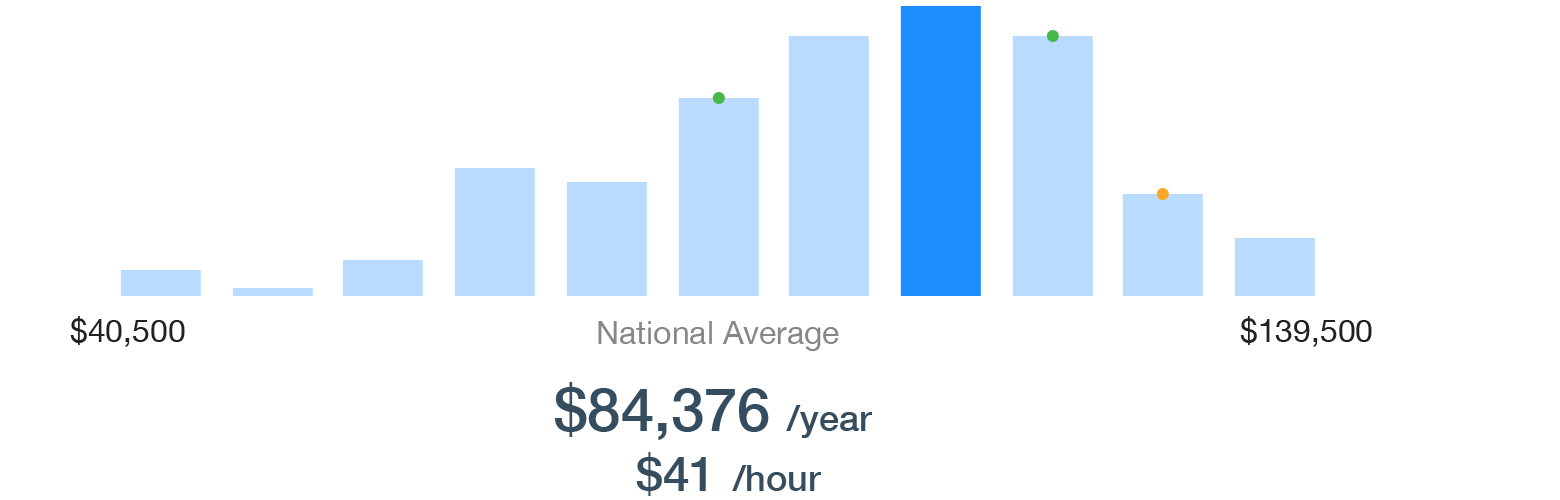
Stay Competitive
99% of organizations surveyed use technical certifications to make hiring decisions.
91% of employers believe IT certifications are a reliable predictor of a successful employee.
81% of employers associate IT certification holders with increased quality and value of work contribution.
Course content
Christian Valentino


Student feedback
4.9
Course rating
Reviews
Thejashree Chan
Khairul
Arontm